Modifying/Adding Security Group Rules
Last updated: 2025-11-24 21:33:21
Security groups are used to manage traffic to and from public and private networks. For the sake of security, most inbound traffic is denied by default, but you can modify and add security group rules as needed. This document describes how to modify and add security group rules in the console.
Prerequisites
You have created a security group. For more information, see Configuring Security Group .
You have learned about which traffic is allowed or denied for your CVM instance. For more information on security group rules and their use cases, see [Security Group Use Cases] (https://www.tencentcloud.com/document/product/213/32369).
Modifying Security Group Rules
1. Log in to the CVM console and go to the Security Group page, find the created target security group, and click Modify Rule in the Operation column.
2. On the security group rule page, select inbound or outbound rules by clicking Inbound rules or Outbound rules.
3. Locate the desired rule and click Edit to modify it.
Adding Security Group Rules
1. Log in to the CVM console and go to the Security Group page, find the created target security group, and click Modify Rule in the Operation column.
2.
On
the security group rule page, click Inbound Rules > Add Rule.3. In the pop-up dialog box, set the rule.
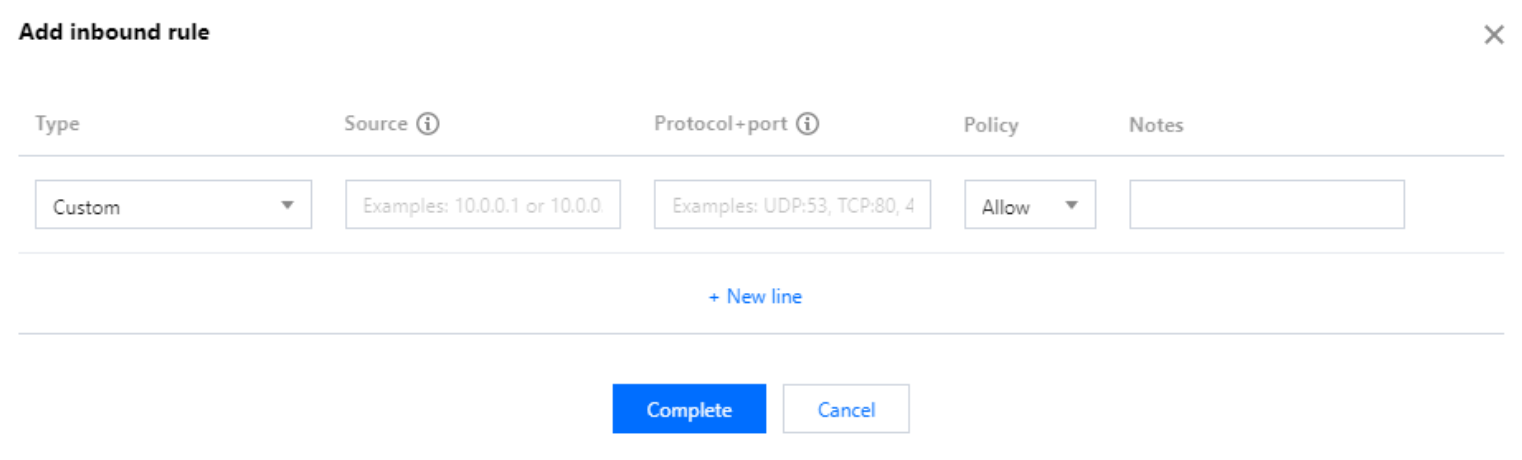
Type: Custom is selected by default. You can also choose another system rule template, such as Windows Login template, Linux Login template, Ping template, HTTP(80) template, HTTPS(443) template, MySQL(3306) template, and SQLServer(1433) template.
Source or Destination: traffic source (inbound rules) or target (outbound rules). You need to specify one of the following options:
Source | Specification |
IP address or CIDR IP range | Utilize CIDR notation (IPv4; such as 203.0.113.0, 203.0.113.0/24 or 0.0.0.0/0, where 0.0.0.0/0 signifies a match for all IPv4 addresses. IPv6: such as FF05::B5, FF05:B5::/60, ::/0 or 0::0/0, where ::/0 or 0::0/0 denotes a match for all IPv6 addresses). |
Parameter template - IP address | |
Parameter template - IP address group | |
Security group | To refer to a security group ID, you may refer to the ID of the following security groups: Current security group: This refers to the security group ID associated with the cloud database, presented in markdown format. Other security groups: This refers to another security group ID within the same project in the same region. Note: Referring to the security group ID is an advanced feature that you may opt to use. The rules of the referred security group will not be appended to the current security group. When security group rules are configured, if a security group ID is entered in the source/destination, it signifies that only the private IP addresses of the cloud database instances and elastic network interfaces bound to this security group ID are considered as the source/destination, excluding public IP addresses. |
Note:
The /number following the IP address denotes the subnet mask, of which the number signifies the length of the network portion in the subnet mask. For instance, 192.168.0.0/24 represents a network segment. The subnet mask /24 indicates that the first 24 bits of 192.168.0.0 are the network portion, and the remaining 8 bits are the host portion. Hence, within the 192.168.0.0/24 subnet, the assignable host IP range is: 192.168.0.0 - 192.168.0.255.
Protocol Port:Specify the protocol type and port range. The protocol type supports TCP, UDP, ICMP, ICMPv6, and GRE. You can also refer to the protocol ports or protocol port groups in the Parameter Template.
Note:
To connect to TDSQL-C for MySQL, you need to open its instance port. You can log in to the TDSQL-C for MySQL console, click the cluster ID to enter the details page, and view its port in the Connection Info section.
The security group rules displayed on the Security Group page in the TDSQL-C MySQL console take effect for private and public (if enabled) network addresses of the TencentDB for MySQL instance.
The supported formats for the protocol port are as follows:
A single port, such as
TCP:80.Multiple discrete ports, such as
TCP:80,443.Consecutive ports, such as
TCP:3306-20000.All the ports, such as
TCP:ALL.Policy: Allow or Reject. Allow is selected by default.
Allow: Traffic to this port is allowed.
Reject: Data packets will be discarded without any response.
Notes: A short description of the rule for easier management.
4.
Click Complete
5. On the security group rule page, click Outbound rule and refer to Steps 2-4 for adding an outbound rule.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

