- Release Notes
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Network Security APIs
- AddAndPublishNetworkFirewallPolicyDetail
- AddAndPublishNetworkFirewallPolicyYamlDetail
- AddNetworkFirewallPolicyDetail
- AddNetworkFirewallPolicyYamlDetail
- CheckNetworkFirewallPolicyYaml
- ConfirmNetworkFirewallPolicy
- CreateNetworkFirewallClusterRefresh
- CreateNetworkFirewallPolicyDiscover
- CreateNetworkFirewallPublish
- CreateNetworkFirewallUndoPublish
- DeleteNetworkFirewallPolicyDetail
- DescribeNetworkFirewallAuditRecord
- DescribeNetworkFirewallClusterList
- DescribeNetworkFirewallClusterRefreshStatus
- DescribeNetworkFirewallNamespaceLabelList
- DescribeNetworkFirewallPodLabelsList
- DescribeNetworkFirewallPolicyDetail
- DescribeNetworkFirewallPolicyDiscover
- DescribeNetworkFirewallPolicyList
- DescribeNetworkFirewallPolicyStatus
- DescribeNetworkFirewallPolicyYamlDetail
- UpdateAndPublishNetworkFirewallPolicyDetail
- UpdateAndPublishNetworkFirewallPolicyYamlDetail
- UpdateNetworkFirewallPolicyDetail
- UpdateNetworkFirewallPolicyYamlDetail
- Cluster Security APIs
- CreateCheckComponent
- CreateClusterCheckTask
- CreateRefreshTask
- DescribeAffectedClusterCount
- DescribeAffectedNodeList
- DescribeAffectedWorkloadList
- DescribeCheckItemList
- DescribeRefreshTask
- DescribeRiskList
- DescribeTaskResultSummary
- DescribeUnfinishRefreshTask
- DescribeUserCluster
- SetCheckMode
- DescribeClusterDetail
- DescribeClusterSummary
- Security Compliance APIs
- AddComplianceAssetPolicySetToWhitelist
- AddCompliancePolicyAssetSetToWhitelist
- AddCompliancePolicyItemToWhitelist
- CreateComplianceTask
- CreateExportComplianceStatusListJob
- DeleteComplianceAssetPolicySetFromWhitelist
- DeleteCompliancePolicyAssetSetFromWhitelist
- DeleteCompliancePolicyItemFromWhitelist
- DescribeComplianceAssetDetailInfo
- DescribeComplianceAssetList
- DescribeComplianceAssetPolicyItemList
- DescribeCompliancePeriodTaskList
- DescribeCompliancePolicyItemAffectedAssetList
- DescribeCompliancePolicyItemAffectedSummary
- DescribeComplianceScanFailedAssetList
- DescribeComplianceTaskAssetSummary
- DescribeComplianceTaskPolicyItemSummaryList
- DescribeComplianceWhitelistItemList
- InitializeUserComplianceEnvironment
- ModifyCompliancePeriodTask
- ScanComplianceAssets
- ScanComplianceAssetsByPolicyItem
- ScanCompliancePolicyItems
- ScanComplianceScanFailedAssets
- Runtime security - High-risk syscalls
- Runtime Security - Reverse Shell APIs
- Runtime Security APIs
- AddEditAbnormalProcessRule
- DescribeAssetImageBindRuleInfo
- AddEditAccessControlRule
- AddEditRiskSyscallWhiteList
- CreateDefenceVulExportJob
- CreateEmergencyVulExportJob
- CreateProcessEventsExportJob
- CreateRiskDnsEventExportJob
- CreateSystemVulExportJob
- CreateVulContainerExportJob
- CreateVulImageExportJob
- CreateVulScanTask
- CreateWebVulExportJob
- DeleteAbnormalProcessRules
- DeleteAccessControlRules
- DescribeAbnormalProcessEventTendency
- DescribeAbnormalProcessEventsExport
- DescribeAbnormalProcessLevelSummary
- DescribeAbnormalProcessRuleDetail
- DescribeAbnormalProcessRules
- DescribeAbnormalProcessRulesExport
- DescribeAccessControlRuleDetail
- DescribeAccessControlRules
- DescribeAccessControlRulesExport
- DescribeEmergencyVulList
- DescribeSupportDefenceVul
- DescribeVulContainerList
- DescribeVulDetail
- DescribeVulImageList
- DescribeVulScanInfo
- DescribeVulScanLocalImageList
- DescribeWebVulList
- ModifyAbnormalProcessRuleStatus
- ModifyAbnormalProcessStatus
- ModifyAccessControlRuleStatus
- ModifyAccessControlStatus
- OpenTcssTrial
- StopVulScanTask
- DescribeAccessControlEventsExport
- DescribeAbnormalProcessDetail
- DescribeAbnormalProcessEvents
- DescribeAccessControlDetail
- DescribeAccessControlEvents
- DescribeRiskSyscallDetail
- Alert Settings APIs
- Advanced prevention - K8s API abnormal requests
- CreateAccessControlsRuleExportJob
- CreateK8sApiAbnormalEventExportJob
- CreateK8sApiAbnormalRuleExportJob
- CreateK8sApiAbnormalRuleInfo
- DeleteK8sApiAbnormalRule
- DescribeAssetClusterList
- DescribeK8sApiAbnormalEventInfo
- DescribeK8sApiAbnormalEventList
- DescribeK8sApiAbnormalRuleInfo
- DescribeK8sApiAbnormalRuleList
- DescribeK8sApiAbnormalRuleScopeList
- DescribeK8sApiAbnormalSummary
- DescribeK8sApiAbnormalTendency
- ModifyK8sApiAbnormalEventStatus
- ModifyK8sApiAbnormalRuleInfo
- ModifyK8sApiAbnormalRuleStatus
- Asset Management APIs
- CreateAssetImageScanSetting
- CreateAssetImageVirusExportJob
- CreateHostExportJob
- DeleteMachine
- DescribeABTestConfig
- DescribeAgentDaemonSetCmd
- DescribeAgentInstallCommand
- DescribeAssetSyncLastTime
- DescribeExportJobDownloadURL
- DescribeExportJobManageList
- DescribeInspectionReport
- DescribePromotionActivity
- DescribeTcssSummary
- DescribeUnauthorizedCoresTendency
- ModifyContainerNetStatus
- Security Operations - Log Analysis APIs
- CreateSearchTemplate
- DeleteSearchTemplate
- DescribeESAggregations
- DescribeESHits
- DescribeIndexList
- DescribeLogStorageStatistic
- DescribePublicKey
- DescribeSearchExportList
- DescribeSearchLogs
- DescribeSearchTemplates
- DescribeSecLogAlertMsg
- DescribeSecLogCleanSettingInfo
- DescribeSecLogDeliveryClsOptions
- DescribeSecLogDeliveryClsSetting
- DescribeSecLogDeliveryKafkaOptions
- DescribeSecLogDeliveryKafkaSetting
- DescribeSecLogJoinTypeList
- DescribeSecLogKafkaUIN
- ModifySecLogCleanSettingInfo
- ModifySecLogDeliveryClsSetting
- ModifySecLogDeliveryKafkaSetting
- ModifySecLogJoinState
- ModifySecLogKafkaUIN
- ResetSecLogTopicConfig
- DescribeSecLogJoinObjectList
- ModifySecLogJoinObjects
- Runtime Security - Trojan Call APIs
- CreateVirusScanAgain
- DescribeExportJobResult
- DescribeVirusAutoIsolateSampleDetail
- DescribeVirusAutoIsolateSampleDownloadURL
- DescribeVirusAutoIsolateSampleList
- DescribeVirusAutoIsolateSetting
- DescribeVirusEventTendency
- DescribeVirusManualScanEstimateTimeout
- DescribeVirusSampleDownloadUrl
- DescribeVirusScanTaskStatus
- DescribeVirusScanTimeoutSetting
- DescribeVirusSummary
- ExportVirusList
- ModifyVirusAutoIsolateExampleSwitch
- ModifyVirusAutoIsolateSetting
- ModifyVirusFileStatus
- ModifyVirusScanTimeoutSetting
- StopVirusScanTask
- DescribeVirusMonitorSetting
- DescribeVirusScanSetting
- ModifyVirusMonitorSetting
- ModifyVirusScanSetting
- DescribeVirusList
- DescribeVirusTaskList
- CreateVirusScanTask
- DescribeVirusDetail
- Runtime Security - Container Escape APIs
- DeleteEscapeWhiteList
- CreateEscapeWhiteListExportJob
- CreateEscapeEventsExportJob
- AddEscapeWhiteList
- DescribeEscapeEventTendency
- DescribeEscapeEventsExport
- DescribeEscapeRuleInfo
- DescribeEscapeSafeState
- DescribeEscapeWhiteList
- DescribeEscapeEventTypeSummary
- ModifyEscapeEventStatus
- ModifyEscapeRule
- ModifyEscapeWhiteList
- DescribeEscapeEventDetail
- DescribeEscapeEventInfo
- Image Security APIs
- AddAssetImageRegistryRegistryDetail
- AddEditImageAutoAuthorizedRule
- AddIgnoreVul
- CheckRepeatAssetImageRegistry
- CreateAssetImageRegistryScanTask
- CreateAssetImageRegistryScanTaskOneKey
- CreateAssetImageScanTask
- CreateComponentExportJob
- CreateImageExportJob
- CreateOrModifyPostPayCores
- CreateVulDefenceEventExportJob
- CreateVulDefenceHostExportJob
- CreateVulExportJob
- DeleteIgnoreVul
- DescribeAssetAppServiceList
- DescribeAssetComponentList
- DescribeAssetDBServiceList
- DescribeAssetHostList
- DescribeAssetImageDetail
- DescribeAssetImageHostList
- DescribeAssetImageList
- DescribeAssetImageListExport
- DescribeAssetImageRegistryAssetStatus
- DescribeAssetImageRegistryDetail
- DescribeAssetImageRegistryList
- DescribeAssetImageRegistryListExport
- DescribeAssetImageRegistryRegistryDetail
- DescribeAssetImageRegistryRegistryList
- DescribeAssetImageRegistryRiskInfoList
- DescribeAssetImageRegistryRiskListExport
- DescribeAssetImageRegistryScanStatusOneKey
- DescribeAssetImageRegistrySummary
- DescribeAssetImageRegistryVirusList
- DescribeAssetImageRegistryVirusListExport
- DescribeAssetImageRegistryVulList
- DescribeAssetImageRegistryVulListExport
- DescribeAssetImageRiskList
- DescribeAssetImageRiskListExport
- DescribeAssetImageScanSetting
- DescribeAssetImageScanStatus
- DescribeAssetImageScanTask
- DescribeAssetImageSimpleList
- DescribeAssetImageVirusList
- DescribeAssetImageVirusListExport
- DescribeAssetImageVulList
- DescribeAssetImageVulListExport
- DescribeAssetPortList
- DescribeAssetProcessList
- DescribeAssetWebServiceList
- DescribeAutoAuthorizedRuleHost
- DescribeContainerSecEventSummary
- DescribeImageAutoAuthorizedLogList
- DescribeImageAutoAuthorizedRule
- DescribeImageAutoAuthorizedTaskList
- DescribeImageComponentList
- DescribeImageRegistryNamespaceList
- DescribeImageRegistryTimingScanTask
- DescribeImageRiskSummary
- DescribeImageRiskTendency
- DescribeImageSimpleList
- DescribeNewestVul
- DescribePostPayDetail
- DescribeScanIgnoreVulList
- DescribeSecEventsTendency
- DescribeSystemVulList
- DescribeValueAddedSrvInfo
- DescribeVulDefenceEventTendency
- DescribeVulIgnoreLocalImageList
- DescribeVulIgnoreRegistryImageList
- DescribeVulImageSummary
- DescribeVulLevelImageSummary
- DescribeVulLevelSummary
- DescribeVulRegistryImageList
- DescribeVulScanAuthorizedImageSummary
- DescribeVulTendency
- DescribeVulTopRanking
- ModifyAsset
- ModifyAssetImageRegistryScanStop
- ModifyAssetImageRegistryScanStopOneKey
- ModifyAssetImageScanStop
- ModifyImageAuthorized
- ModifyVulDefenceEventStatus
- RemoveAssetImageRegistryRegistryDetail
- RenewImageAuthorizeState
- SwitchImageAutoAuthorizedRule
- SyncAssetImageRegistryAsset
- UpdateAssetImageRegistryRegistryDetail
- UpdateImageRegistryTimingScanTask
- DescribeAssetHostDetail
- DescribeAssetSummary
- DescribeContainerAssetSummary
- DescribeVulDefenceEventDetail
- DescribeVulSummary
- ModifyVulDefenceSetting
- DescribeAssetContainerDetail
- DescribeAssetContainerList
- DescribeVulDefenceEvent
- DescribeVulDefenceHost
- DescribeVulDefencePlugin
- DescribeVulDefenceSetting
- Billing APIs
- Data Types
- Error Codes
- FAQs
- TCSS Policy
- Contact Us
- Glossary
- Release Notes
- Product Introduction
- Purchase Guide
- Getting Started
- Operation Guide
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- Network Security APIs
- AddAndPublishNetworkFirewallPolicyDetail
- AddAndPublishNetworkFirewallPolicyYamlDetail
- AddNetworkFirewallPolicyDetail
- AddNetworkFirewallPolicyYamlDetail
- CheckNetworkFirewallPolicyYaml
- ConfirmNetworkFirewallPolicy
- CreateNetworkFirewallClusterRefresh
- CreateNetworkFirewallPolicyDiscover
- CreateNetworkFirewallPublish
- CreateNetworkFirewallUndoPublish
- DeleteNetworkFirewallPolicyDetail
- DescribeNetworkFirewallAuditRecord
- DescribeNetworkFirewallClusterList
- DescribeNetworkFirewallClusterRefreshStatus
- DescribeNetworkFirewallNamespaceLabelList
- DescribeNetworkFirewallPodLabelsList
- DescribeNetworkFirewallPolicyDetail
- DescribeNetworkFirewallPolicyDiscover
- DescribeNetworkFirewallPolicyList
- DescribeNetworkFirewallPolicyStatus
- DescribeNetworkFirewallPolicyYamlDetail
- UpdateAndPublishNetworkFirewallPolicyDetail
- UpdateAndPublishNetworkFirewallPolicyYamlDetail
- UpdateNetworkFirewallPolicyDetail
- UpdateNetworkFirewallPolicyYamlDetail
- Cluster Security APIs
- CreateCheckComponent
- CreateClusterCheckTask
- CreateRefreshTask
- DescribeAffectedClusterCount
- DescribeAffectedNodeList
- DescribeAffectedWorkloadList
- DescribeCheckItemList
- DescribeRefreshTask
- DescribeRiskList
- DescribeTaskResultSummary
- DescribeUnfinishRefreshTask
- DescribeUserCluster
- SetCheckMode
- DescribeClusterDetail
- DescribeClusterSummary
- Security Compliance APIs
- AddComplianceAssetPolicySetToWhitelist
- AddCompliancePolicyAssetSetToWhitelist
- AddCompliancePolicyItemToWhitelist
- CreateComplianceTask
- CreateExportComplianceStatusListJob
- DeleteComplianceAssetPolicySetFromWhitelist
- DeleteCompliancePolicyAssetSetFromWhitelist
- DeleteCompliancePolicyItemFromWhitelist
- DescribeComplianceAssetDetailInfo
- DescribeComplianceAssetList
- DescribeComplianceAssetPolicyItemList
- DescribeCompliancePeriodTaskList
- DescribeCompliancePolicyItemAffectedAssetList
- DescribeCompliancePolicyItemAffectedSummary
- DescribeComplianceScanFailedAssetList
- DescribeComplianceTaskAssetSummary
- DescribeComplianceTaskPolicyItemSummaryList
- DescribeComplianceWhitelistItemList
- InitializeUserComplianceEnvironment
- ModifyCompliancePeriodTask
- ScanComplianceAssets
- ScanComplianceAssetsByPolicyItem
- ScanCompliancePolicyItems
- ScanComplianceScanFailedAssets
- Runtime security - High-risk syscalls
- Runtime Security - Reverse Shell APIs
- Runtime Security APIs
- AddEditAbnormalProcessRule
- DescribeAssetImageBindRuleInfo
- AddEditAccessControlRule
- AddEditRiskSyscallWhiteList
- CreateDefenceVulExportJob
- CreateEmergencyVulExportJob
- CreateProcessEventsExportJob
- CreateRiskDnsEventExportJob
- CreateSystemVulExportJob
- CreateVulContainerExportJob
- CreateVulImageExportJob
- CreateVulScanTask
- CreateWebVulExportJob
- DeleteAbnormalProcessRules
- DeleteAccessControlRules
- DescribeAbnormalProcessEventTendency
- DescribeAbnormalProcessEventsExport
- DescribeAbnormalProcessLevelSummary
- DescribeAbnormalProcessRuleDetail
- DescribeAbnormalProcessRules
- DescribeAbnormalProcessRulesExport
- DescribeAccessControlRuleDetail
- DescribeAccessControlRules
- DescribeAccessControlRulesExport
- DescribeEmergencyVulList
- DescribeSupportDefenceVul
- DescribeVulContainerList
- DescribeVulDetail
- DescribeVulImageList
- DescribeVulScanInfo
- DescribeVulScanLocalImageList
- DescribeWebVulList
- ModifyAbnormalProcessRuleStatus
- ModifyAbnormalProcessStatus
- ModifyAccessControlRuleStatus
- ModifyAccessControlStatus
- OpenTcssTrial
- StopVulScanTask
- DescribeAccessControlEventsExport
- DescribeAbnormalProcessDetail
- DescribeAbnormalProcessEvents
- DescribeAccessControlDetail
- DescribeAccessControlEvents
- DescribeRiskSyscallDetail
- Alert Settings APIs
- Advanced prevention - K8s API abnormal requests
- CreateAccessControlsRuleExportJob
- CreateK8sApiAbnormalEventExportJob
- CreateK8sApiAbnormalRuleExportJob
- CreateK8sApiAbnormalRuleInfo
- DeleteK8sApiAbnormalRule
- DescribeAssetClusterList
- DescribeK8sApiAbnormalEventInfo
- DescribeK8sApiAbnormalEventList
- DescribeK8sApiAbnormalRuleInfo
- DescribeK8sApiAbnormalRuleList
- DescribeK8sApiAbnormalRuleScopeList
- DescribeK8sApiAbnormalSummary
- DescribeK8sApiAbnormalTendency
- ModifyK8sApiAbnormalEventStatus
- ModifyK8sApiAbnormalRuleInfo
- ModifyK8sApiAbnormalRuleStatus
- Asset Management APIs
- CreateAssetImageScanSetting
- CreateAssetImageVirusExportJob
- CreateHostExportJob
- DeleteMachine
- DescribeABTestConfig
- DescribeAgentDaemonSetCmd
- DescribeAgentInstallCommand
- DescribeAssetSyncLastTime
- DescribeExportJobDownloadURL
- DescribeExportJobManageList
- DescribeInspectionReport
- DescribePromotionActivity
- DescribeTcssSummary
- DescribeUnauthorizedCoresTendency
- ModifyContainerNetStatus
- Security Operations - Log Analysis APIs
- CreateSearchTemplate
- DeleteSearchTemplate
- DescribeESAggregations
- DescribeESHits
- DescribeIndexList
- DescribeLogStorageStatistic
- DescribePublicKey
- DescribeSearchExportList
- DescribeSearchLogs
- DescribeSearchTemplates
- DescribeSecLogAlertMsg
- DescribeSecLogCleanSettingInfo
- DescribeSecLogDeliveryClsOptions
- DescribeSecLogDeliveryClsSetting
- DescribeSecLogDeliveryKafkaOptions
- DescribeSecLogDeliveryKafkaSetting
- DescribeSecLogJoinTypeList
- DescribeSecLogKafkaUIN
- ModifySecLogCleanSettingInfo
- ModifySecLogDeliveryClsSetting
- ModifySecLogDeliveryKafkaSetting
- ModifySecLogJoinState
- ModifySecLogKafkaUIN
- ResetSecLogTopicConfig
- DescribeSecLogJoinObjectList
- ModifySecLogJoinObjects
- Runtime Security - Trojan Call APIs
- CreateVirusScanAgain
- DescribeExportJobResult
- DescribeVirusAutoIsolateSampleDetail
- DescribeVirusAutoIsolateSampleDownloadURL
- DescribeVirusAutoIsolateSampleList
- DescribeVirusAutoIsolateSetting
- DescribeVirusEventTendency
- DescribeVirusManualScanEstimateTimeout
- DescribeVirusSampleDownloadUrl
- DescribeVirusScanTaskStatus
- DescribeVirusScanTimeoutSetting
- DescribeVirusSummary
- ExportVirusList
- ModifyVirusAutoIsolateExampleSwitch
- ModifyVirusAutoIsolateSetting
- ModifyVirusFileStatus
- ModifyVirusScanTimeoutSetting
- StopVirusScanTask
- DescribeVirusMonitorSetting
- DescribeVirusScanSetting
- ModifyVirusMonitorSetting
- ModifyVirusScanSetting
- DescribeVirusList
- DescribeVirusTaskList
- CreateVirusScanTask
- DescribeVirusDetail
- Runtime Security - Container Escape APIs
- DeleteEscapeWhiteList
- CreateEscapeWhiteListExportJob
- CreateEscapeEventsExportJob
- AddEscapeWhiteList
- DescribeEscapeEventTendency
- DescribeEscapeEventsExport
- DescribeEscapeRuleInfo
- DescribeEscapeSafeState
- DescribeEscapeWhiteList
- DescribeEscapeEventTypeSummary
- ModifyEscapeEventStatus
- ModifyEscapeRule
- ModifyEscapeWhiteList
- DescribeEscapeEventDetail
- DescribeEscapeEventInfo
- Image Security APIs
- AddAssetImageRegistryRegistryDetail
- AddEditImageAutoAuthorizedRule
- AddIgnoreVul
- CheckRepeatAssetImageRegistry
- CreateAssetImageRegistryScanTask
- CreateAssetImageRegistryScanTaskOneKey
- CreateAssetImageScanTask
- CreateComponentExportJob
- CreateImageExportJob
- CreateOrModifyPostPayCores
- CreateVulDefenceEventExportJob
- CreateVulDefenceHostExportJob
- CreateVulExportJob
- DeleteIgnoreVul
- DescribeAssetAppServiceList
- DescribeAssetComponentList
- DescribeAssetDBServiceList
- DescribeAssetHostList
- DescribeAssetImageDetail
- DescribeAssetImageHostList
- DescribeAssetImageList
- DescribeAssetImageListExport
- DescribeAssetImageRegistryAssetStatus
- DescribeAssetImageRegistryDetail
- DescribeAssetImageRegistryList
- DescribeAssetImageRegistryListExport
- DescribeAssetImageRegistryRegistryDetail
- DescribeAssetImageRegistryRegistryList
- DescribeAssetImageRegistryRiskInfoList
- DescribeAssetImageRegistryRiskListExport
- DescribeAssetImageRegistryScanStatusOneKey
- DescribeAssetImageRegistrySummary
- DescribeAssetImageRegistryVirusList
- DescribeAssetImageRegistryVirusListExport
- DescribeAssetImageRegistryVulList
- DescribeAssetImageRegistryVulListExport
- DescribeAssetImageRiskList
- DescribeAssetImageRiskListExport
- DescribeAssetImageScanSetting
- DescribeAssetImageScanStatus
- DescribeAssetImageScanTask
- DescribeAssetImageSimpleList
- DescribeAssetImageVirusList
- DescribeAssetImageVirusListExport
- DescribeAssetImageVulList
- DescribeAssetImageVulListExport
- DescribeAssetPortList
- DescribeAssetProcessList
- DescribeAssetWebServiceList
- DescribeAutoAuthorizedRuleHost
- DescribeContainerSecEventSummary
- DescribeImageAutoAuthorizedLogList
- DescribeImageAutoAuthorizedRule
- DescribeImageAutoAuthorizedTaskList
- DescribeImageComponentList
- DescribeImageRegistryNamespaceList
- DescribeImageRegistryTimingScanTask
- DescribeImageRiskSummary
- DescribeImageRiskTendency
- DescribeImageSimpleList
- DescribeNewestVul
- DescribePostPayDetail
- DescribeScanIgnoreVulList
- DescribeSecEventsTendency
- DescribeSystemVulList
- DescribeValueAddedSrvInfo
- DescribeVulDefenceEventTendency
- DescribeVulIgnoreLocalImageList
- DescribeVulIgnoreRegistryImageList
- DescribeVulImageSummary
- DescribeVulLevelImageSummary
- DescribeVulLevelSummary
- DescribeVulRegistryImageList
- DescribeVulScanAuthorizedImageSummary
- DescribeVulTendency
- DescribeVulTopRanking
- ModifyAsset
- ModifyAssetImageRegistryScanStop
- ModifyAssetImageRegistryScanStopOneKey
- ModifyAssetImageScanStop
- ModifyImageAuthorized
- ModifyVulDefenceEventStatus
- RemoveAssetImageRegistryRegistryDetail
- RenewImageAuthorizeState
- SwitchImageAutoAuthorizedRule
- SyncAssetImageRegistryAsset
- UpdateAssetImageRegistryRegistryDetail
- UpdateImageRegistryTimingScanTask
- DescribeAssetHostDetail
- DescribeAssetSummary
- DescribeContainerAssetSummary
- DescribeVulDefenceEventDetail
- DescribeVulSummary
- ModifyVulDefenceSetting
- DescribeAssetContainerDetail
- DescribeAssetContainerList
- DescribeVulDefenceEvent
- DescribeVulDefenceHost
- DescribeVulDefencePlugin
- DescribeVulDefenceSetting
- Billing APIs
- Data Types
- Error Codes
- FAQs
- TCSS Policy
- Contact Us
- Glossary
Users can configure alarms and interception policies on the image interception policies page. The image interception policy allows you to intercept the startup of containers for images that have critical security issues, thereby preventing malicious images from running container services.
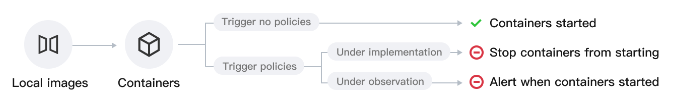
After you create and activate an interception policy, it will take effect in about 3-5 minutes. Once it is activated, if a hit risk image attempts to start a container, the system will alarm or intercept the container startup and report the interception records, based on the configured policy's alarm and interception requirements.
Currently supported intercepted image types: Images with critical and high-risk vulnerabilities, Trojan viruses, and sensitive information risks, as well as privileged images.
Privileged image interception supports only one rule configured. To modify the range of intercepted images, you can edit the configured rule.
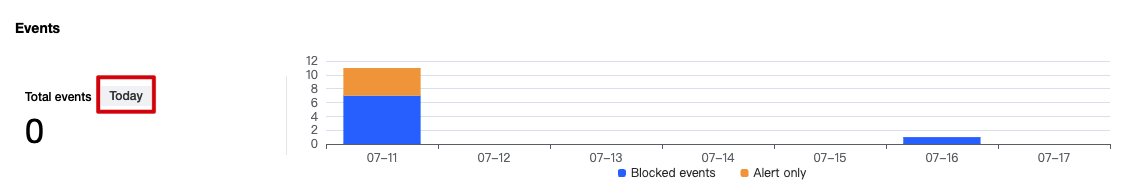
Event Overview
Once the user configures the image startup interception policy and sets it to take immediate effect, attempts to start containers using targeted risky images will be intercepted in real-time, with the image startup actions reported and recorded. If the policy includes an observation period, during which only alarms are issued without interception, attempts to start containers using targeted risky images will trigger real-time reporting of the image startup actions. In both scenarios, event logs will be generated.
In the image interception events > Events, daily statistics will be provided for both image startup interception events and events where only alarms were triggered. Trend charts for both types of events over the past 7 days and the current total number of events will be displayed.
Policy Overview
On the image interception policy page, after you have configured the alarm and interception policies, the system will count the total number of enabled policies, as well as the number of included effective interception policies and observation period policies. In the image interception events > Policies, click View policy details to jump to Policy Management > Image Blocking Policies page to view the details of the image interception policies.

Event List
In the image interception events > Event List, the recorded are the image startup interception events generated by effective interception policies and the image startup alarm events generated by observation period policies. Users can filter events by type, executed action, or latest creation time, and perform keyword searches, such as the hit policy, image name, image ID, name of the node hosting the image, private IP of the node, and public IP of the node.
Event type: Risky image interception, where the image contains certain vulnerabilities, Trojans, or sensitive information needs interception. Privileged image interception, where the image is intercepted when a container is started in privileged mode.
Executed action: Interception successful, indicating image startup interception events generated by effective interception policies. Alarm, indicating image startup alarm events generated by observation period policies.
Users can click Details in the action bar to view event details, including event details, hit policy, impact, risk description, and solution.
Event details: The system will aggregate the same interception or alarm events for the same image, with the aggregation time being the current day. This section shows the event type, number of events, and time period of interception or interception events.
Hit policy: Displays the name, type, startup status, policy status, interception start time, policy description, and policy interception content of effective interception policies or observation period policies. Users can click Details next to the policy name/policy type to view the policy details associated with this event.
Impact: Displays details of the targeted images requiring interception, including the image name, image ID, and the name and IP address of the node hosting the image.
Risk description: Displays the reasons behind the interception events or alarm events, such as interception due to the presence of critical vulnerabilities or hitting the interception policy. Additionally, it provides detailed parameters of the image startup process.
Solution: It is recommended that users repair images with vulnerabilities, Trojan viruses, or sensitive information to avoid impacting the business.

 Yes
Yes
 No
No
Was this page helpful?