Bot 智能分析
最后更新时间:2025-07-28 16:25:02
功能概述
Bot 智能分析旨在帮助您快速识别并区分人类用户和自动化程序(Bot)的请求,该功能适用于以下业务场景:
业务面临 Bot 攻击、活动刷量、流量盗刷等威胁,短时间内无法完成精准的 Bot 防护策略配置与调优,需要快速压制非人类用户请求的业务场景。
需要快速部署,识别并分析网站流量模式,了解整体访客情况的业务场景。
Bot 智能分析基于聚类分析算法和大数据模型的智能引擎,通过对请求的多个因素进行综合评估,将请求分类为正常人类请求、正常 Bot 请求、疑似 Bot 请求以及恶意 Bot 请求。您可以根据 Bot 分析结果,对不同类型的请求配置相应的处置方式,如拦截、JavaScript 挑战、观察和放行。
说明:
Bot 智能分析综合了 Bot 基础特征管理和客户端画像分析功能中的请求特点,并结合动态聚类分析,形成请求风险标签。Bot 智能分析可以帮助您了解整体访客情况并快速部署Bot管理策略。如您对于请求特征有非常明确的策略要求(例如:放行特定搜索引擎请求、拦截Web开发工具请求等),您可以进一步使用 Bot 基础特征管理、客户端画像分析和自定义 Bot 规则进行策略调整。
策略机制
Bot 智能分析采用基于规则的策略机制,由静态规则和动态规则两部分组成:
静态规则基于预先定义的特征库,包含部分自动化工具(如 cURL、Python)的黑名单特征,如用户代理(User-Agent)和指纹等。静态规则在单次请求中触发即生效,规则有效期为永久。
动态规则根据实时的流量特征和请求行为自动生成。例如,当前域名的请求量在短时间内(约 5 分钟)超过一定阈值(约 100 次)时,系统会自动触发动态规则的生成和部署,动态规则有效期为 20 分钟,可以捕获未知的 Bot 行为。
Bot 智能分析的策略按照域名维度生效,不同域名的流量互不影响。对于同一个域名,可能存在多条静态规则和动态规则同时生效的情况,当一个请求同时命中多条规则时,系统会根据规则的权重和置信度对请求打上相应的标签,如恶意 Bot、疑似 Bot、友好 Bot 等,并根据客户预先配置的处置动作对请求进行相应处理。
通过静态规则和动态规则的有机结合,Bot 智能分析可以全面覆盖已知和未知的 Bot 威胁,同时降低规则维护的复杂度,让客户以最低的时间成本获得有效的Bot 防护能力。
操作步骤
例如:电商站点
shop.example.com 发现商品展示页面访问用量突增,判断可能遭受了大量的 Bot 访问,通过 Bot 智能分析策略可快速启用 Bot 管理功能对 Bot 工具进行拦截。您可以参照以下步骤操作:1. 登录 边缘安全加速平台 EO 控制台,在左侧菜单栏中,进入服务总览,单击网站安全加速内需配置的站点。
2. 单击安全防护 > Web 防护。默认为站点级防护策略,单击域名级防护策略 Tab,在域名级防护策略中,单击目标域名进入目标域名防护策略配置界面,例如:
shop.example.com。3. 定位到 Bot 管理卡片,单击 Bot 智能分析下方的编辑,进入配置页面。
4. 配置各 Bot 分析标签的相应处置方式。以当前场景为例,可配置恶意 Bot 请求的处置方式为 JavaScript 挑战,疑似 Bot 请求和友好 Bot 请求保持为观察即可。
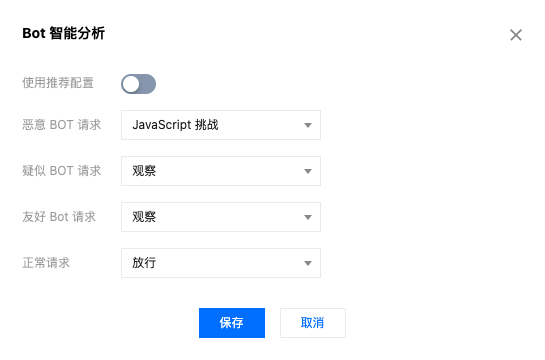
5. 单击保存,完成配置。
查看命中 Bot 智能分析的流量
要查看命中 Bot 智能分析规则的流量:
1. 登录 边缘安全加速平台 EO 控制台,在左侧菜单栏中,单击Web 安全分析。
2. 单击添加筛选,选择 Bot 管理 - Bot 智能分析,支持根据规则 ID、Bot 标签、Bot 智能分析特征进行筛选。
3. 单击确定,应用筛选条件,在统计趋势和统计详情处观察防护效果。
使用限制及处理方案
Bot 智能分析旨在区分人类用户和自动化程序的请求,在某些特定的业务场景下可能存在使用限制:
合法自动化请求访问:对于允许通过自动化请求访问的业务,例如性能监控使用到的定期拨测、通过第三方工具或组件调用 API 访问等,Bot 智能分析可能将其误判为恶意 Bot 请求。在这种情况下,建议配置防护例外规则绕过 Bot 智能分析防护模块,避免误拦截。同时结合自定义 Bot 规则,增强防护能力。
多 CDN 或代理场景:如果业务在 EdgeOne 前部还嵌套使用了其他 CDN 或代理服务,可能会导致请求的真实来源 IP 信息丢失,从而影响 Bot 智能分析的判断准确性。在这种情况下,建议仔细评估现有的业务架构,并根据需要调整 EdgeOne 的部署位置,确保能够获取到准确的请求来源信息。
APP 场景:对于移动应用(APP)业务,由于不同用户的使用环境和行为差异较大,部分 APP 内置的开发组件或客户端(如游戏的热更新功能)发出的请求可能会被误判为 Bot。在这种情况下,建议配置防护例外规则,将特定 APP 请求添加到白名单中,避免影响正常用户的使用体验。
高级 Bot 对抗场景:在 Web 场景下,对于一些高级 Bot,如已经伪造 JA3 指纹的脚本工具、无头浏览器等,仅依靠流量特征分析可能无法有效识别。在这种情况下,建议启用Bot 主动特征识别功能,实现更精准的 Bot 鉴别。
极高对抗场景:对于使用指纹浏览器、真机操作、录屏操作等手段的极端情况,建议结合自定义 Bot 规则,采取托管挑战处置方式,通过下发验证码提升恶意攻击者的对抗成本,保护业务安全。
相关参考
请求的 Bot 标签
Bot 智能分析根据分析结果,将请求分类成下列类型:
恶意 Bot 请求:高度疑似来自恶意自动化程序的请求,风险较高,建议配置为拦截或者挑战处置动作。
疑似 Bot 请求:疑似来自自动化程序的请求,有一定风险,建议至少配置为观察或者挑战处置动作。
正常 Bot 请求:来自合法爬虫(如搜索引擎爬虫)的请求。
正常请求:客户端不具备明显 Bot 特征的请求,仅支持放行处置方式。
影响 Bot 智能分析判定的相关因素
Bot 智能分析引擎基于多维度特征和行为分析,对各个要素的风险进行综合评估和打分。主要影响因素如下:
1. 请求速率:基于全网流量审计建立的 IP 流量基线,对特定 IP 的访问频率进行异常检测。高频或异常的请求频率特征会被赋予较高的风险分数。
2. IP 情报库:引擎将引用全面的 IP 情报库,通过评估客户端 IP 的历史行为、信誉度和潜在风险,识别已知的恶意行为记录或黑名单信息。
3. 搜索引擎特征:结合搜索引擎厂商公开的爬虫 IP 列表和对应的 User-Agent 特征,系统能够准确识别和验证来自谷歌、百度等合法搜索引擎的爬虫请求。满足合法爬虫特征的请求会被赋予正常请求标签。
4. 访问 URL 序列:分析访客的 URL 访问顺序和模式,识别异常的浏览行为,以定位类似蜘蛛池爬虫、自动扫描工具等行为。具有恶意特征的行为序列会被赋予较高的风险分数。
5. JA3 指纹注1:利用 JA3 指纹技术识别客户端 TLS 连接的特征,识别非常规访问工具,如 Python 脚本、curl、headless 浏览器等。来自异常客户端或特定工具的请求会被赋予较高的风险分数。
6. 客户端一致性校验:系统验证流量特征与 User-Agent 中声明的浏览器和操作系统信息是否一致。特征不一致通常表明客户端被伪造,这类请求会被赋予较高的风险分数。
7. 代理 IP 识别:通过分析流量特征,实时检测基于 VPN、代理或本地拨号等技术的高频 IP 切换行为。符合秒拨 IP 特征的请求会被赋予较高的风险分数。
8. 客户端指纹注2:通过分析 HTTP 头部特征指纹,对比已知高危客户端指纹库,识别来自僵尸网络的恶意爬虫行为
说明:
注1:
JA3是一种针对 TLS 客户端握手过程中的特征进行指纹生成的方法(具体算法参考:JA3 指纹)。通过收集客户端在TLS握手过程中提供的信息(如支持的加密套件、扩展等),生成一个唯一的哈希值作为指纹。JA3指纹可以帮助我们识别出使用特定工具或库发起请求的客户端,例如使用 Python 库发起的请求。通过对比客户端的JA3指纹与已知的恶意工具或库的指纹,我们可以更准确地识别潜在的恶意Bot行为。
注2:
BotnetID 是一种基于 Bot 网络行为特征的识别方法。Bot 网络(Botnet)通常由多个被控制的恶意设备组成,它们可能用于发起攻击或执行其他恶意活动。通过分析客户端行为特征及其与已知 Bot 网络的相似性,可以生成一个 BotnetID。通过对比客户端的 BotnetID 与已知的恶意 Bot 网络 ID,我们可以更准确地识别潜在的恶意 Bot 行为。文档反馈

