Web Security Monitoring Alert
Last updated: 2025-07-28 16:42:21
Overview
Web security monitoring rules can provide you with real-time, customized security event notifications, and support Webhook shipping, seamlessly integrating alarms with common enterprise communication tools, improving security operation efficiency, and helping you quickly discover and respond to potential risks. You can flexibly configure the monitoring range, threshold, and alarm frequency based on your business needs and risk assessment.
Configuration Item Description
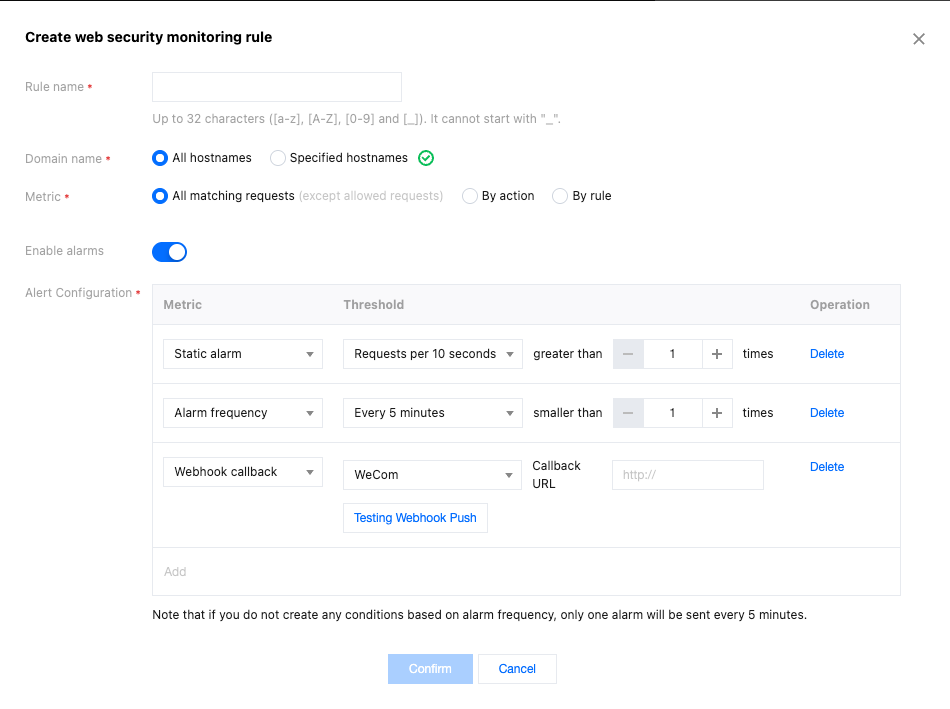
Configuration Item | Description | |
Rule name (Required) | | Must meet the following requirements: A combination of letters, digits, and underscores; Less than 32 characters; Cannot start with an underscore. |
Domain name (Required) | | All domains: Includes all domains under this site, including domains added later. Specified domains: Only monitors specific domains under this site. Note: Threshold statistics are only effective for individual domains and will not merge the number of requests within multiple domains. |
Metric (Required) | | Supports selecting the statistical request range by action or by rule. All action requests: All requests that hit the security module rules and are processed (excluding allowed), are counted in the monitoring rule statistics. Only count requests with specified action: Requests that hit Web protection or Bot management rules and are ultimately processed in the selected way, are counted in the monitoring rule statistics. Only count requests that hit specified rule: Requests that hit specified Web protection or Bot management rules. Note: Allowing will not record logs, so it will not be included in monitoring statistics. |
Alert switch | | Controls whether this Web security monitoring rule is effective. When the alarms switch is enabled, alarms will be sent through the message push channels provided by the Message Center (Message Center/Email/SMS/WeChat/Voice/WeCom Service Account). The specific message push channels can be configured in the Message Center Console. When the alarms switch is disabled, this Web security monitoring rule will no longer send alarms, including Message Center-related channels and Webhook push. Note: EdgeOne Web security monitoring alarm messages correspond to the "Security Event Notification" type messages in the Message Center. |
Alarm setting | Static alarm (Required) | Supports configuring the threshold quantity of requests reached within a specified time window. When the specified threshold is reached, an alarm is triggered. |
| Alarm frequency (Optional) | Configure the frequency of pushing alarms. When not custom configured, the default is up to 1 alarm notification every 5 minutes for each rule. |
| Webhook push (Optional) | In addition to the message push channels provided by the Message Center, an additional Webhook interface callback method is provided. Currently supported channels include WeCom, Lark, DingTalk, and custom interface callback. After filling in the Webhook address for the corresponding channel, you can click Test Webhook Push, and EdgeOne will push a test message to the address you filled in to verify connectivity. The message content template is defined using Go text/template syntax and supports referencing Web security monitoring-related variables using {{.Notification Variables}}. For details, see Webhook Message Content Template. |
Scenario 1: Monitor site for CC attack events and alert within 5 minutes
A financial business site needs to quickly respond within 5 minutes to meet regulatory compliance requirements when the business domain
www.example.com is under CC attack. Therefore, the site's CC attack events are monitored. When the site is attacked by more than 5000 QPS CC attacks, an alarm is pushed to the security operations team for processing within 5 minutes.1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. On the site details page, click Security and Acceleration > Alert Notification Push to enter the alert notification push details page.
3. In the Web security monitoring rules card, click Set to enter the rule management page.
4. Click Add rule and configure the corresponding alert rule. In this scenario, after entering the rule name, select the monitoring domain as
www.example.com, the monitoring metric as high-frequency access request limit, intelligent client filtering, and slow attack protection events in CC attack defense. When the number of CC attacks exceeds 50,000 within 10 seconds, an alarm is triggered immediately and sent through the notification channels configured in the Message Center Console.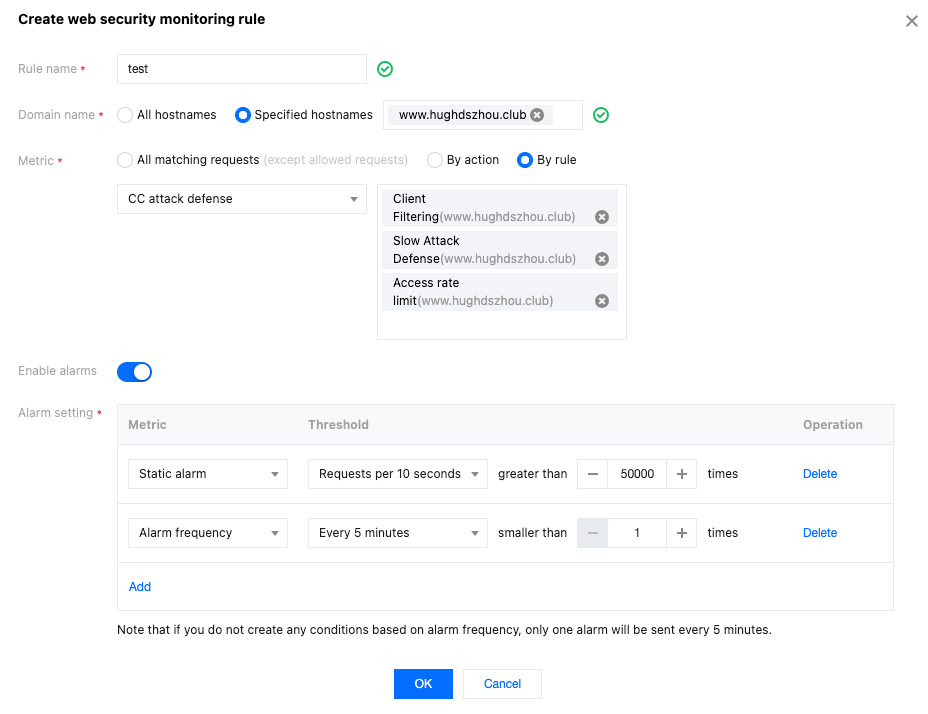
5. Click OK to complete the configuration.
Scenario 2: Monitor requests suspected of vulnerability attacks that hit managed rules and push Webhook alarms
The domain name of a company's official website that has been connected is
www.example.com. The site contains sensitive customer information and needs to be constantly monitored for SQL injection-type vulnerability attacks. When any request hits the Web-managed rules for SQL injection attack defense, an alarm needs to be triggered immediately and pushed to the Enterprise WeChat robot via Webhook for further analysis.1. Log in to the Tencent Cloud EdgeOne console, enter Service Overview in the left menu bar, and click the site to be configured under Website Security Acceleration.
2. On the site details page, click Security Protection > Alert Notification Push to enter the alarm notification push details page.
3. In the Web security monitoring rules card, click Set to enter the rule management page.
4. Click Add rule and configure the corresponding alarm rule. In this scenario, after entering the rule name, select the monitoring domain as
www.example.com, the monitoring metric as requests hitting managed rules for SQL injection attack defense, and when the number of requests exceeds 1 within 10 seconds, an alarm is triggered immediately and sent through the notification channels configured in the Message Center Console, as well as pushed to the specified URL via Webhook.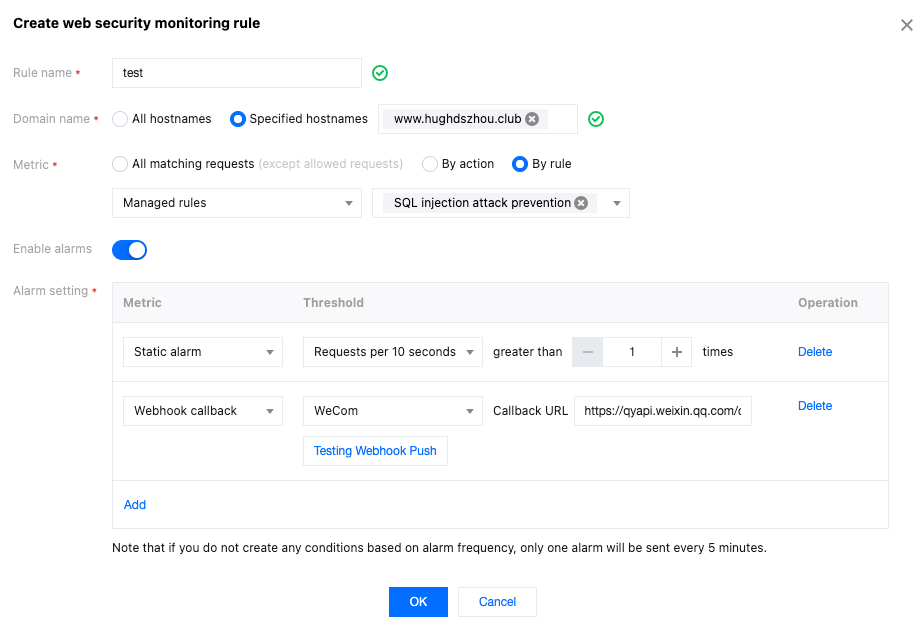
5. Click OK to complete the configuration.
Related References
Webhook Message Content Template
The message content template is defined using Go text/template syntax and supports referencing Web security monitoring-related variables using
{{.Notification variables}}. The default message content template is as follows:Notification Type: Site Security Monitoring NotificationAccount ID: {{.UIN}}Nickname: {{.AccountName}}Site Name: {{.Zone}}Monitoring Object: {{.Object}}Monitoring Rule Name: {{.AlertRule}}Alarm Time: {{.StartTime}} (GMT +8:00)Alarm Condition: {{.Condition.TimeSpan}} seconds with more than {{.Condition.Threshold}} requestsMonitoring Item Metrics: {{.Condition.TimeSpan}} seconds with {{.MetricValue}} requests
Notification Variable Name | Data Type | Variable Meaning |
UIN | String | Tencent Cloud Account ID |
AccountName | String | Tencent Cloud Account Nickname |
Zone | String | EdgeOne Site Name |
AlertRule | String | Alarm Policy Name |
Object | Array of String | |
JSON object | ||
StartTime | String | Alarm Trigger Time. The default timezone is UTC+8, example value: 2024-01-08 18:00:40 |
MetricValue | Integer | Alarm Trigger Metric Value |
Note:
Currently, the console does not support self-service modification of message content templates. If you have related needs, please contact us.
Condition Object Structure
key Name | value Meaning |
TimeSpan | User-configured alarm time window |
Threshold | User-configured static threshold for the number of requests |
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No
Feedback

