Cloud Migration
- Release Notes and Announcements
- Data Collector
- Migration Implementation
- Research Analysis
- COS Migration Guide
Offline Tool
Last updated: 2025-04-09 15:53:49
This document mainly introduces how to use the Offline Collection Tool provided by cloud migration. Currently, cloud migration supports collecting origin resources from AWS international website through the Offline Collection Tool. Subsequently, it will support the collection of resources from more cloud service providers. You can choose a suitable research method according to the actual situation.
Notes:
This operation guide is for reference only and is intended to provide users with a clear guide. Some materials come from third-party public information. For details, see the relevant pages of the third party.
Application Scenario
Tencent Cloud resource research tool for collecting resource usage from the source platform for customers. Currently supports scanning source resources on the AWS international site. If the Tencent Cloud resource region is outside the Chinese mainland, download the scan tool to nodes outside the Chinese mainland for scanning, which can reduce API call failures of cloud service providers caused by network issues.
Preparations
The scan tool requires specifying the vendor name where the cloud resource resides, the Region where the resource is located, and the key pair for accessing cloud resources (AccessKeyID and AccessKeySecret).
Following takes AWS as an example:
1. Confirm the region where the resource is located, for example, cn-shanghai, cn-beijing. The specific region needs to be determined by combining the source platform and the actual situation of the customer.
2. Retrieve cloud resource access keys (AKSK).
3. Clarify the execution environment of the tool.
The offline research tool needs to be installed and run on servers, which should maintain network connectivity with the Internet to ensure smooth API calls for resource scanning. The tool requires at least a 2C4G machine specification. The operating system requirements are mainstream Linux distributions (CentOS 7 is preferred) or macOS.
Notes:
When it is a macOS, the file needs to add security authorization. The path is: System Preferences > Privacy and Security.
You can first download it locally and then upload it to a server where the tool can be deployed for execution, or directly download it on the server through the link:
3.1 Select the source platform and system version to be scanned and downloaded via interface.
3.2 Upload the downloaded installation package to the target server, or download directly.
wget https://msp-release-1258344699.cos.ap-shanghai.myqcloud.com/package/urp/aws-scanner-linux-1.0.0.tar.gztar -xzvf aws-scanner-linux-1.0.0.tar.gz
The directory structure after decompressing is as follows:
mspcli├── ReadMe.txt # Tool instructions file├── config.yaml # Parameter configuration file├── aws-scanner # Collection agent file
3.3 Prepare the parameter file. You can prepare multiple parameter files in advance for backup, but only the configuration file named config.yaml in the same-level directory as aws-scanner will be effective.
# SecretIdSecretId: *********# SecretKeySecretKey: *****************# Region to be scanned, multiple regions are separated by commas. region can be not specified, and all regions of the current product will be automatically obtained for scanning.# List of region names: https://docs.aws.amazon.com/zh_cn/AWSEC2/latest/UserGuide/using-regions-availability-zones.html#concepts-available-regionsRegions:# Multiple products are separated by commas. Product support: do not fill in, and automatically obtain all products for scanning.# apigateway,cloudfront, dynamodb, ec2, ecr, efs, eks, elasticache,# elb, emr, es, kafka, mq, s3, sns, vpc, vpn, rdsProducts: ec2
Notes:
Fill in the correct key information. The key will only be used for verification when calling the API and will not be saved by the tool.
Enter a space after the colon in the configuration item, and then input the corresponding value. Multiple values are separated by commas. When the Regions and Products configuration items are empty, all regions and scannable products will be scanned by default.
The configuration file needs to be in the same-level directory as the scanning program (for example, aws-scanner).
Tool Execution
After confirming the environment and after installation, you can execute xxx-scanner to collect data. The execution command and results are calculated and summarized as follows:
# Authorize the toolchmod +x aws-scanner# startup command./aws-scanner#console outputSwitched to the directory of the executable file: /home/ec2-userload configuration file: config.yamlGenerating research configuration in progress...Generate research configuration for product ec2Research configuration generation completed.Start researching cloud resourcesResource research completed. Product: ec2. Region: ap-southeast-1. Number of scanned resources: 1.Resource list exported successfully: aws_scan_20241008084938.xlsx
Notes:
When the selected platform is MacOS, please go to: System Preferences > Privacy and Security > Security. xxx has been blocked to protect MacOS. Select "Open Anyway" to authorize the file.
View Files
After the scan is completed, the following files will be generated in the same-level directory:
mspcli├── ReadMe.txt # Tool instructions fileconfig.yaml # Parameter configuration file├── aws-scanner # Collection program fileaws_scan_20241008084938.xlsx # Scanning result data├── generate_scan_config_log.json # Configuration file reading log├── mspcli.log # Execution log
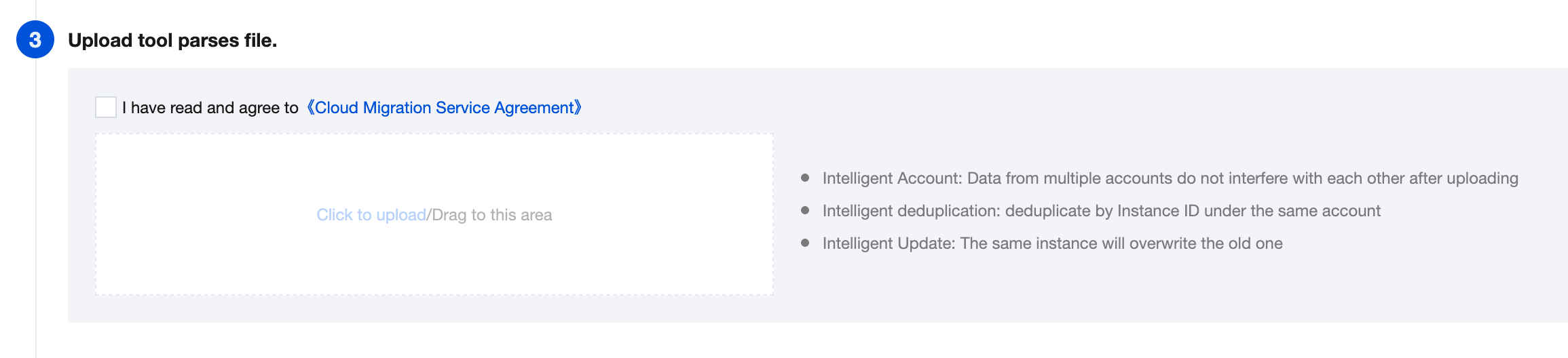
Upload Result File
After confirming that the local data is correct, you can upload the corresponding result file (xlsx format) to Cloud Migration (CMG).
Notes:
To correctly parse the data content, do not modify the result file.
Online Data Viewing
Click Go to resource list, and the imported data will be displayed in Source-end resource list of Research Analysis.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

