告警策略(腾讯云可观测平台)
最后更新时间:2025-10-30 17:48:39
本文为您介绍通过腾讯云可观测平台控制台,创建告警策略和关联告警对象的操作。
操作场景
您可以创建告警用于在云产品状态改变时触发警报并发送相关消息。创建的告警会根据每隔一段时间监控的指标相对于给定阈值的情况判断,是否需要触发相关通知。
状态改变触发告警后,您可以及时进行相应的预防或补救措施。因此,合理地创建告警能帮助您提高应用程序的健壮性和可靠性。有关告警的更多信息,请参见腾讯云可观测平台的 告警配置。
当用户需要针对某个产品的某个状态发送告警时,需要先创建告警策略。告警策略包括名称、类型和告警触发条件三个必要组成部分。每个告警策略是一系列告警触发条件的集合,告警触发条件是“或”关系,即一个条件满足,就会发送告警。告警将发送至告警策略关联的所有人,用户接收到告警后可以及时查看并采取相应措施。
注意:
请确认您已经设置默认告警接收人,否则腾讯云数据库的默认告警策略将无法通知到您。
操作步骤
创建告警策略
1. 登录 腾讯云可观测平台控制台,在左侧导航选择告警管理 > 告警配置页。
2. 在告警策略列表页中,单击新建。
3. 在新建策略页中,设置策略名称、策略类型、告警对象、触发条件等内容。
策略类型:分为主机监控和备机监控,分别适用于不同的实例类型。
部署类监控为主机:当监控实例为主实例时,由于其主实例不为任何实例的从实例,因此其主机下复制相关的监控数据无效,此时其 IO、SQL 线程状态为未启动。仅当监控实例为灾备实例和只读实例时,其对应复制相关的监控数据才有效,且 IO、SQL 线程才是启动的状态。
部署类监控为备机:双节点、三节点的主实例与灾备实例默认为主备架构,因此,仅当监控实例为主实例及灾备实例时,其备机下复制相关的监控数据才有效。用于反映主实例、灾备实例与其隐藏备节点的延迟距离及时间,建议关注备机下相关的监控数据,若主实例及灾备实例存在故障时,其监控实例对应隐藏的备节点可快速提升为主实例。
告警对象:可通过选择对象所在的地域或搜索对象的实例 ID 找到需要关联的对象实例。
触发条件:指标、比较关系、阈值、统计周期和持续周期组成的一个有语义的条件。例如:指标为磁盘使用率、比较关系为>、阈值为80%、统计周期为5分钟、持续周期为2个周期。表示:每5分钟收集一次磁盘使用率数据,若某台云数据库的磁盘使用率连续两次大于80%则触发告警。
配置告警通知:支持选择系统预设通知模板和用户自定义通知模板,每个告警策略最多只能绑定三个通知模板,详情请参考 通知模板。
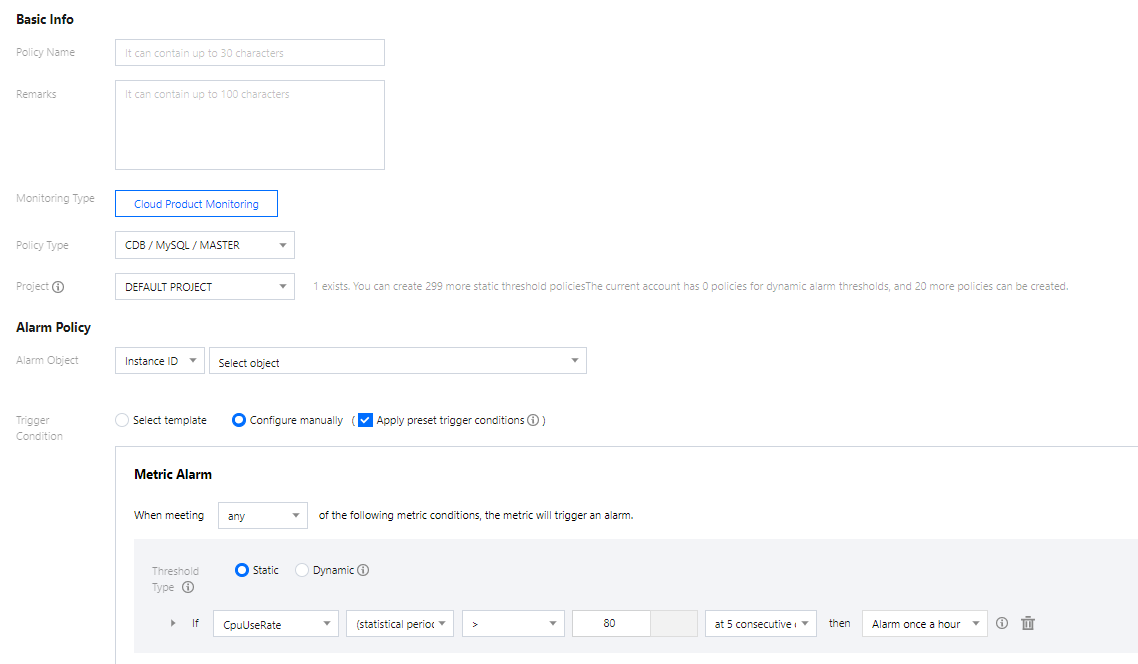
4. 确认无误后,单击完成。
关联告警对象
创建完告警策略后,您可以为其关联一些告警对象,对象达到告警触发条件时会发送告警。
1. 在 告警策略列表页,单击告警策略名称,进入管理告警策略页。
2. 在管理告警策略页的告警对象栏,单击新增对象。
3. 在弹出的对话框,选择您需要关联的告警对象,单击确定,即可关联告警对象。
热点问题
如何配置主从延迟监控?
配置主从延迟监控分为以下两种场景,您可根据实际场景对应操作。
场景一:为主实例配置主从延迟监控
1.1 登录 腾讯云可观测平台控制台,在左侧导航选择告警管理,然后选择策略管理 > 新建策略。
1.2 在告警策略页,策略类型项选择:云数据库 > MySQL > 备机监控。
说明:
为主实例配置主从延迟监控,策略类型要选择备机监控,监控的是备机到主机的延迟信息。
1.3 在配置告警规则下完成对监控项“主从延迟距离”和“主从延迟时间”的触发条件设置,然后根据您的需要完成其他配置项的设置,单击完成。
1.4 设置完成后,当“主从延迟距离”和“主从延迟时间”监控项满足触发条件时即可触发告警。
场景二:为 RO 和灾备实例配置主从延迟监控
1.1 登录 腾讯云可观测平台控制台,在左侧导航选择告警管理,然后选择策略管理 > 新建策略。
1.2 在告警策略页,策略类型项选择:云数据库 > MySQL > 主机监控。
说明:
为 RO 实例配置主从延迟监控,策略类型只能选主机监控,监控的是 RO 实例到其主实例的延迟信息。
为灾备实例配置主从延迟监控,策略类型若选择主机监控,则监控的是灾备实例到其主实例的延迟信息,若选择备机监控,则监控的是灾备实例的备机到灾备实例的延迟信息。
1.3 在配置告警规则下完成对监控项“主从延迟距离”和“主从延迟时间”的触发条件设置,然后根据您的需要完成其他配置项的设置,单击完成。
1.4 设置完成后,当“主从延迟距离”和“主从延迟时间”监控项满足触发条件时即可触发告警。
文档反馈

