监控规则配置
最后更新时间:2024-08-13 16:29:50
核心文件监控的监控规则分为系统规则和自定义规则。系统规则为腾讯主机安全运营专家与算法专家经过多模型沉淀的规则配置,适用于大部分的篡改用户配置监控需求,您也可以根据业务需要自定义规则,自定义规则支持编辑、复制和删除。
新增规则
1. 登录 主机安全控制台,在左侧导航栏,选择高级防御 > 核心文件监控 > 监控规则配置。
2. 在监控规则配置页面,单击左上角处的新增规则。
3. 在新增规则页面,依次配置基础设置、规则内容设置和生效服务器范围参数。
基础信息
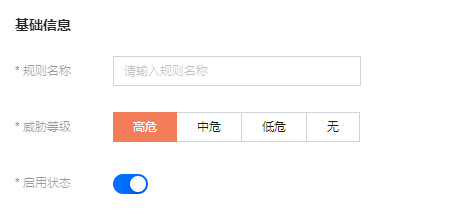
参数说明:
规则名称:自定义名称。
威胁等级:根据实际需求可选择高危、中危、低危或无。
启用状态:可启用或不启用该新增规则。
规则内容设置:单击添加规则,可添加多行,最大添加20行。
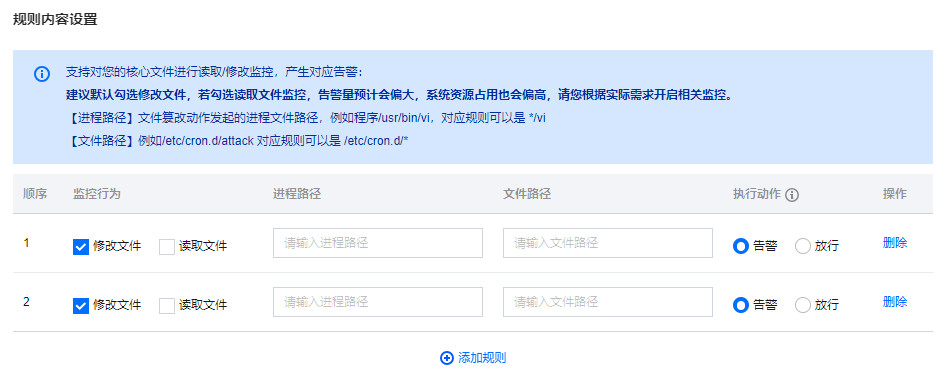
参数说明:
监控行为:修改文件/读取文件。
进程路径:文件篡改动作发起的进程文件路径,例如程序 /usr/bin/vi,对应规则可以是 */vi。
文件路径:例如 /etc/cron.d/attack 对应规则可以是 /etc/cron.d/*。
执行动作:告警指的是对文件系统变化产生自动告警事件,记录事件详情;放行指的是对文件系统变化产生事件进行放行操作,记录事件详情。
说明:
当告警放行进程路径及被访问文件一致,且生效服务器有重叠,重叠部分服务器不产生告警(即优先以放行条件为准)。
生效主机范围:可根据实际需求选择全部服务器或自选服务器。
4. 配置完成后,单击保存即可。
管理规则
编辑规则
1. 在 核心文件监控 > 监控规则配置页面,选择所需规则,单击操作列的编辑。
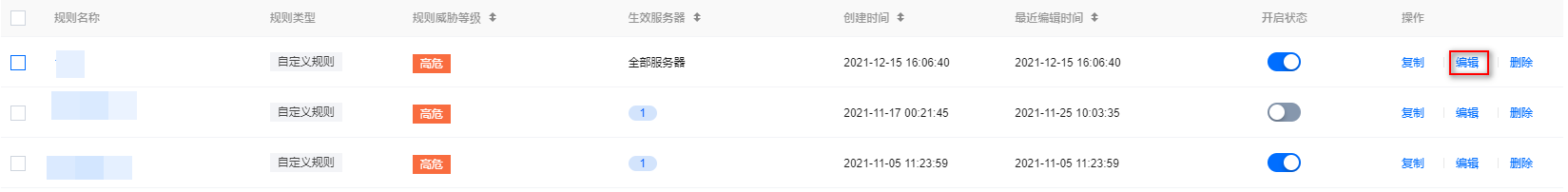
2. 在编辑规则页面,修改相关参数,单击保存即可。
复制规则
1. 在 核心文件监控 > 监控规则配置页面,选择所需规则,单击操作列的复制。
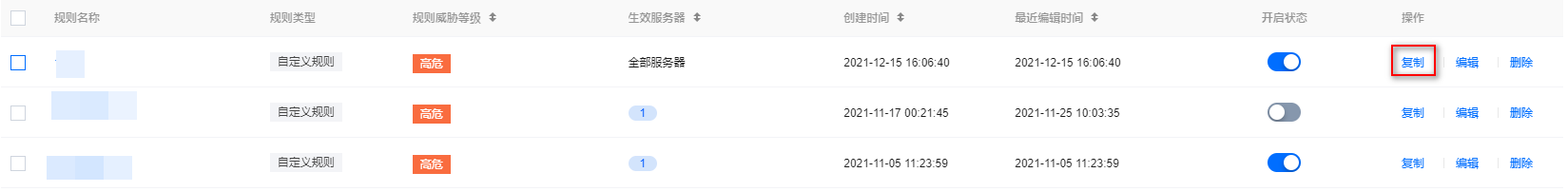
2. 在复制规则页面,修改相关参数,单击保存即可。
删除规则
1. 在 核心文件监控 > 监控规则配置页面,支持删除单个规则或批量删除规则,具体操作如下。
单个:选择单个规则, 单击操作列的删除,弹出“确认删除”弹窗。
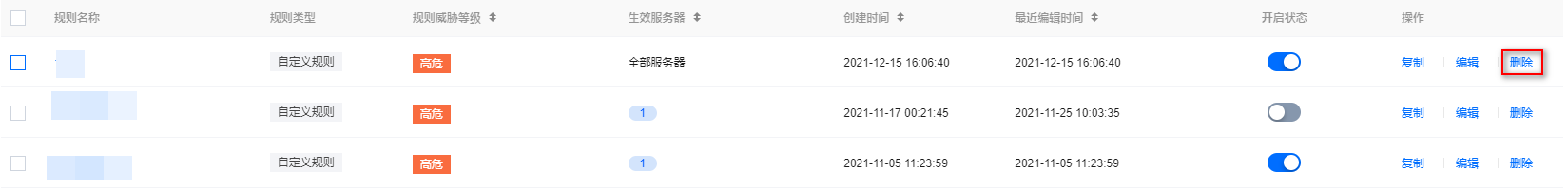
批量:选择所需规则,单击删除,弹出“确认删除”弹窗。
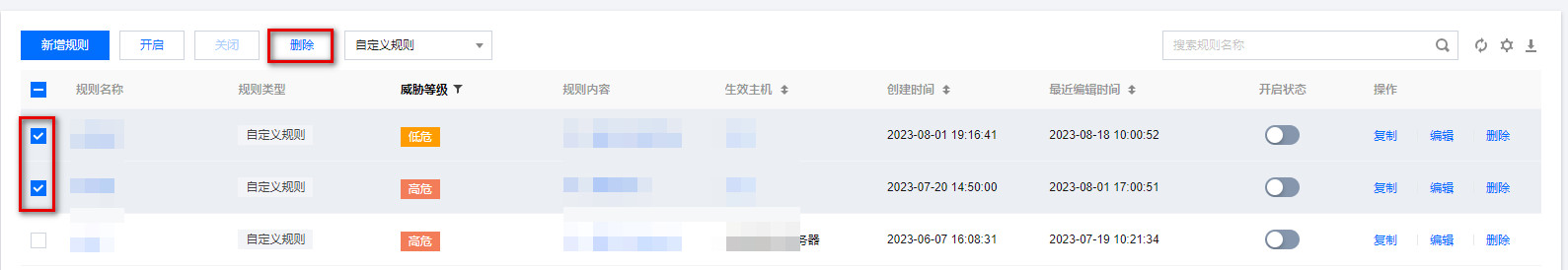
2. 在“确认删除”弹窗中,单击确认,即可完成删除规则。
注意:
删除后,规则将无法恢复,请谨慎操作。
文档反馈

