VPC 间防火墙实践教程
最后更新时间:2024-09-06 17:57:03
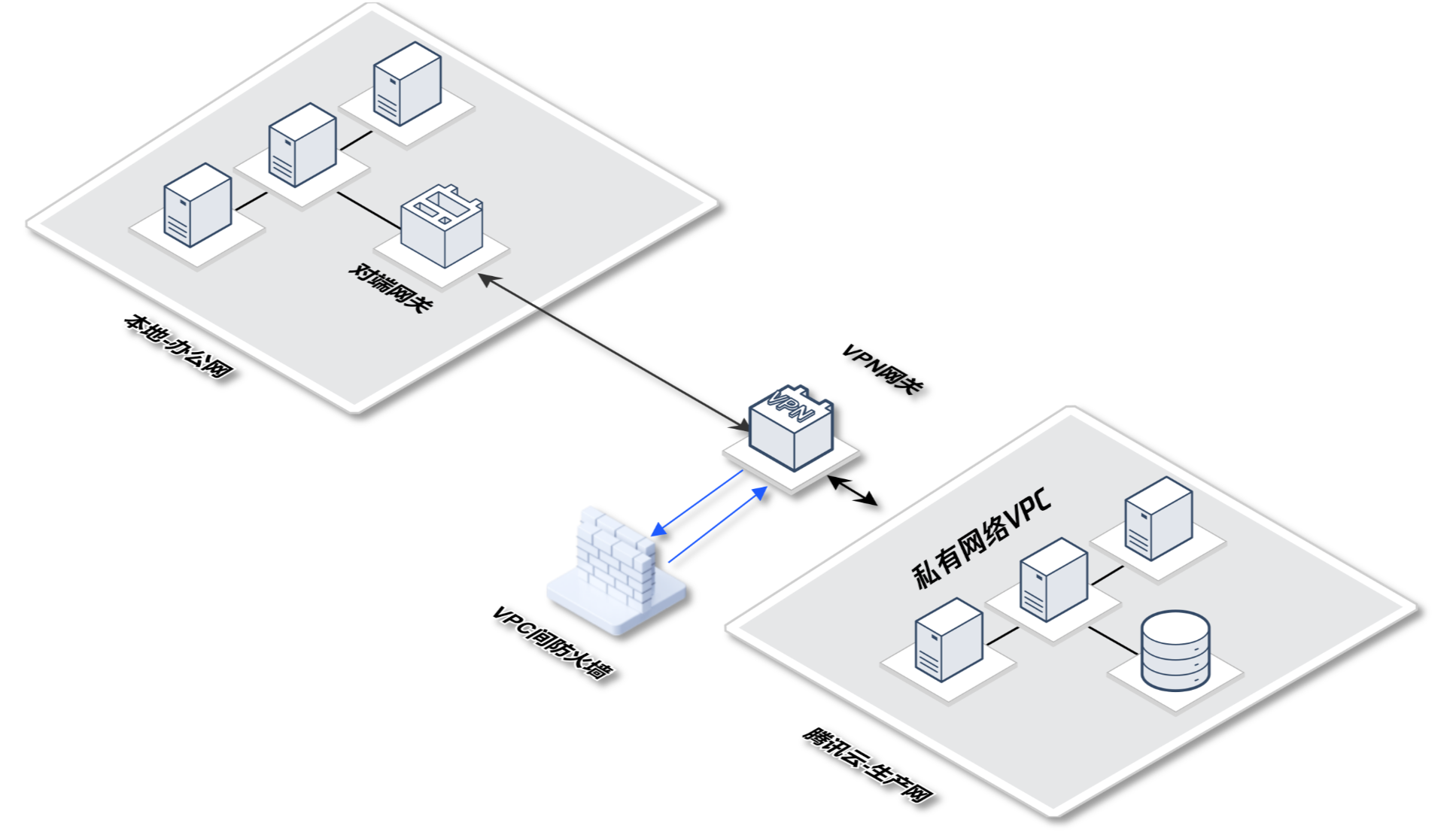
VPN 上云场景
用户需求:采用 VPN 连接办公网和公有云,核心业务和数据在公有云上,办公网安全监控情况低于生产网。
业务挑战:当因为钓鱼等攻击导致本地办公网失陷时,攻击者可以很轻易的通过 VPC 专线攻击云上核心业务。
解决方案:接入 VPC 间防火墙,并开启入侵防御拦截模式,自动阻断监测办公网对云上业务的访问行为,阻断扫描、攻击流量。
实践配置:参考 新建 VPC 间防火墙 进行配置,选择云联网模式接入,防火墙 VPC 选择自动选择,路由模式选择单点互通。
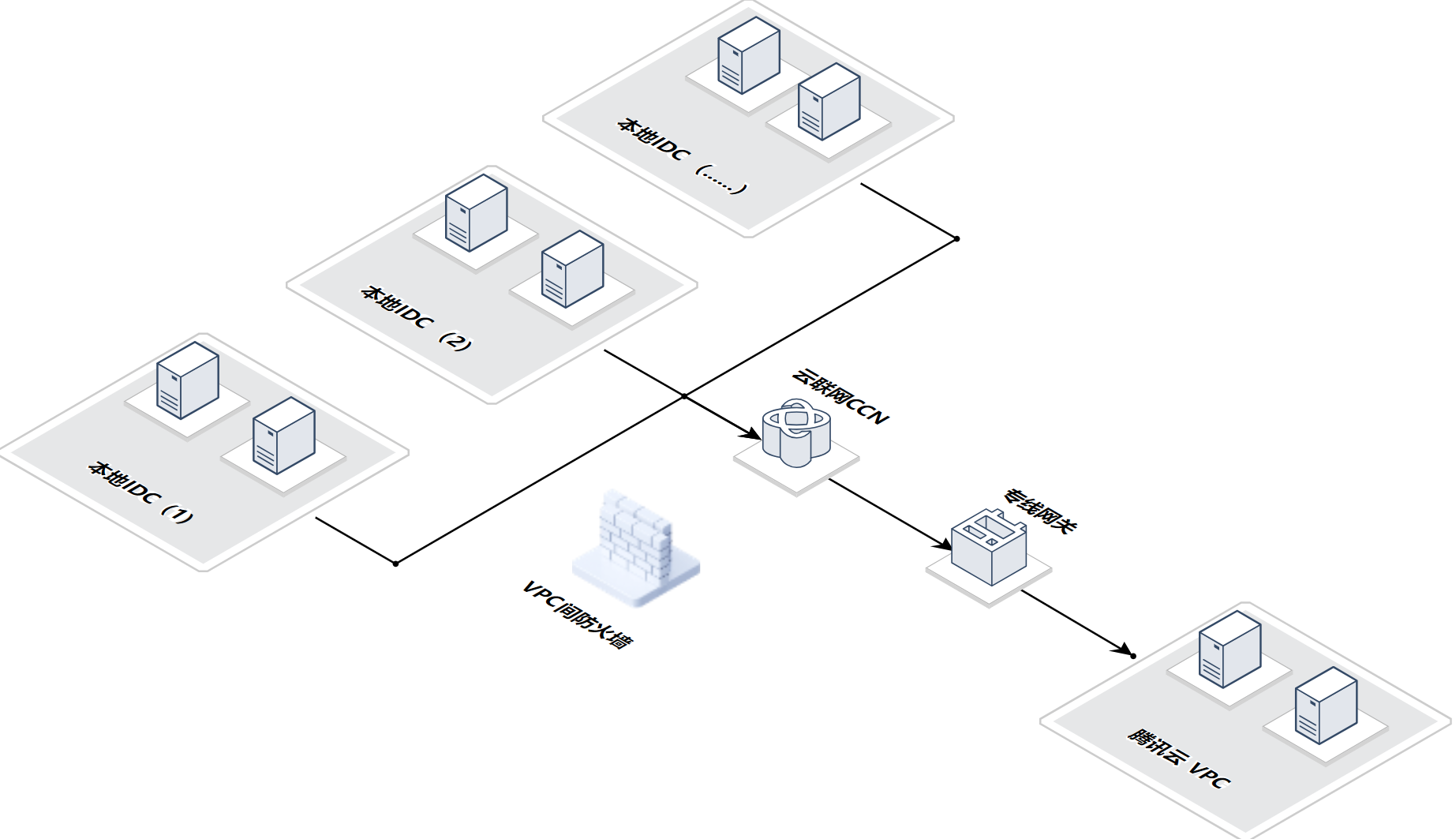
混合云场景
用户需求:客户有多个本地 IDC,通过云联网互联,并使用专线打通公有云 VPC。
业务挑战:当需要隔离部分 IDC,不允许这些 IDC 访问公有云业务;同时需要避免本地 IDC 失陷后 ,横向扩散到云上。
解决方案:接入 VPC 间防火墙,并开启入侵防御。设置访问控制规则,对源地址为某些 IDC 的进行阻断。
实践配置:参考 新建 VPC 间防火墙 进行配置,选择云联网模式接入,防火墙 VPC 选择自动选择,路由模式选择多点互通(如本地 IDC 数量较少,可选择单点互通)。
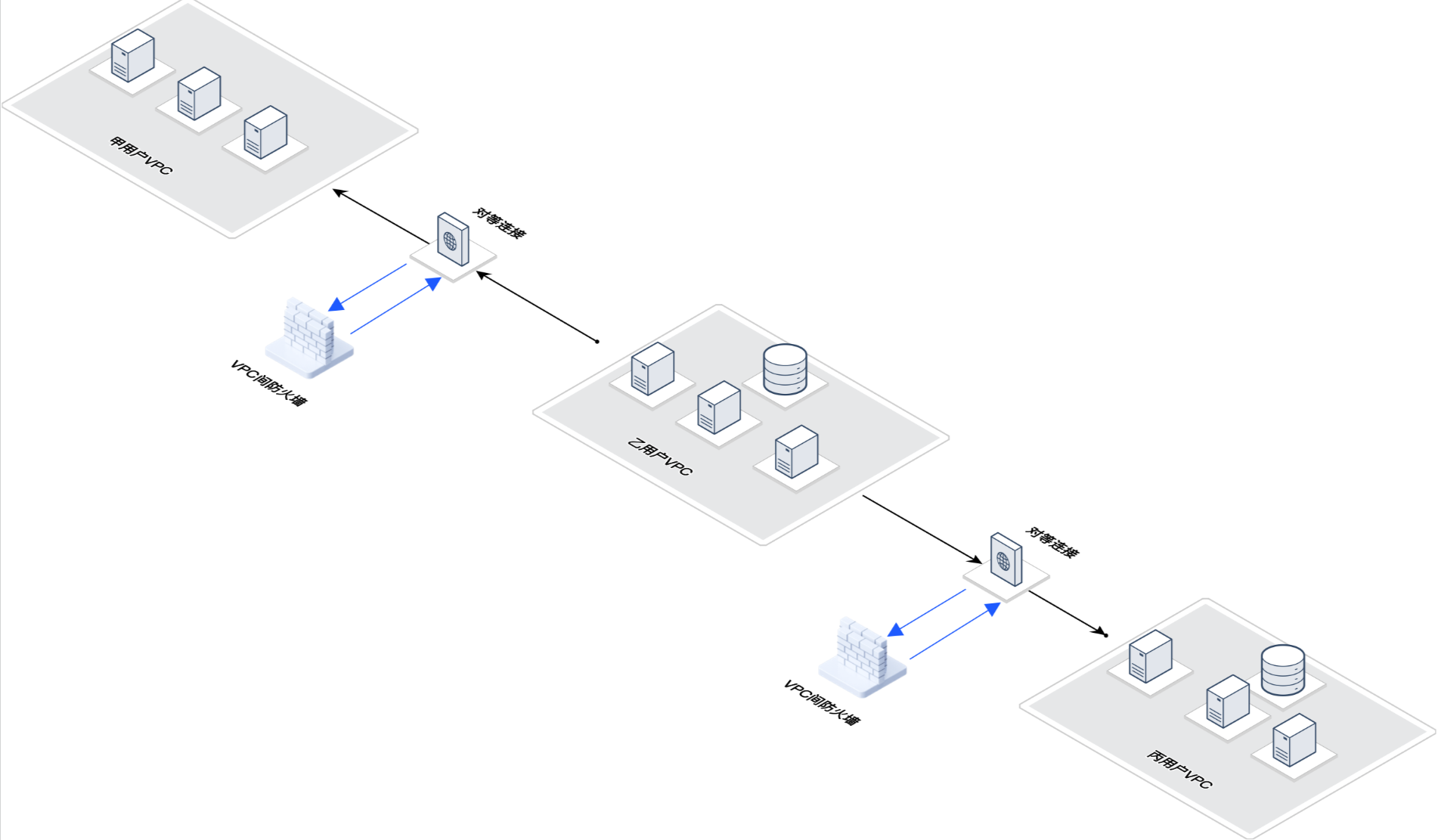
跨账号对等连接场景
用户需求:乙用户云上业务,需要向甲、丙用户获取数据,要求数据只进不出。
业务挑战:需要允许乙用户 VPC 访问甲、丙 VPC,为了确保数据安全,需要阻断甲用户 VPC、丙用户 VPC 对乙用户的访问。
解决方案:接入 VPC 间防火墙,配置访问控制规则,对目的地址为乙用户 VPC 的流量全部阻断。
实践配置:参考 新建 VPC 间防火墙 进行配置,选择私有网络模式接入,防火墙 VPC选择自动选择,路由模式选择单点互通。
热点问题
接入 VPC 间防火墙是否对业务有影响?
接入时会出现极短的闪断,建议选择业务较空闲时段进行。云防火墙可提供研发支持,根据经验,接入 VPC 间防火墙对业务影响较小。如担心对业务产生影响,可在测试环境进行尝试。
能否通过安全组替代 VPC 间防火墙?
VPC 间防火墙可以进行日志的审计,观察到命中的规则和放行的流量,但服务器的安全组则无此功能。同时,VPC 间防火墙的入侵防御功能可以应对流量中的威胁,监测发起的扫描流量和攻击流量,而安全组则不具备此功能。
文档反馈

