多云接入
最后更新时间:2025-11-28 15:24:25
功能简介
当用户业务同时部署在腾讯云和第三方云厂商时,支持通过腾讯云云安全中心集中管理多云资源(目前支持亚马逊云 AWS、微软云 Azure)。通过接入多云账号,实现多云安全管理上的透明化与可视化,实时掌握第三方云上业务的安全防护状态、风险等信息。
操作步骤
1. 登录 云安全中心控制台,在左侧导览中,单击多云多账号管理。
2. 在多云多账号管理页面,单击接入多云账号。


Azure 账号
步骤1:应用注册
1. 登录 Azure 后前往应用注册页面,单击新注册(如果已有应用注册,跳到第二步)。
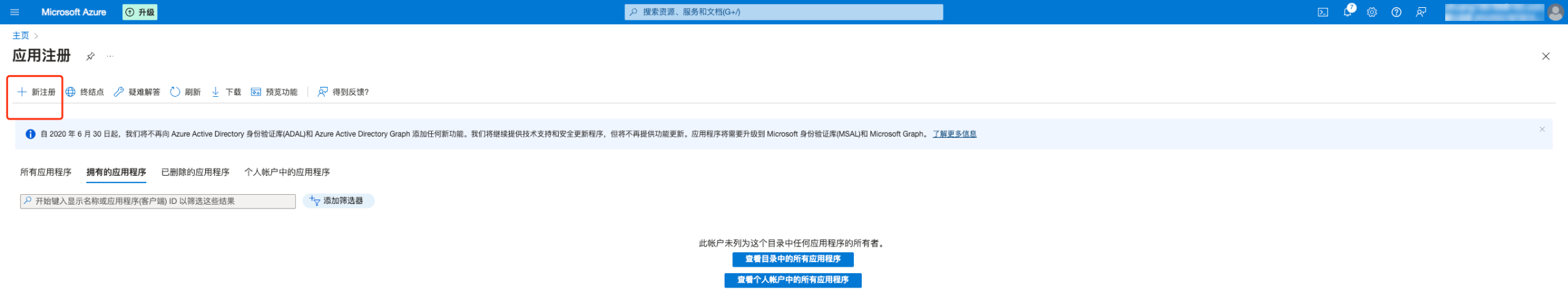
2. 在注册应用程序页面,填写应用程序“名称”,并根据实际需要选择“受支持的账户类型”,单击注册。
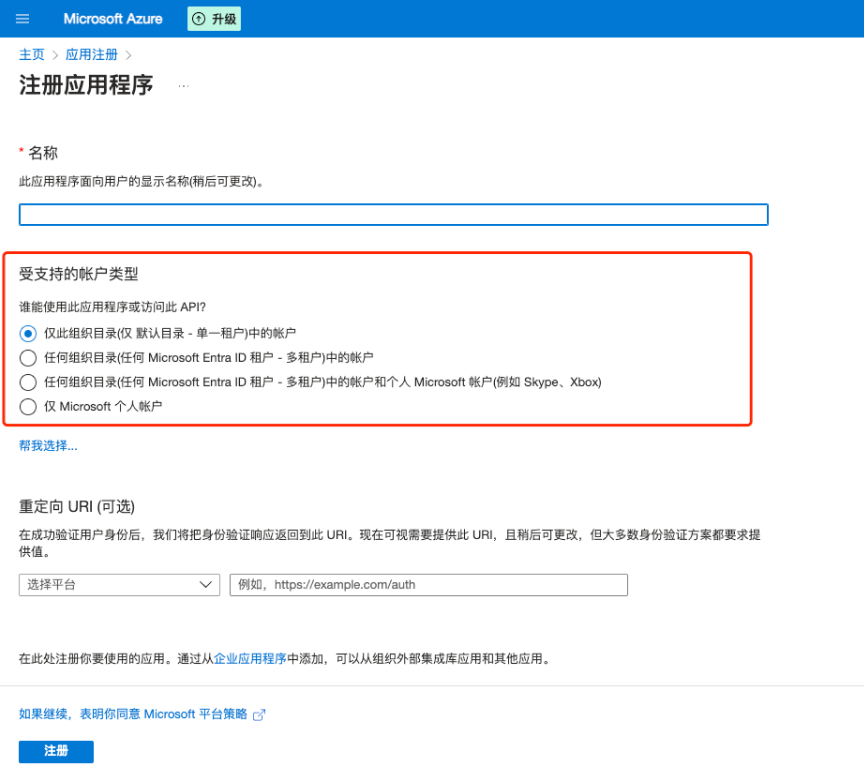
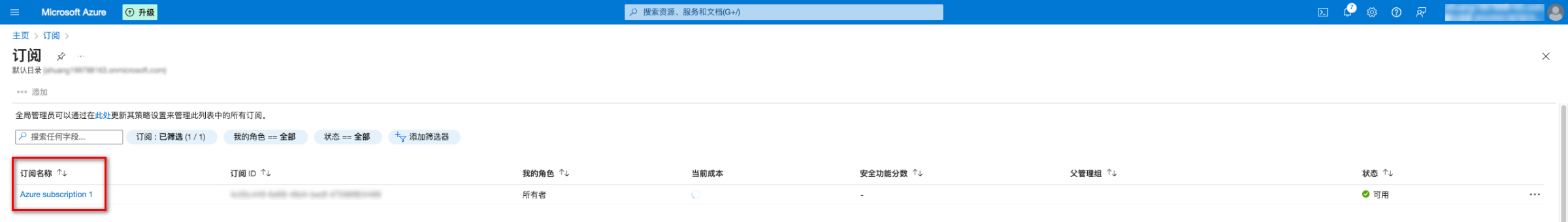
步骤2:获取订阅 ID
1. 在订阅列表页面,选择将要接入的订阅(应用注册可以绑定多个订阅),单击订阅名称。
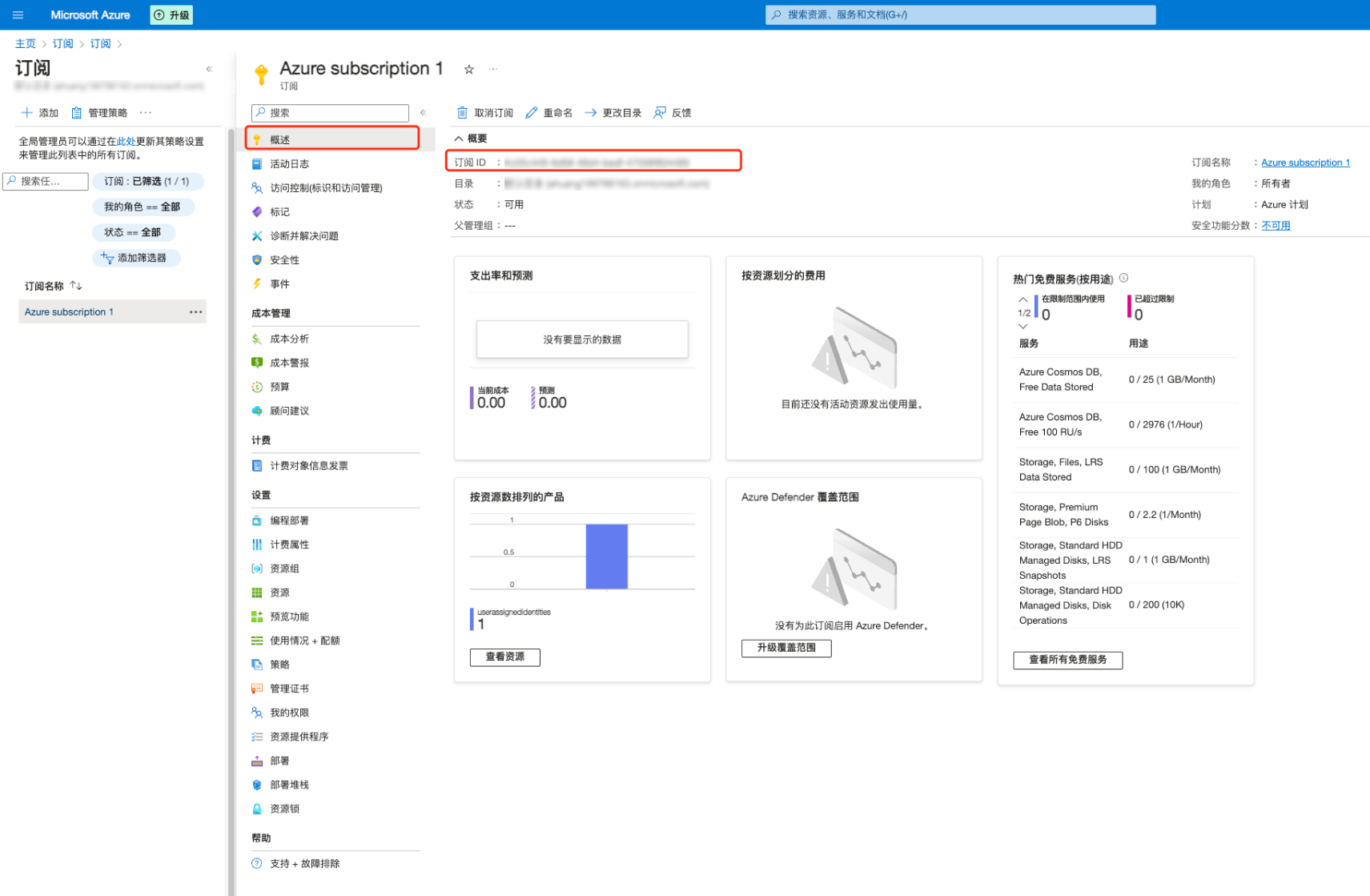
2. 在订阅详情页面,单击概述,获取订阅 ID。

3. 选择访问控制,单击添加,选择添加角色分配。

4. 选择需要分配的角色,建议依次选择“读者 ”和“Azure Kubernetes 服务群集用户角色”,单击下一步。

5. 添加需要分配的用户,单击选择成员,在搜索框输入要添加的“应用注册”名称,选择该应用注册,单击下一步。
6. 确定角色与成员,单击审阅和分配。

步骤3:获取租户 ID、客户端 ID、客户端密钥
1. 进入刚刚绑定的应用注册页面,单击概览,获取“①客户端 ID”与“②租户 ID”。

2. 单击证书和密码 > 新客户端密码,填写说明,截止期限选择730天(24个月),单击添加。
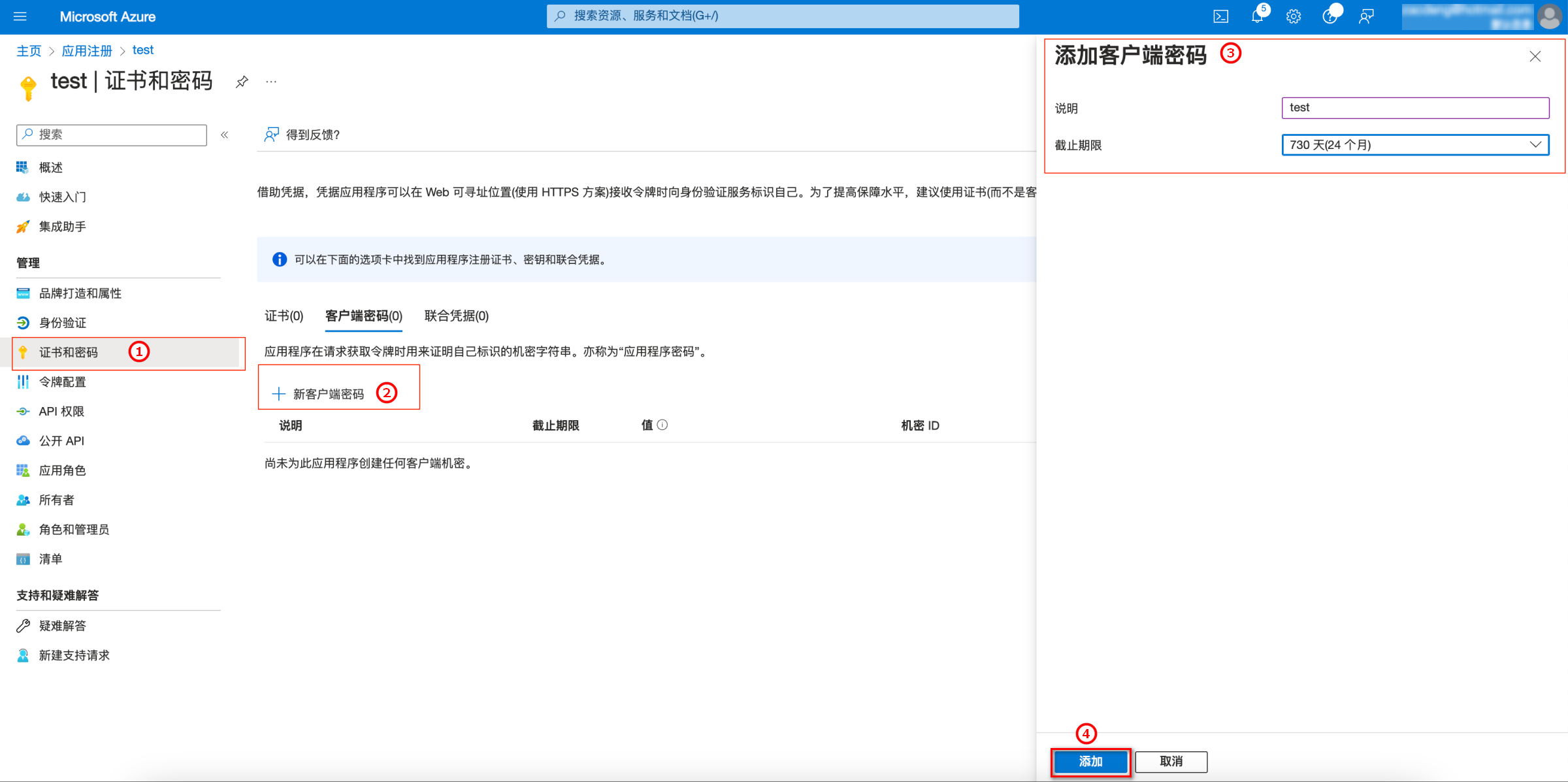
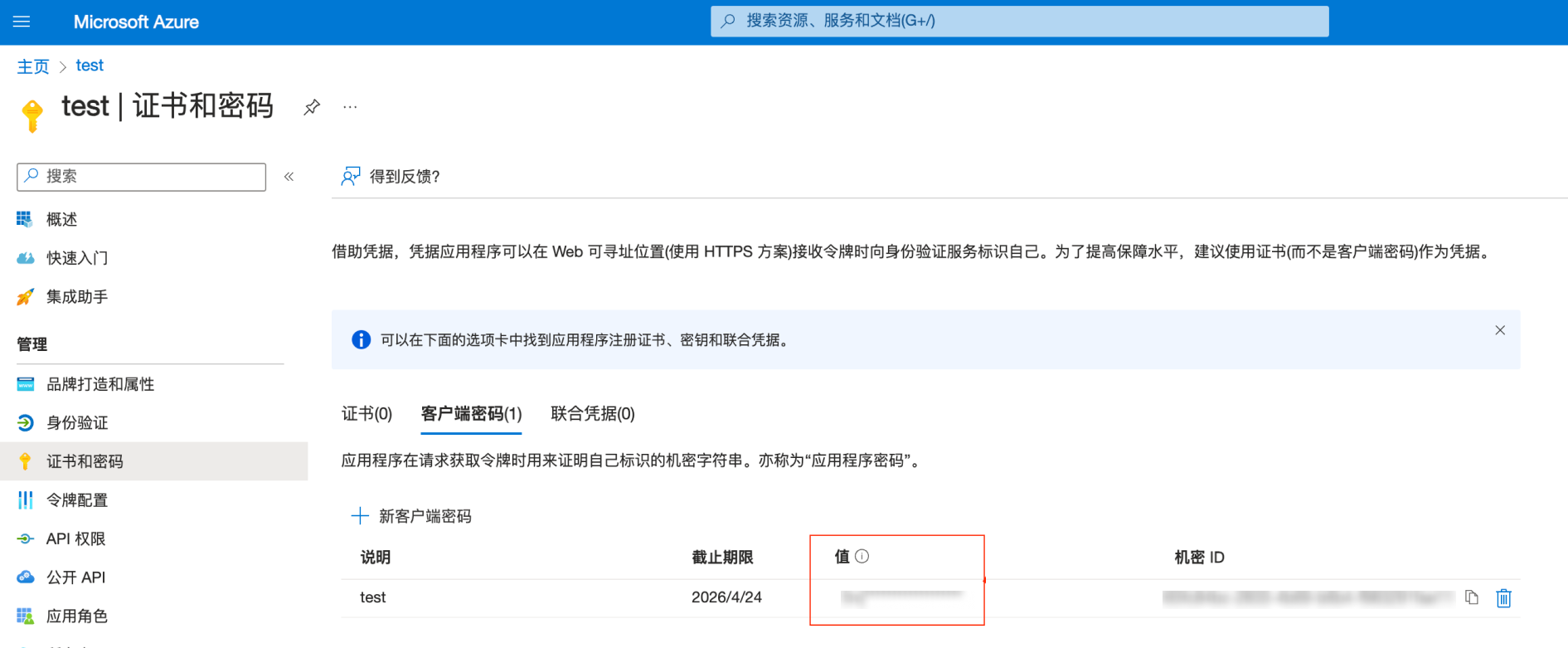
3. 在证书和密钥页面,获取客户端密钥。
AWS 账号
快速配置
完成时间约为1分钟,但因需要较高权限,需配置主账号的 AK。之后,云安全中心会自动创建一个子账号 AK 以接入资产,并授予对所有资产的只读权限。
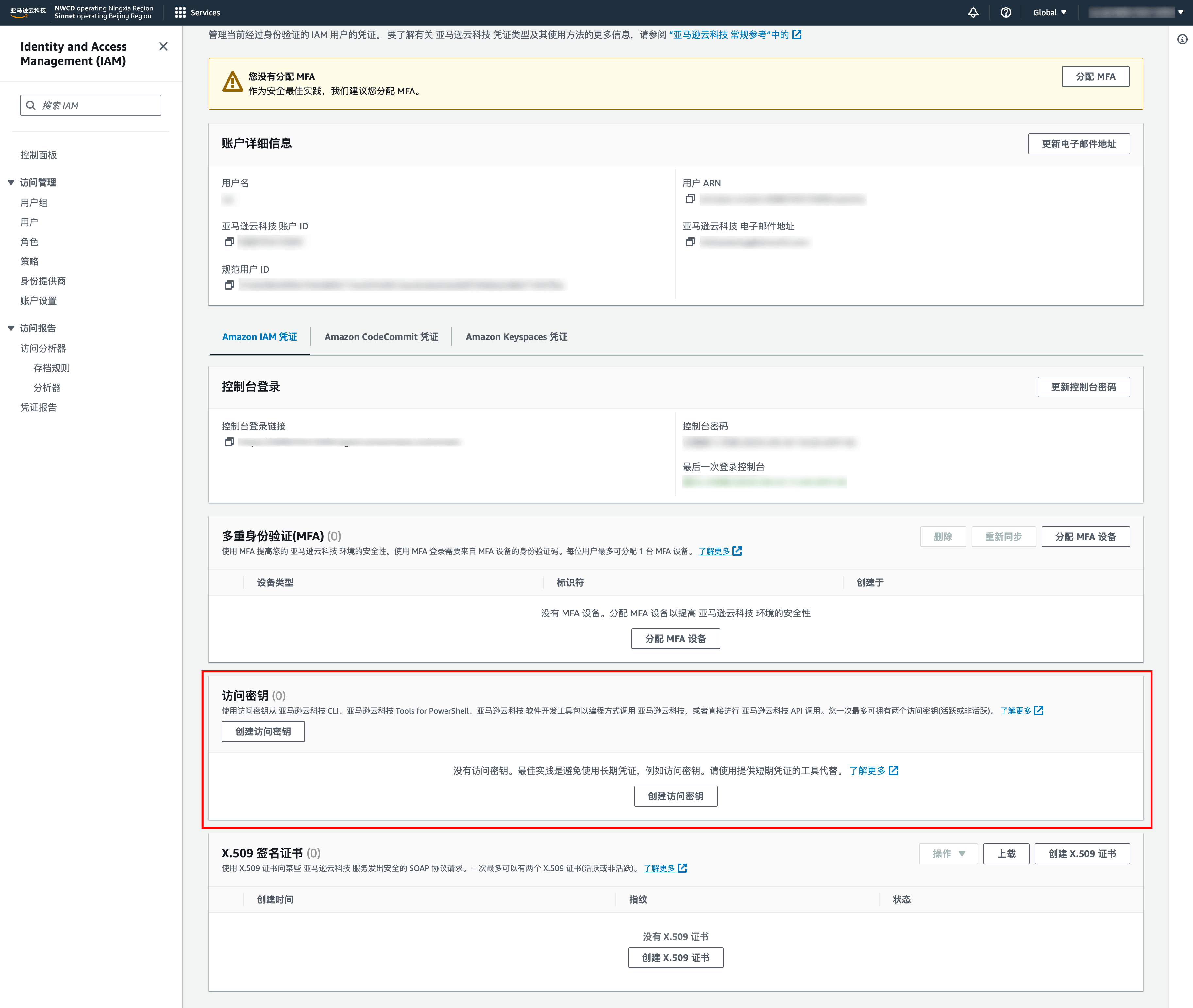
1. 请登录 AWS 后前往 安全凭证 页面,单击创建访问密钥生成可用于监控或管理亚马逊云科技资源的“访问密钥”、“秘密访问密钥”。
2. 在检索访问密钥页面,查看或下载“访问密钥”、“秘密访问密钥”。
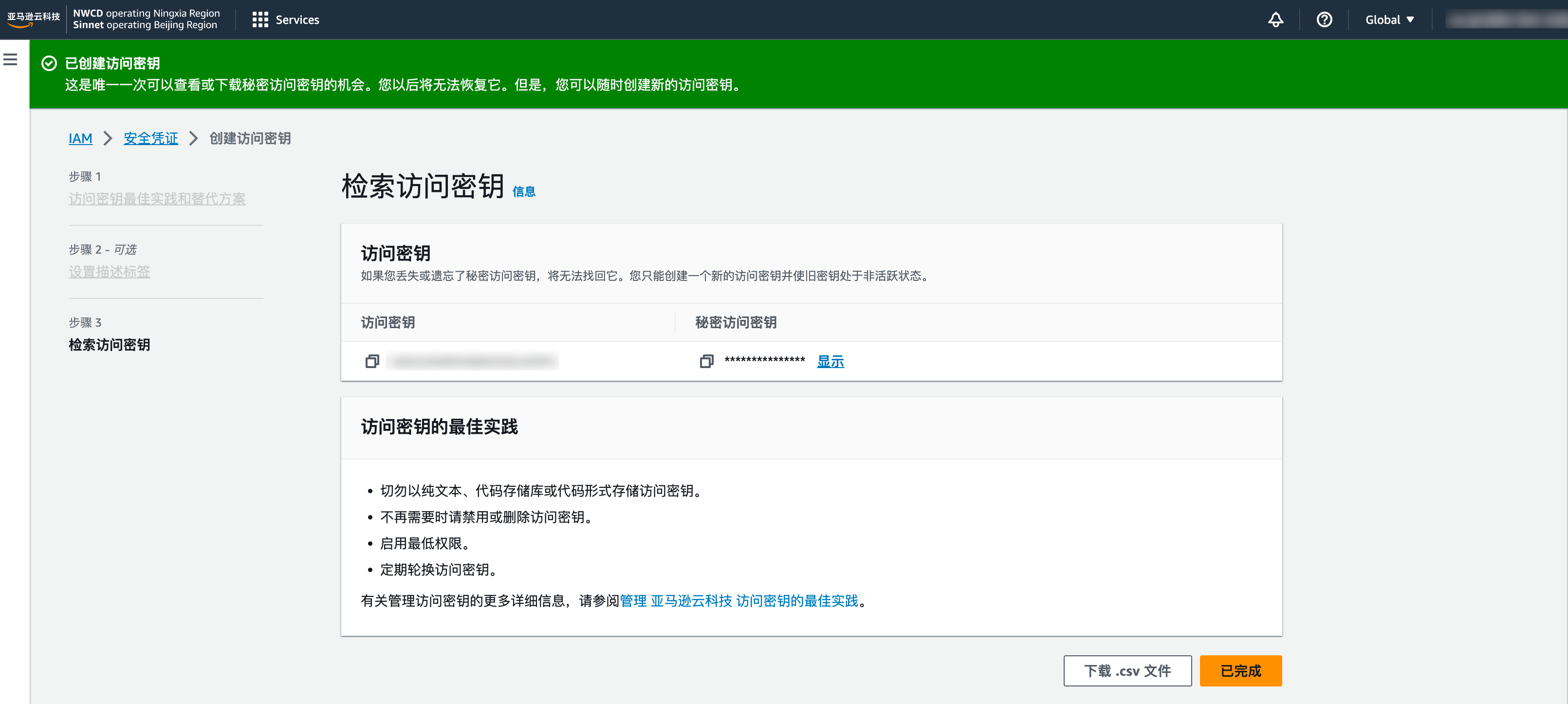
3. 确保“访问密钥”的状态为 Active 后,将“访问密钥”、“秘密访问密钥”填写至“主账号 SecretID”、“主账号 SecretKey”。

手动配置
完成时间约为5分钟,但权限配置较为复杂,需要为创建好的子账号配置访问密钥(AK),以便更灵活地控制权限范围。
1. 请登录 AWS 后前往 IAM > 用户 页面,单击创建用户,创建子账号用于与账户中的亚马逊云科技进行交互。

2. 进入该子用户详情,单击创建访问密钥生成可用于监控或管理亚马逊云科技 资源的“访问密钥”、“秘密访问密钥”。

3. 查看或下载“访问密钥”、“秘密访问密钥”,确保“访问密钥”的状态为 Active 后,将“访问密钥”、“秘密访问密钥”填写至“子账号SecretID”、“子账号 SecretKey”。

高级配置
较为复杂,但权限范围和期限可控。请按照我们提供的 RoleArn 在 AWS 创建角色,并授权指定 ARN 且带有 uuid 的账号调用 sts:AssumeRole 接口。该接口用于创建账号的临时访问角色。
1. 请登录 AWS 后前往IAM > 角色 页面,单击创建角色,该身份具有特定权限,凭证在短期内有效。角色可以由您信任的实体承担。
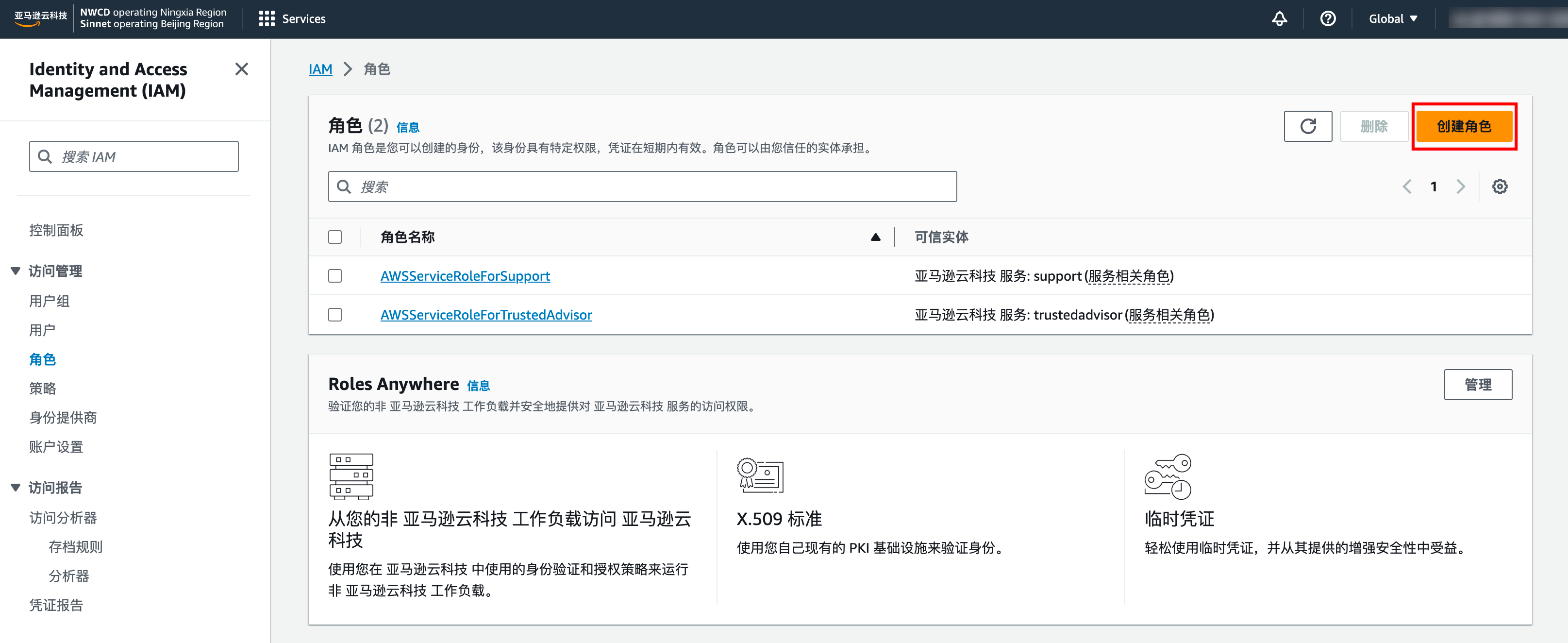
2. 选择“亚马逊云科技账户”为可信实体类型后,根据所需权限创建角色。
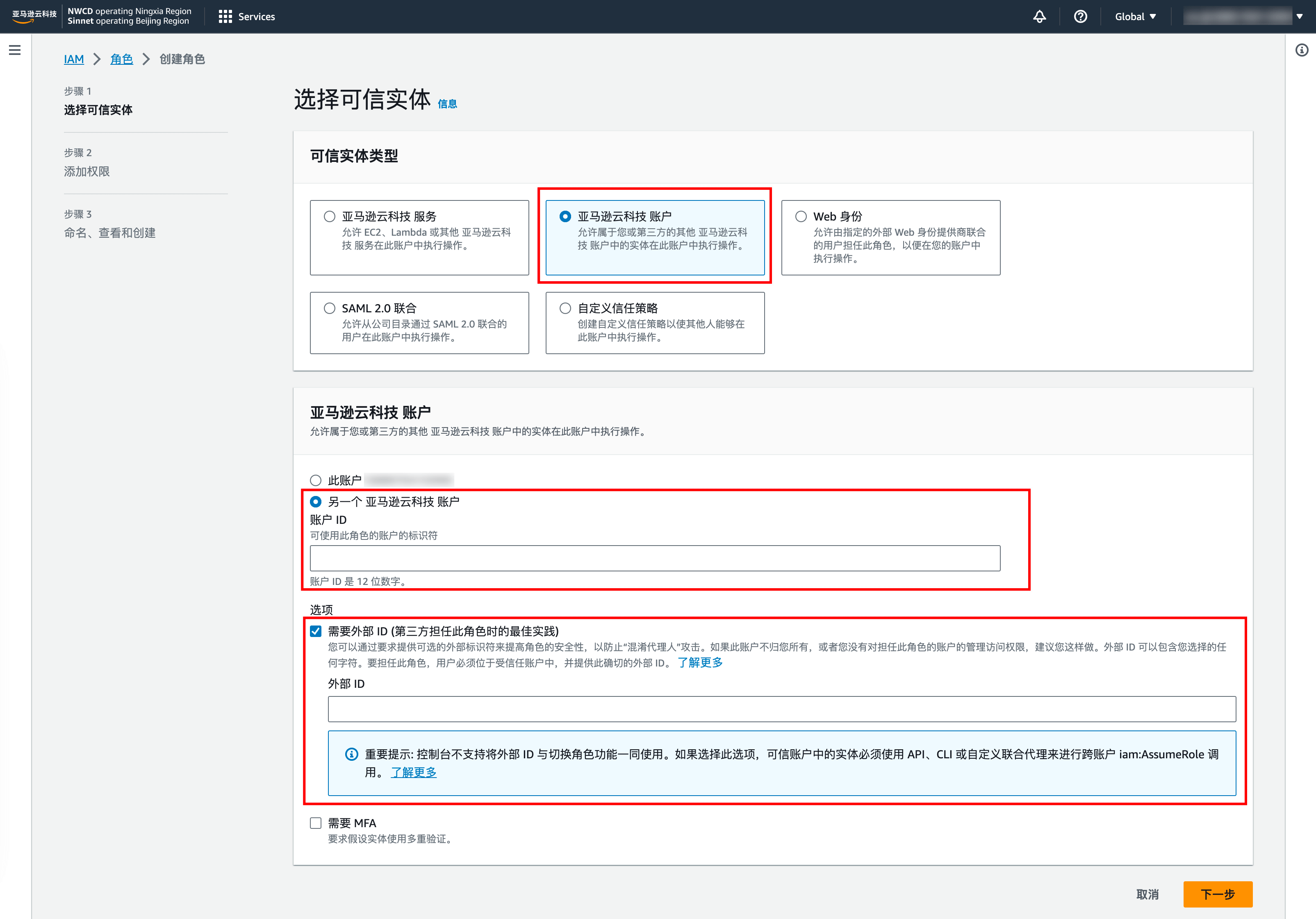
3. 进入该角色详情,将“ARN”复制并填入“RoleArn”框中。
文档反馈

