- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Security Dashboard
- Asset Overview
- Server List
- Asset Fingerprint
- Vulnerability Management
- Baseline Management
- Malicious File Scan
- Unusual Login
- Password Cracking
- Malicious Requests
- High-risk Commands
- Local Privilege Escalation
- Reverse Shell
- Java Webshell
- Critical File Monitor
- Network Attack
- A Ransomware Defense
- Log Analysis
- License Management
- Cloud Access Management
- Hybrid Cloud Installation Guide
- FAQs for Beginners
- Cloud Workload Protection Description
- Practical Tutorial
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Asset Management APIs
- DescribeAssetMachineList
- DescribeAssetMachineDetail
- DescribeAssetUserList
- DescribeAssetUserInfo
- DescribeAssetPortInfoList
- DescribeAssetProcessInfoList
- DescribeAssetAppList
- DescribeAssetAppProcessList
- DescribeAssetDatabaseList
- DescribeAssetDatabaseInfo
- DescribeAssetWebAppList
- DescribeAssetWebServiceInfoList
- DescribeAssetWebAppPluginList
- DescribeAssetWebServiceProcessList
- DescribeAssetWebFrameList
- DescribeAssetWebLocationList
- DescribeAssetWebLocationInfo
- DescribeAssetJarList
- DescribeAssetJarInfo
- DescribeAssetInitServiceList
- DescribeAssetPlanTaskList
- DescribeAssetCoreModuleList
- DescribeAssetCoreModuleInfo
- DescribeAssetSystemPackageList
- SyncAssetScan
- DescribeAssetRecentMachineInfo
- DescribeAssetMachineTagTop
- DescribeAssetLoadInfo
- DescribeAssetTypeTop
- ExportAssetRecentMachineInfo
- DescribeMachineGeneral
- DescribeMachineRegions
- DescribeMachineOsList
- DescribeMachineLicenseDetail
- DescribeMachinesSimple
- DescribeDirectConnectInstallCommand
- DescribeAgentInstallationToken
- RemoveMachine
- DescribeHostInfo
- EditTags
- DescribeTags
- DeleteTags
- DeleteMachineTag
- UpdateMachineTags
- DescribeTagMachines
- ExportAssetUserList
- DescribeAssetUserCount
- ExportAssetMachineList
- ExportAssetMachineDetail
- DescribeAssetPortCount
- ExportAssetPortInfoList
- DescribeAssetProcessCount
- DescribeProcessStatistics
- ExportAssetProcessInfoList
- DescribeAssetAppCount
- ExportAssetAppList
- DescribeAssetDatabaseCount
- ExportAssetDatabaseList
- DescribeAssetWebAppCount
- ExportAssetWebAppList
- DescribeAssetWebServiceCount
- ExportAssetWebServiceInfoList
- DescribeAssetWebLocationCount
- ExportAssetWebLocationList
- DescribeAssetWebLocationPathList
- DescribeAssetWebFrameCount
- ExportAssetWebFrameList
- ExportAssetCoreModuleList
- DescribeAssetDiskList
- DescribeFileTamperRules
- DescribeMachineFileTamperRules
- ExportAssetEnvList
- DescribeAssetHostTotalCount
- DescribeAssetTotalCount
- ExportAssetInitServiceList
- ExportAssetJarList
- ExportAssetPlanTaskList
- ExportAssetSystemPackageList
- DescribeAssetUserKeyList
- DescribeHistoryAccounts
- DescribeAccountStatistics
- DeleteMachineClearHistory
- DescribeAssetInfo
- ModifyMachineAutoClearConfig
- DescribeExportMachines
- DescribeMachineClearHistory
- CreateIncidentBacktracking
- DescribeMachineRegionList
- DescribeProcesses
- DescribeProcessTaskStatus
- DescribeComponents
- DescribeComponentInfo
- DescribeAccounts
- CreateProcessTask
- DescribeOpenPortTaskStatus
- AddMachineTag
- CreateOpenPortTask
- Virus Scanning APIs
- DescribeMalWareList
- DescribeMalwareInfo
- DescribeMalwareWhiteList
- DescribeNetAttackWhiteList
- DescribeMalwareWhiteListAffectList
- DeleteMalwareWhiteList
- DeleteNetAttackWhiteList
- DescribeMalwareFile
- CreateScanMalwareSetting
- DeleteMalwareScanTask
- DescribeScanMalwareSchedule
- DescribeMalwareRiskWarning
- ModifyMalwareTimingScanSettings
- DescribeMalwareTimingScanSetting
- DescribeServersAndRiskAndFirstInfo
- DescribeVulDefenceSetting
- DescribeVulDefencePluginExceptionCount
- DescribeVulDefenceOverview
- DescribeJavaMemShellList
- ModifyJavaMemShellsStatus
- DescribeJavaMemShellPluginList
- DeleteAllJavaMemShells
- DescribeJavaMemShellInfo
- DescribeJavaMemShellPluginInfo
- ModifyJavaMemShellPluginSwitch
- CreateMalwareWhiteList
- CreateNetAttackWhiteList
- DescribeMalwareRiskOverview
- DescribeRiskProcessEvents
- ModifyMalwareWhiteList
- ModifyNetAttackWhiteList
- ExportJavaMemShellPlugins
- ExportJavaMemShells
- ExportRiskProcessEvents
- Abnormal Log-in APIs
- Password Cracking APIs
- Malicious Request APIs
- DescribeRiskDnsList
- CreateMaliciousRequestWhiteList
- ModifyMaliciousRequestWhiteList
- DeleteMaliciousRequestWhiteList
- DescribeMaliciousRequestWhiteList
- DeleteRiskDnsEvent
- DeleteRiskDnsPolicy
- DescribeRiskDnsEventInfo
- DescribeRiskDnsEventList
- DescribeRiskDnsPolicyList
- ExportRiskDnsPolicyList
- ModifyRiskDnsPolicy
- ModifyRiskDnsPolicyStatus
- DescribeRiskDnsInfo
- ExportRiskDnsEventList
- High-Risk Command APIs
- DescribeBashEvents
- DescribeBashEventsNew
- SetBashEventsStatus
- DeleteBashEvents
- DescribeBashPolicies
- DescribeBashRules
- EditBashRules
- ModifyBashPolicy
- DeleteBashPolicies
- DeleteBashRules
- ModifyBashPolicyStatus
- SwitchBashRules
- CheckBashPolicyParams
- CheckBashRuleParams
- DescribeBashEventsInfo
- DescribeBashEventsInfoNew
- ExportBashEvents
- ExportBashEventsNew
- ExportBashPolicies
- Local Privilege Escalation APIs
- Reverse Shell APIs
- Vulnerability Management APIs
- ScanVul
- DescribeScanSchedule
- ScanVulAgain
- DescribeVdbAndPocInfo
- DescribeVulEmergentMsg
- DescribeVulTop
- DescribeVulHostTop
- DescribeVulHostCountScanTime
- DescribeUndoVulCounts
- DescribeVulCountByDates
- DescribeVulLevelCount
- ExportVulList
- CreateEmergencyVulScan
- DescribeVulCveIdInfo
- DescribeVulInfoCvss
- DescribeVulEffectHostList
- DescribeVulEffectModules
- ExportVulEffectHostList
- ExportVulInfo
- IgnoreImpactedHosts
- CancelIgnoreVul
- ExportVulDetectionReport
- ModifyVulDefenceSetting
- ExportVulDefencePluginEvent
- DescribeVulDefencePluginDetail
- DescribeVulDefenceEvent
- ExportVulDefenceEvent
- ModifyVulDefenceEventStatus
- DescribeDefenceEventDetail
- CreateVulFix
- DescribeCanFixVulMachine
- DescribeMachineSnapshot
- DescribeVulDefenceList
- DescribeVulFixStatus
- ExportVulDefenceList
- RetryCreateSnapshot
- RetryVulFix
- DescribeScanVulSetting
- ScanVulSetting
- DescribeEmergencyVulList
- DescribeVulDefencePluginStatus
- ExportVulDetectionExcel
- DescribeVulList
- RescanImpactedHost
- DescribeVuls
- DescribeVulScanResult
- DescribeVulInfo
- DescribeImpactedHosts
- DescribeAgentVuls
- New Baseline Management APIs
- DeleteBaselinePolicy
- DescribeBaselineHostDetectList
- DescribeBaselineItemDetectList
- DescribeBaselineItemList
- DescribeBaselinePolicyList
- DescribeBaselineWeakPasswordList
- DescribeIgnoreHostAndItemConfig
- ExportBaselineFixList
- ExportBaselineHostDetectList
- ExportBaselineItemDetectList
- StartBaselineDetect
- StopBaselineDetect
- SyncBaselineDetectSummary
- DescribeHotVulTop
- DescribeVulStoreList
- ModifyBaselinePolicy
- Baseline Management APIs
- DescribeBaselineTop
- DescribeBaselineHostTop
- DescribeBaselineDefaultStrategyList
- CreateBaselineStrategy
- DescribeStrategyExist
- UpdateBaselineStrategy
- DeleteBaselineStrategy
- DescribeBaselineStrategyList
- DescribeBaselineStrategyDetail
- DescribeBaselineBasicInfo
- DescribeBaselineEffectHostList
- DescribeBaselineList
- DescribeBaselineDetail
- ScanBaseline
- DescribeBaselineScanSchedule
- CheckFirstScanBaseline
- ChangeStrategyEnableStatus
- ChangeRuleEventsIgnoreStatus
- DescribeIgnoreBaselineRule
- DescribeIgnoreRuleEffectHostList
- DescribeBaselineRule
- ExportBaselineEffectHostList
- ExportBaselineList
- ExportIgnoreBaselineRule
- ExportIgnoreRuleEffectHostList
- Advanced Defense APIs
- DescribeAttackEvents
- DescribeMachineDefenseCnt
- DescribeMachineRiskCnt
- ExportFileTamperEvents
- DescribeAttackVulTypeList
- DescribeVulLabels
- DescribeVulOverview
- CheckFileTamperRule
- DescribeRansomDefenseBackupList
- DescribeRansomDefenseEventsList
- DescribeRansomDefenseMachineList
- DescribeRansomDefenseRollBackTaskList
- DescribeRansomDefenseStrategyMachines
- ModifyWebPageProtectSwitch
- ModifyFileTamperEvents
- ModifyFileTamperRuleStatus
- DescribeFileTamperEventRuleInfo
- DescribeFileTamperRuleCount
- DescribeFileTamperRuleInfo
- ModifyRansomDefenseEventsStatus
- DescribeFileTamperEvents
- DescribeRansomDefenseStrategyList
- ExportRansomDefenseBackupList
- ExportRansomDefenseEventsList
- ExportRansomDefenseMachineList
- ExportRansomDefenseStrategyList
- ExportRansomDefenseStrategyMachines
- ModifyFileTamperRule
- ExportFileTamperRules
- ModifyNetAttackSetting
- DescribeAttackEventInfo
- DescribeAttackStatistics
- DescribeAttackTop
- DescribeAttackTrends
- DescribeNetAttackSetting
- ExportAttackEvents
- CreateRansomDefenseStrategy
- Security Operation APIs
- Expert Service APIs
- Other APIs
- DescribeOpenPortStatistics
- DeleteMachine
- DeleteNonlocalLoginPlaces
- DescribeUsualLoginPlaces
- DeleteBruteAttacks
- DescribeSecurityBroadcastInfo
- DescribeLogStorageConfig
- DescribeLogStorageRecord
- ModifyLogStorageConfig
- DescribeTrialReport
- DescribeAssetEnvList
- DescribeABTestConfig
- DescribeRiskBatchStatus
- ExportTasks
- DescribeGeneralStat
- DescribeScreenGeneralStat
- DescribeVersionStatistics
- DescribeSafeInfo
- DescribeRansomDefenseMachineStrategyInfo
- DescribeRansomDefenseState
- DescribeRansomDefenseStrategyDetail
- DescribeRansomDefenseTrend
- DescribeSecurityEventStat
- ModifyRansomDefenseStrategyStatus
- RansomDefenseRollback
- DescribeScreenAttackHotspot
- DescribeScreenBroadcasts
- DescribeScreenDefenseTrends
- DescribeScreenEmergentMsg
- DescribeScreenEventsCnt
- DescribeScreenHostInvasion
- DescribeScreenMachineRegions
- DescribeScreenMachines
- DescribeScreenProtectionCnt
- DescribeScreenRiskAssetsTop
- DescribeSecurityEventsCnt
- ExportSecurityTrends
- DescribeScanTaskDetails
- DescribeScanState
- DeleteScanTask
- DescribeScanTaskStatus
- ScanTaskAgain
- DescribeAgentInstallCommand
- DescribePublicProxyInstallCommand
- DescribeVersionCompareChart
- CreateBuyBindTask
- SyncMachines
- CheckLogKafkaConnectionState
- CreateLogExport
- DeleteLogExport
- DescribeAESKey
- DescribeAssetTypes
- DescribeCanNotSeparateMachine
- DescribeClientException
- DescribeFastAnalysis
- DescribeLogDeliveryKafkaOptions
- DescribeLogExports
- DescribeLogHistogram
- DescribeLogIndex
- DescribeLogKafkaDeliverInfo
- DescribeScreenProtectionStat
- DescribeWarningHostConfig
- ModifyLogKafkaAccess
- ModifyLogKafkaDeliverType
- ModifyLogKafkaState
- ModifyEventAttackStatus
- ModifyRiskEventsStatus
- ModifyWarningHostConfig
- SearchLog
- StopAssetScan
- ClearLocalStorage
- DescribeLicenseWhiteConfig
- DescribeProductStatus
- GetLocalStorageItem
- KeysLocalStorage
- RemoveLocalStorageItem
- SetLocalStorageExpire
- SetLocalStorageItem
- DescribeVulTrend
- ExportScanTaskDetails
- DescribeAlarmIncidentNodes
- DescribeAlarmVertexId
- DescribeEventByTable
- DescribeProVersionStatus
- DescribeVertexDetail
- DeleteWebHookPolicy
- DeleteWebHookReceiver
- DescribeRecommendedProtectCpu
- DescribeUsersConfig
- DescribeWebHookPolicy
- DescribeWebHookReceiver
- DescribeWebHookReceiverUsage
- ModifyUsersConfig
- ModifyWebHookPolicy
- ModifyWebHookPolicyStatus
- ModifyWebHookReceiver
- DeleteUsualLoginPlaces
- CreateUsualLoginPlaces
- CloseProVersion
- DescribeWeeklyReports
- DescribeWeeklyReportVuls
- DescribeWeeklyReportNonlocalLoginPlaces
- DescribeWeeklyReportMalwares
- DescribeWeeklyReportInfo
- DescribeWeeklyReportBruteAttacks
- DescribeOpenPorts
- RenewProVersion
- OpenProVersionPrepaid
- ModifyProVersionRenewFlag
- InquiryPriceOpenProVersionPrepaid
- OpenProVersion
- Overview Statistics APIs
- Settings Center APIs
- DescribeProVersionInfo
- DescribeWarningList
- ModifyWarningSetting
- ModifyAutoOpenProVersionConfig
- DescribeLicenseGeneral
- DescribeLicenseList
- DeleteLicenseRecord
- DescribeLicenseBindList
- ModifyLicenseBinds
- DescribeLicenseBindSchedule
- CreateLicenseOrder
- DeleteLicenseRecordAll
- DestroyOrder
- CreateWhiteListOrder
- DeleteWebHookRule
- DescribeLicense
- DescribeWebHookRule
- DescribeWebHookRules
- ExportLicenseDetail
- ModifyWebHookRule
- ModifyWebHookRuleStatus
- TestWebHookRule
- ModifyLicenseOrder
- DescribeAlarmAttribute
- Making API Requests
- Intrusion Detection APIs
- DeleteMalwares
- TrustMalwares
- UntrustMalwares
- SeparateMalwares
- RecoverMalwares
- ExportMalwares
- DescribeLoginWhiteList
- DeleteLoginWhiteList
- ExportNonlocalLoginPlaces
- ExportBruteAttacks
- DeleteMaliciousRequests
- ExportMaliciousRequests
- MisAlarmNonlocalLoginPlaces
- DescribeNonlocalLoginPlaces
- DescribeMalwares
- DescribeBruteAttacks
- UntrustMaliciousRequest
- TrustMaliciousRequest
- DescribeMaliciousRequests
- ModifyLoginWhiteList
- AddLoginWhiteList
- Data Types
- Error Codes
- FAQs
- Agreements
- Contact Us
- Glossary
- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Security Dashboard
- Asset Overview
- Server List
- Asset Fingerprint
- Vulnerability Management
- Baseline Management
- Malicious File Scan
- Unusual Login
- Password Cracking
- Malicious Requests
- High-risk Commands
- Local Privilege Escalation
- Reverse Shell
- Java Webshell
- Critical File Monitor
- Network Attack
- A Ransomware Defense
- Log Analysis
- License Management
- Cloud Access Management
- Hybrid Cloud Installation Guide
- FAQs for Beginners
- Cloud Workload Protection Description
- Practical Tutorial
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Asset Management APIs
- DescribeAssetMachineList
- DescribeAssetMachineDetail
- DescribeAssetUserList
- DescribeAssetUserInfo
- DescribeAssetPortInfoList
- DescribeAssetProcessInfoList
- DescribeAssetAppList
- DescribeAssetAppProcessList
- DescribeAssetDatabaseList
- DescribeAssetDatabaseInfo
- DescribeAssetWebAppList
- DescribeAssetWebServiceInfoList
- DescribeAssetWebAppPluginList
- DescribeAssetWebServiceProcessList
- DescribeAssetWebFrameList
- DescribeAssetWebLocationList
- DescribeAssetWebLocationInfo
- DescribeAssetJarList
- DescribeAssetJarInfo
- DescribeAssetInitServiceList
- DescribeAssetPlanTaskList
- DescribeAssetCoreModuleList
- DescribeAssetCoreModuleInfo
- DescribeAssetSystemPackageList
- SyncAssetScan
- DescribeAssetRecentMachineInfo
- DescribeAssetMachineTagTop
- DescribeAssetLoadInfo
- DescribeAssetTypeTop
- ExportAssetRecentMachineInfo
- DescribeMachineGeneral
- DescribeMachineRegions
- DescribeMachineOsList
- DescribeMachineLicenseDetail
- DescribeMachinesSimple
- DescribeDirectConnectInstallCommand
- DescribeAgentInstallationToken
- RemoveMachine
- DescribeHostInfo
- EditTags
- DescribeTags
- DeleteTags
- DeleteMachineTag
- UpdateMachineTags
- DescribeTagMachines
- ExportAssetUserList
- DescribeAssetUserCount
- ExportAssetMachineList
- ExportAssetMachineDetail
- DescribeAssetPortCount
- ExportAssetPortInfoList
- DescribeAssetProcessCount
- DescribeProcessStatistics
- ExportAssetProcessInfoList
- DescribeAssetAppCount
- ExportAssetAppList
- DescribeAssetDatabaseCount
- ExportAssetDatabaseList
- DescribeAssetWebAppCount
- ExportAssetWebAppList
- DescribeAssetWebServiceCount
- ExportAssetWebServiceInfoList
- DescribeAssetWebLocationCount
- ExportAssetWebLocationList
- DescribeAssetWebLocationPathList
- DescribeAssetWebFrameCount
- ExportAssetWebFrameList
- ExportAssetCoreModuleList
- DescribeAssetDiskList
- DescribeFileTamperRules
- DescribeMachineFileTamperRules
- ExportAssetEnvList
- DescribeAssetHostTotalCount
- DescribeAssetTotalCount
- ExportAssetInitServiceList
- ExportAssetJarList
- ExportAssetPlanTaskList
- ExportAssetSystemPackageList
- DescribeAssetUserKeyList
- DescribeHistoryAccounts
- DescribeAccountStatistics
- DeleteMachineClearHistory
- DescribeAssetInfo
- ModifyMachineAutoClearConfig
- DescribeExportMachines
- DescribeMachineClearHistory
- CreateIncidentBacktracking
- DescribeMachineRegionList
- DescribeProcesses
- DescribeProcessTaskStatus
- DescribeComponents
- DescribeComponentInfo
- DescribeAccounts
- CreateProcessTask
- DescribeOpenPortTaskStatus
- AddMachineTag
- CreateOpenPortTask
- Virus Scanning APIs
- DescribeMalWareList
- DescribeMalwareInfo
- DescribeMalwareWhiteList
- DescribeNetAttackWhiteList
- DescribeMalwareWhiteListAffectList
- DeleteMalwareWhiteList
- DeleteNetAttackWhiteList
- DescribeMalwareFile
- CreateScanMalwareSetting
- DeleteMalwareScanTask
- DescribeScanMalwareSchedule
- DescribeMalwareRiskWarning
- ModifyMalwareTimingScanSettings
- DescribeMalwareTimingScanSetting
- DescribeServersAndRiskAndFirstInfo
- DescribeVulDefenceSetting
- DescribeVulDefencePluginExceptionCount
- DescribeVulDefenceOverview
- DescribeJavaMemShellList
- ModifyJavaMemShellsStatus
- DescribeJavaMemShellPluginList
- DeleteAllJavaMemShells
- DescribeJavaMemShellInfo
- DescribeJavaMemShellPluginInfo
- ModifyJavaMemShellPluginSwitch
- CreateMalwareWhiteList
- CreateNetAttackWhiteList
- DescribeMalwareRiskOverview
- DescribeRiskProcessEvents
- ModifyMalwareWhiteList
- ModifyNetAttackWhiteList
- ExportJavaMemShellPlugins
- ExportJavaMemShells
- ExportRiskProcessEvents
- Abnormal Log-in APIs
- Password Cracking APIs
- Malicious Request APIs
- DescribeRiskDnsList
- CreateMaliciousRequestWhiteList
- ModifyMaliciousRequestWhiteList
- DeleteMaliciousRequestWhiteList
- DescribeMaliciousRequestWhiteList
- DeleteRiskDnsEvent
- DeleteRiskDnsPolicy
- DescribeRiskDnsEventInfo
- DescribeRiskDnsEventList
- DescribeRiskDnsPolicyList
- ExportRiskDnsPolicyList
- ModifyRiskDnsPolicy
- ModifyRiskDnsPolicyStatus
- DescribeRiskDnsInfo
- ExportRiskDnsEventList
- High-Risk Command APIs
- DescribeBashEvents
- DescribeBashEventsNew
- SetBashEventsStatus
- DeleteBashEvents
- DescribeBashPolicies
- DescribeBashRules
- EditBashRules
- ModifyBashPolicy
- DeleteBashPolicies
- DeleteBashRules
- ModifyBashPolicyStatus
- SwitchBashRules
- CheckBashPolicyParams
- CheckBashRuleParams
- DescribeBashEventsInfo
- DescribeBashEventsInfoNew
- ExportBashEvents
- ExportBashEventsNew
- ExportBashPolicies
- Local Privilege Escalation APIs
- Reverse Shell APIs
- Vulnerability Management APIs
- ScanVul
- DescribeScanSchedule
- ScanVulAgain
- DescribeVdbAndPocInfo
- DescribeVulEmergentMsg
- DescribeVulTop
- DescribeVulHostTop
- DescribeVulHostCountScanTime
- DescribeUndoVulCounts
- DescribeVulCountByDates
- DescribeVulLevelCount
- ExportVulList
- CreateEmergencyVulScan
- DescribeVulCveIdInfo
- DescribeVulInfoCvss
- DescribeVulEffectHostList
- DescribeVulEffectModules
- ExportVulEffectHostList
- ExportVulInfo
- IgnoreImpactedHosts
- CancelIgnoreVul
- ExportVulDetectionReport
- ModifyVulDefenceSetting
- ExportVulDefencePluginEvent
- DescribeVulDefencePluginDetail
- DescribeVulDefenceEvent
- ExportVulDefenceEvent
- ModifyVulDefenceEventStatus
- DescribeDefenceEventDetail
- CreateVulFix
- DescribeCanFixVulMachine
- DescribeMachineSnapshot
- DescribeVulDefenceList
- DescribeVulFixStatus
- ExportVulDefenceList
- RetryCreateSnapshot
- RetryVulFix
- DescribeScanVulSetting
- ScanVulSetting
- DescribeEmergencyVulList
- DescribeVulDefencePluginStatus
- ExportVulDetectionExcel
- DescribeVulList
- RescanImpactedHost
- DescribeVuls
- DescribeVulScanResult
- DescribeVulInfo
- DescribeImpactedHosts
- DescribeAgentVuls
- New Baseline Management APIs
- DeleteBaselinePolicy
- DescribeBaselineHostDetectList
- DescribeBaselineItemDetectList
- DescribeBaselineItemList
- DescribeBaselinePolicyList
- DescribeBaselineWeakPasswordList
- DescribeIgnoreHostAndItemConfig
- ExportBaselineFixList
- ExportBaselineHostDetectList
- ExportBaselineItemDetectList
- StartBaselineDetect
- StopBaselineDetect
- SyncBaselineDetectSummary
- DescribeHotVulTop
- DescribeVulStoreList
- ModifyBaselinePolicy
- Baseline Management APIs
- DescribeBaselineTop
- DescribeBaselineHostTop
- DescribeBaselineDefaultStrategyList
- CreateBaselineStrategy
- DescribeStrategyExist
- UpdateBaselineStrategy
- DeleteBaselineStrategy
- DescribeBaselineStrategyList
- DescribeBaselineStrategyDetail
- DescribeBaselineBasicInfo
- DescribeBaselineEffectHostList
- DescribeBaselineList
- DescribeBaselineDetail
- ScanBaseline
- DescribeBaselineScanSchedule
- CheckFirstScanBaseline
- ChangeStrategyEnableStatus
- ChangeRuleEventsIgnoreStatus
- DescribeIgnoreBaselineRule
- DescribeIgnoreRuleEffectHostList
- DescribeBaselineRule
- ExportBaselineEffectHostList
- ExportBaselineList
- ExportIgnoreBaselineRule
- ExportIgnoreRuleEffectHostList
- Advanced Defense APIs
- DescribeAttackEvents
- DescribeMachineDefenseCnt
- DescribeMachineRiskCnt
- ExportFileTamperEvents
- DescribeAttackVulTypeList
- DescribeVulLabels
- DescribeVulOverview
- CheckFileTamperRule
- DescribeRansomDefenseBackupList
- DescribeRansomDefenseEventsList
- DescribeRansomDefenseMachineList
- DescribeRansomDefenseRollBackTaskList
- DescribeRansomDefenseStrategyMachines
- ModifyWebPageProtectSwitch
- ModifyFileTamperEvents
- ModifyFileTamperRuleStatus
- DescribeFileTamperEventRuleInfo
- DescribeFileTamperRuleCount
- DescribeFileTamperRuleInfo
- ModifyRansomDefenseEventsStatus
- DescribeFileTamperEvents
- DescribeRansomDefenseStrategyList
- ExportRansomDefenseBackupList
- ExportRansomDefenseEventsList
- ExportRansomDefenseMachineList
- ExportRansomDefenseStrategyList
- ExportRansomDefenseStrategyMachines
- ModifyFileTamperRule
- ExportFileTamperRules
- ModifyNetAttackSetting
- DescribeAttackEventInfo
- DescribeAttackStatistics
- DescribeAttackTop
- DescribeAttackTrends
- DescribeNetAttackSetting
- ExportAttackEvents
- CreateRansomDefenseStrategy
- Security Operation APIs
- Expert Service APIs
- Other APIs
- DescribeOpenPortStatistics
- DeleteMachine
- DeleteNonlocalLoginPlaces
- DescribeUsualLoginPlaces
- DeleteBruteAttacks
- DescribeSecurityBroadcastInfo
- DescribeLogStorageConfig
- DescribeLogStorageRecord
- ModifyLogStorageConfig
- DescribeTrialReport
- DescribeAssetEnvList
- DescribeABTestConfig
- DescribeRiskBatchStatus
- ExportTasks
- DescribeGeneralStat
- DescribeScreenGeneralStat
- DescribeVersionStatistics
- DescribeSafeInfo
- DescribeRansomDefenseMachineStrategyInfo
- DescribeRansomDefenseState
- DescribeRansomDefenseStrategyDetail
- DescribeRansomDefenseTrend
- DescribeSecurityEventStat
- ModifyRansomDefenseStrategyStatus
- RansomDefenseRollback
- DescribeScreenAttackHotspot
- DescribeScreenBroadcasts
- DescribeScreenDefenseTrends
- DescribeScreenEmergentMsg
- DescribeScreenEventsCnt
- DescribeScreenHostInvasion
- DescribeScreenMachineRegions
- DescribeScreenMachines
- DescribeScreenProtectionCnt
- DescribeScreenRiskAssetsTop
- DescribeSecurityEventsCnt
- ExportSecurityTrends
- DescribeScanTaskDetails
- DescribeScanState
- DeleteScanTask
- DescribeScanTaskStatus
- ScanTaskAgain
- DescribeAgentInstallCommand
- DescribePublicProxyInstallCommand
- DescribeVersionCompareChart
- CreateBuyBindTask
- SyncMachines
- CheckLogKafkaConnectionState
- CreateLogExport
- DeleteLogExport
- DescribeAESKey
- DescribeAssetTypes
- DescribeCanNotSeparateMachine
- DescribeClientException
- DescribeFastAnalysis
- DescribeLogDeliveryKafkaOptions
- DescribeLogExports
- DescribeLogHistogram
- DescribeLogIndex
- DescribeLogKafkaDeliverInfo
- DescribeScreenProtectionStat
- DescribeWarningHostConfig
- ModifyLogKafkaAccess
- ModifyLogKafkaDeliverType
- ModifyLogKafkaState
- ModifyEventAttackStatus
- ModifyRiskEventsStatus
- ModifyWarningHostConfig
- SearchLog
- StopAssetScan
- ClearLocalStorage
- DescribeLicenseWhiteConfig
- DescribeProductStatus
- GetLocalStorageItem
- KeysLocalStorage
- RemoveLocalStorageItem
- SetLocalStorageExpire
- SetLocalStorageItem
- DescribeVulTrend
- ExportScanTaskDetails
- DescribeAlarmIncidentNodes
- DescribeAlarmVertexId
- DescribeEventByTable
- DescribeProVersionStatus
- DescribeVertexDetail
- DeleteWebHookPolicy
- DeleteWebHookReceiver
- DescribeRecommendedProtectCpu
- DescribeUsersConfig
- DescribeWebHookPolicy
- DescribeWebHookReceiver
- DescribeWebHookReceiverUsage
- ModifyUsersConfig
- ModifyWebHookPolicy
- ModifyWebHookPolicyStatus
- ModifyWebHookReceiver
- DeleteUsualLoginPlaces
- CreateUsualLoginPlaces
- CloseProVersion
- DescribeWeeklyReports
- DescribeWeeklyReportVuls
- DescribeWeeklyReportNonlocalLoginPlaces
- DescribeWeeklyReportMalwares
- DescribeWeeklyReportInfo
- DescribeWeeklyReportBruteAttacks
- DescribeOpenPorts
- RenewProVersion
- OpenProVersionPrepaid
- ModifyProVersionRenewFlag
- InquiryPriceOpenProVersionPrepaid
- OpenProVersion
- Overview Statistics APIs
- Settings Center APIs
- DescribeProVersionInfo
- DescribeWarningList
- ModifyWarningSetting
- ModifyAutoOpenProVersionConfig
- DescribeLicenseGeneral
- DescribeLicenseList
- DeleteLicenseRecord
- DescribeLicenseBindList
- ModifyLicenseBinds
- DescribeLicenseBindSchedule
- CreateLicenseOrder
- DeleteLicenseRecordAll
- DestroyOrder
- CreateWhiteListOrder
- DeleteWebHookRule
- DescribeLicense
- DescribeWebHookRule
- DescribeWebHookRules
- ExportLicenseDetail
- ModifyWebHookRule
- ModifyWebHookRuleStatus
- TestWebHookRule
- ModifyLicenseOrder
- DescribeAlarmAttribute
- Making API Requests
- Intrusion Detection APIs
- DeleteMalwares
- TrustMalwares
- UntrustMalwares
- SeparateMalwares
- RecoverMalwares
- ExportMalwares
- DescribeLoginWhiteList
- DeleteLoginWhiteList
- ExportNonlocalLoginPlaces
- ExportBruteAttacks
- DeleteMaliciousRequests
- ExportMaliciousRequests
- MisAlarmNonlocalLoginPlaces
- DescribeNonlocalLoginPlaces
- DescribeMalwares
- DescribeBruteAttacks
- UntrustMaliciousRequest
- TrustMaliciousRequest
- DescribeMaliciousRequests
- ModifyLoginWhiteList
- AddLoginWhiteList
- Data Types
- Error Codes
- FAQs
- Agreements
- Contact Us
- Glossary
This document describes how to use the Anti-Unusual Login feature.
Overview
When log-in behaviors from a server do not meet the allowlist criteria (common source IP, common username, common log-in location, and common log-in time), an unusual log-in alarm will be generated. If the source IP of the unusual log-in is an overseas IP (including Hong Kong (China), Macao (China), and Taiwan (China)) or a malicious IP from threat intelligence, it will be marked as High-risk. Otherwise, it will be marked as Suspicious.
Important Notes
Hosts with CWPP agent installed (client online) will have unusual log-in behaviors monitored in real-time.
The CWPP console only retains the unusual login events for the last 6 months, and the event data generated 6 months ago is not displayed.
Operation Guide
1. Log in to the CWPP console.
2. Click Intrusion Detection > Unusual Login on the left sidebar. The fields and operations related to the feature are described as follows.
Event List
In the Event List, you can view and handle unusual login risks detected by CWPP.
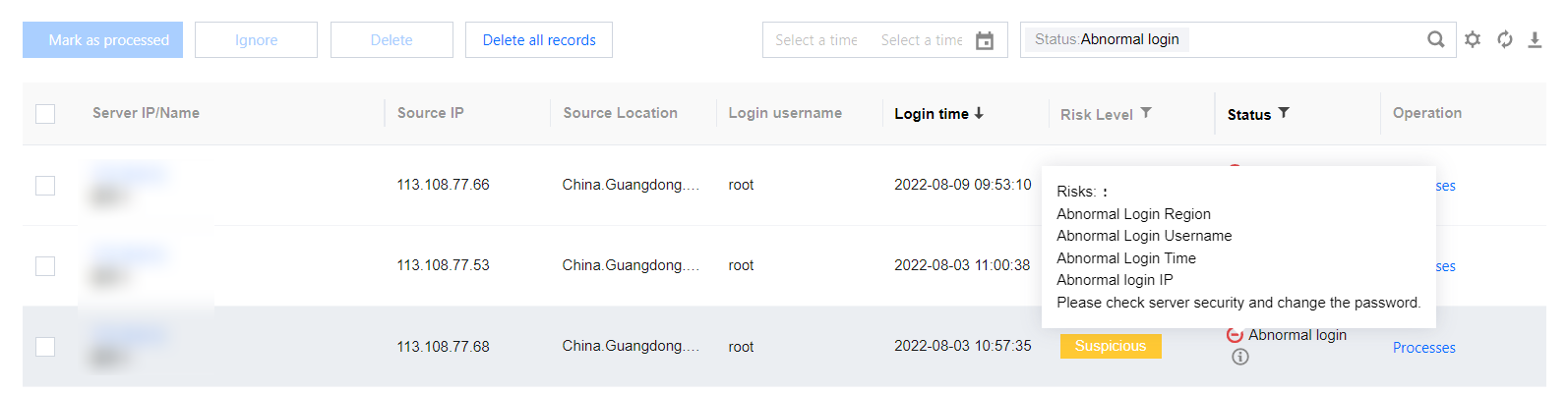
Field description:
Server IP/Name: The target server of the unusual login attempt.
Source IP: Source IP of the unusual login attempt, which generally is an egress IP of a company's network or a proxy IP.
Source Location: The location where the login source IP is located.
Login Username: The username used by the user who successfully logged in to the server.
Login Time: The time when the user successfully logged in to the server (The time shown on the server).
Threat Level: Suspicious/High.
Status
Unusual Login: A login attempt from an unusual location, with an unusual user name, at an unusual time, or from an unusual IP.
Allowlisted: The login source has been added to the allowlist (login source IP, login username, login time, and usual login location).
Handled: The event has been handled manually and marked as Handled.
Ignored: This alarm event has been ignored.
Operation
Actions
Mark as processed: If the event has been handled manually, mark the event as "Handled".
Add to Allowlist: Once an event is added to the allowlist, no alarm will be sent if the same event occurs again.
Ignore: Only ignore this alarm event. If the same event occurs again, an alarm will be sent again.
Delete Record: Once deleted, the event record will no longer be displayed on the console and cannot be recovered.
Allowlist Management
In Allowlist Management, you can add/delete items to/from the allowlist of unusual logins, or check and edit the allowlist.
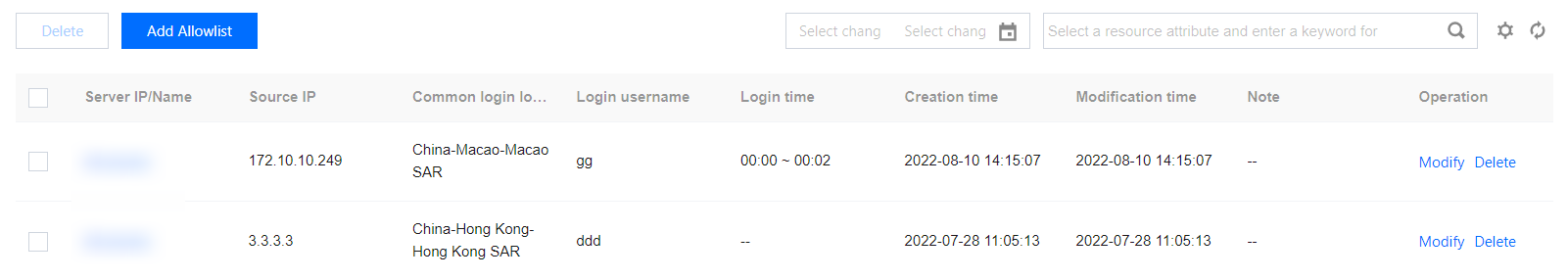
Field description:
Server IP/Name: The server on which the allowlist takes effect.
Source IP: The source IP added to the allowlist.
Usual Login Location: The login location added to the allowlist.
Login Username: The username added to the allowlist.
Login Time: The login time added to the allowlist.
Creation time: The time when the allowlist was created.
Update time: The time when the allowlist was last updated.
Operation
Edit: Re-edit the login source IP, login username, login time, usual login location, covered servers, etc.
Delete: Delete items from the allowlist.
FAQs
How to Process Unusual Log-in Alarms?
Determine whether the log-in behavior is self-initiated.
If it is your own log-in behavior and you do not want to see the alarm again, click Processing , and select Add to allowlist to configure common log-in source IP, log-in username, log-in location, log-in time, and effective range.
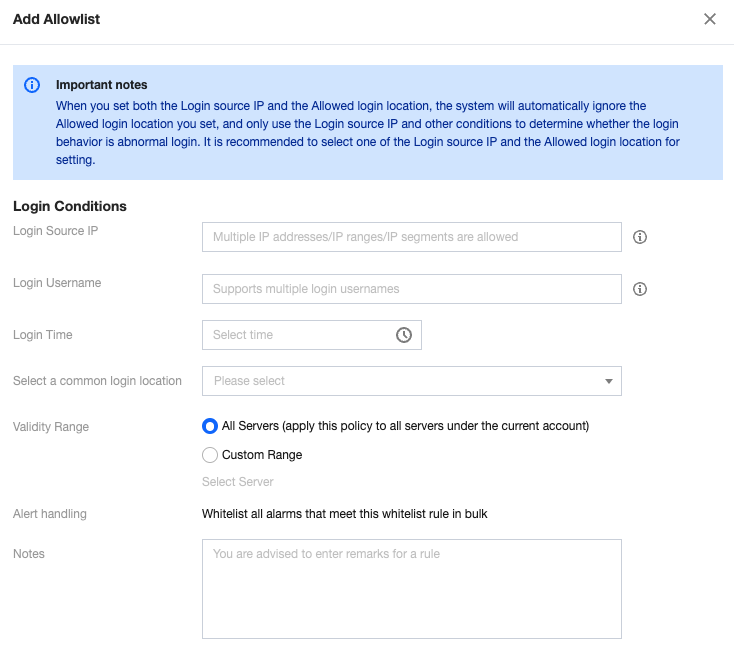
Field Description:
Empty Log-in Source IP: Indicates that log-in attempts from any source IP to the server will not trigger an alarm.
Empty Log-in Username: Indicates that log-in attempts with any username to the server will not trigger an alarm.
Empty Log-in Location: Indicates that log-in attempts from any location will not trigger an alarm.
Empty Log-in Time: Indicates that log-in attempts at any time will not trigger an alarm.
Note:
Log-in source IP, log-in username, log-in location, and log-in time cannot be empty at the same time.
If the log-in behavior is not from you, immediately change the server log-in password (it is recommended to be more than 10 characters, including uppercase and lowercase letters and special characters for a strong password.).
The server has been logged in abnormally, and the intruder might have already intruded your server and left malicious files. It is recommended to immediately perform malicious file scan, vulnerability detection, baseline detection to enhance your server's security.
How to Set an Allowlist to Meet Most Users' Needs?
Scenario 1: The source IP is a fixed IP segment. Users using any username can log in to the server from this segment without triggering abnormal log-in alarms.
You can enter the IP segment in the log-in source IP and select the effective server range.
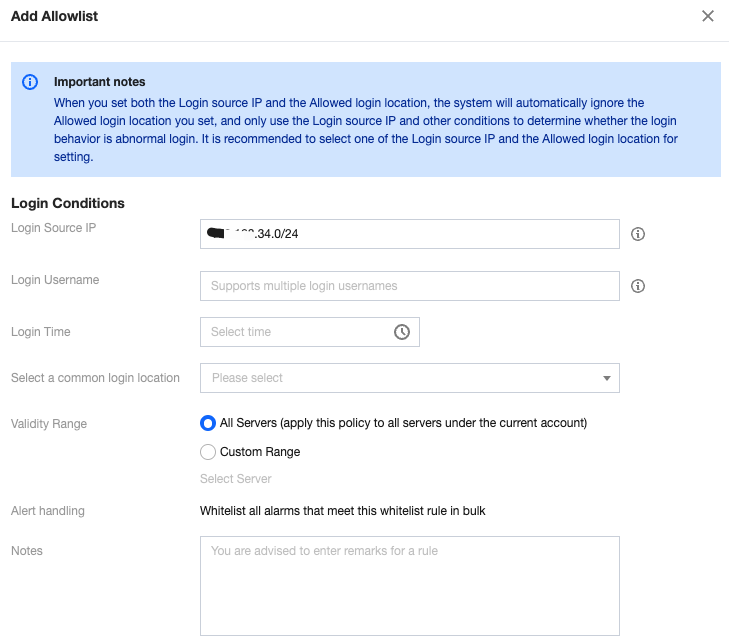
Scenario 2: The source IP is dynamic. Users from any location within Hong Kong (China) can log in to the server at any time using any username without triggering abnormal log-in alarms.
Select Hong Kong (China) Special Administrative Region in the list of common log-in locations and select the effective server range.
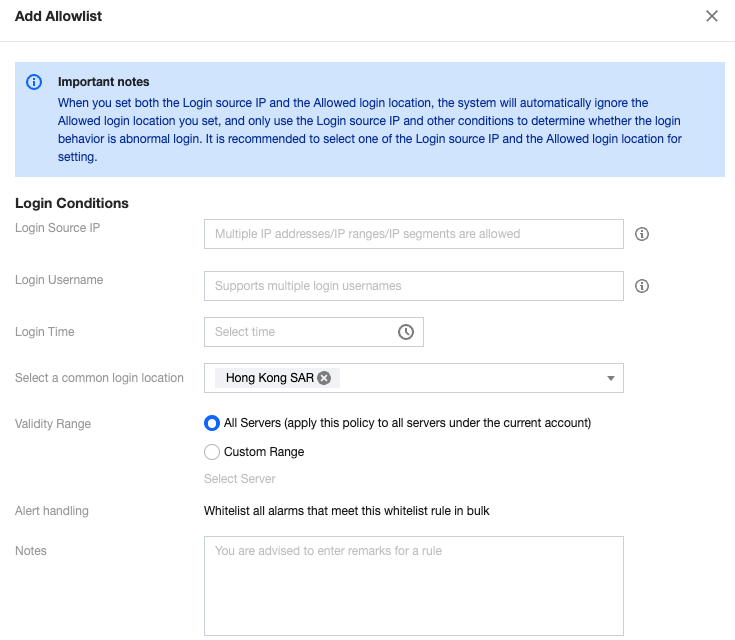
Note:
Combinations of log-in conditions are supported.
How to Disable Abnormal Log-in Alarms?
Go to alert settings to turn off the abnormal log-in alarm switch. If you keep the alarm switch on, it is recommended to select the high-risk option to only alarm on high-risk abnormal log-in behaviors.
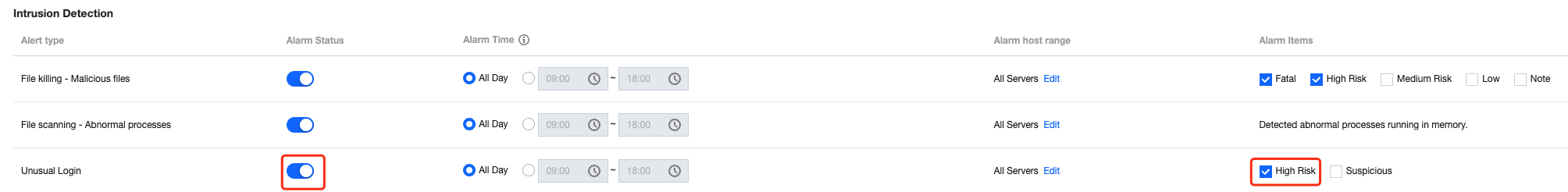

 Yes
Yes
 No
No
Was this page helpful?