VPN Connections
- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Getting Started
- IPSec VPN
- Establishing a Connection Between VPC and IDC (SPD policy)
- Connecting VPC to IDC (Destination route)
- Operation Guide
- VPN Gateway
- IPSec VPN Gateway
- VPN Tunnel
- Customer Gateway
- SSL VPN Server
- SSL VPN Client
- Alarming and Monitoring
- SSL VPN Configuration Guide
- IPSec VPN Configuration Guide
- Practical Tutorial
- IPsec VPN
- Local Gateway Configurations
- Dedicated Private Network Traffic Encrypted Via a Private Network VPN Gateway
- Troubleshooting
- Service Agreement
DocumentationVPN ConnectionsPractical TutorialIPsec VPNConnect via Direct Connect or VPN Connection to Interconnect the Primary and Replica Links for Redundant Communication (Auto-Switch)
Connect via Direct Connect or VPN Connection to Interconnect the Primary and Replica Links for Redundant Communication (Auto-Switch)
Last updated: 2024-05-24 10:53:09
Connect via Direct Connect or VPN Connection to Interconnect the Primary and Replica Links for Redundant Communication (Auto-Switch)
Last updated: 2024-05-24 10:53:09
If your business is deployed in both a local IDC and a Tencent Cloud VPC, you can connect them via direct connect or VPN connection to interconnect the cloud and local services. To improve the business high availability, set up both direct connect and VPN connection businesses. Combined with CCN, configure them as the primary and replica links for redundant communication.
Note
Currently, the routing priority feature is in beta testing. If needed, you may Contact Us.
Currently, the routing priority cannot be adjusted in the console. If you want to adjust the routing priority, you may Contact Us.
When configuring primary and replica routings, the mask length of the direct connect IP range must be longer than that of the VPN IP range.
Business Scenario
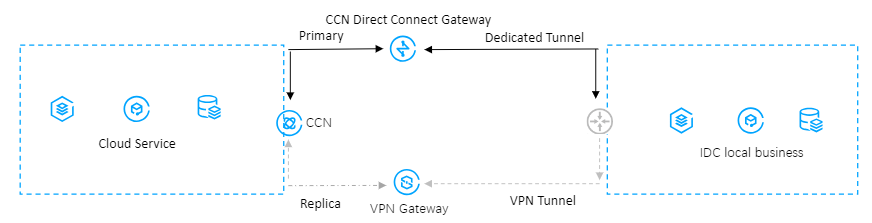
As shown below, you have deployed businesses in VPC and IDC. To interconnect them, user need to deploy network connection services for high-availability communications. When a fault occurs, business will be automatically switched. The deployment plan is as follows:
Direct Connect (primary): The local IDC is connected to a CCN-type direct connect gateway through the connection to establish the local and cloud business communication. When the connection link is normal, all data traffic between the IDC and the VPC is forwarded through the connection.
VPN Connection (replica): A CCN-type VPN security tunnel is established between the local IDC and the cloud VPC to establish the local and cloud business communication. When the direct connect link is abnormal, traffic will be forwarded using this link to ensure the business availability.
Prerequisites
Your local IDC gateway device should support the IPsec VPN feature, and can act as a user-side VPN gateway, to create a IPsec tunnel communication with the cloud-side VPN device.
The IDC-side gateway device has configured with a static IP.
A CCN instance has been created with ECMP and routing overlap features enabled. For more details, contact Technical Support.
The dynamic BGP propagation feature has been enabled on the direct connect. For more details, contact Technical Support.
Directions
Step One: Connecting IDC to Cloud Migration Through Direct Connect
1. Log in to the DC Console. Click connection in the left sidebar, and click Create to set up a connection. For details, see Applying for Connection.
2. Click Direct Connect Gateway in the left sidebar, and click Create to establish a CCN-type direct connect gateway. After creation, publish the IP range directed to CCN on the details. For detailed operations, see Creating a Direct Connect Gateway, Publishing IDC IP Ranges to CCN.
3. Click Dedicated Tunnels > Exclusive Dedicated Tunnels in the left sidebar, then click Create to set up an exclusive dedicated tunnel. Here, you will need to configure the tunnel name, select the direct connect type, the created direct connect gateway, and interconnect IP for both Tencent Cloud-side and user-side. Choose static routing for the routing method, and fill in the IDC communication IP range. Upon configuration, you can download the configuration guide and complete the setup on the IDC device. For detailed operations, see Exclusive Virtual Interface.
Note
Step Two: Connecting IDC to Cloud Migration Through a VPN Connection
1. Log in to the VPN Gateway Console. Click Create. For creating a CCN-type VPN Gateway, see Creating a VPN Gateway. After creation, associate a CCN instance on the details page. For detailed steps, see Associating a CCN Instance.
2. Click Customer Gateway in the left sidebar, and configure the customer gateway (i.e., the logical object of the IDC-side VPN gateway). Enter the public network IP address of the IDC-side VPN gateway. For example, 202.xx.xx.5. For detailed operations, see Creating Customer Gateways.
3. Click VPN Tunnel in the left sidebar, and click Create to set up a VPN tunnel. Follow page instructions to configure SPD policy, IKE, IPsec parameters. For detailed configuration information, see Creating a VPN Tunnel.
Configure the VPN tunnel information on the local gateway device at IDC. The configuration here needs to be consistent with the VPN tunnel information in Step 3. Otherwise, the VPN tunnel cannot connect properly.
Configure the routing pointing to the customer gateway in the routing table tab of the gateway.
Note
Step Three: Configuring Alarms
You can configure an alarm policy to detect exceptions in the links in time. When a link has an exception, alarm notifications are sent to you automatically via emails and SMS messages. This makes you aware of the risks in advance.
1. Log in to the TCOP Alarm Policy Console.
2. Click Create, and enter the policy name. Choose private network/network probe for the policy type, and choose a specific network probe instance for the alarm object. Configure trigger conditions and notifications and click Complete to finish.
Step Four: Switching Primary and Replica Routing
When an anomaly alarm for the direct connect gateway's primary path is received, your traffic will automatically be switched to the replica routing on the VPN gateway.
If the primary direct connect returns to normal, you will need to manually switch the traffic back to the direct connect gateway.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

