Mutual Authentication
Last updated: 2024-11-08 15:55:01
Overview
HTTPS mutual authentication, also known as mutual TLS (mTLS) authentication or client authentication, is a secure communication protocol that requires both the server and the client to verify the identity of the opposite side. For standard HTTPS, the server proves its identity to the client (through a server certificate) in most cases, thereby establishing a secure, encrypted communication channel. On this basis, mutual authentication further requires the client to provide a certificate for the server to verify the client identity. This method is often used in systems with high security requirements to ensure both communication parties are trustworthy.
Preparations
One server certificate, consisting of server.pem and server.key;
One client certificate, consisting of client.pem and client.key;
Root certificate: CA.pem. The certificate requires the complete certificate chain to be uploaded in advance to the Tencent Cloud SSL console. The certificate needs to include the complete certificate chain. For format requirements, refer to CA Certificate Format and Certificate Chain Specification.
Note:
If you have not purchased server certificates and client certificates yet, you can also refer to Using OpenSSL to Generate Self-Signed Certificates to generate self-signed certificates in a testing environment.
Use Limits
Currently, each domain name supports configuring only 1 client CA certificate and supports RSA, ECC, or SM2 national encryption algorithm certificates.
If the server is configured with a national encryption algorithm certificate, the client CA certificate must also be a national encryption algorithm certificate.
Directions
For example, you need to configure mutual authentication for the domain name
www.example.com, and the client CA certificate has been uploaded to the Tencent Cloud SSL console.1. Log in to the EdgeOne console, click Site List in the left sidebar, and then click the site you want to configure in the site list.
2. On the site details page, click Domain Name Service > Domain Name Management.
3. On the domain name management page, select the domain name to be configured with a certificate and click Edit in the HTTPS column. The HTTPS certificate configuration page will pop up. In mTLS configuration, enable Edge mTLS and select an existing client CA certificate to configure.
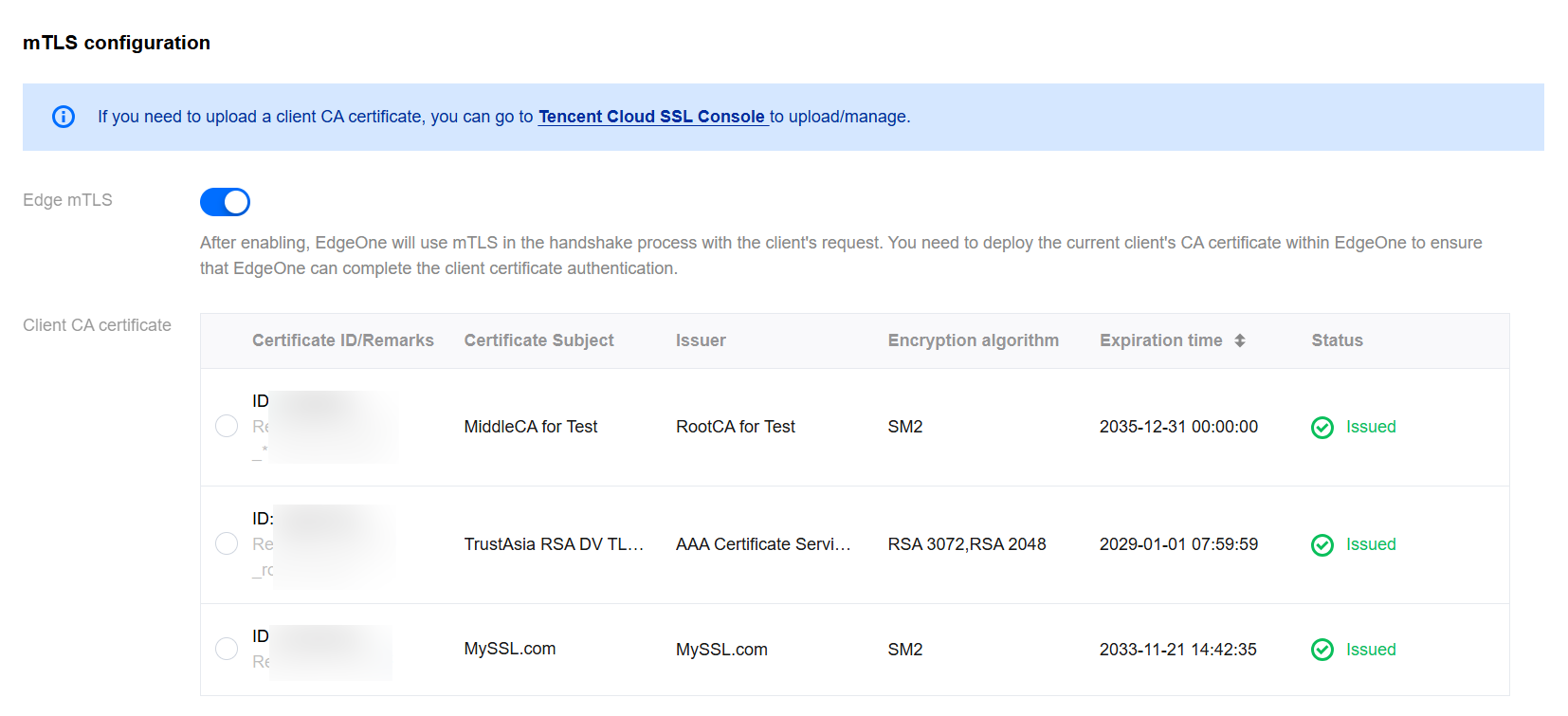
4. Click Confirm to issue the configuration. It will take effect immediately after the deployment is completed. After configuration, the client must carry the client certificate issued by the client CA certificate for access, otherwise the HTTPS handshake cannot be completed. You can also verify whether the handshake is successful by following the CURL command below to carry the client certificate information:
curl https://www.example.com --cert client.crt --key client.key -v -k
In this command, --cert indicates the local path of the client's public key certificate, and --key indicates the local path of the client's private key certificate.
FAQs
What Should I Do If An Error Is Reported During Testing with the Response Message: Empty Reply From Server?
In this case, the most common possibility is that the certificate chain of the currently configured client CA certificate is incomplete. You need to concatenate the complete certificate chain content together and upload it to the Tencent Cloud SSL console. The concatenation order needs to be in strict accordance with the CA Certificate Format and Certificate Chain Specification.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

