API 事件管理
最后更新时间:2024-09-05 11:28:40
功能简介
事件管理功能目前支持对发现的 API 风险事件进行查看、分析、处置,结合专家建议分级分类收敛风险,并持续运营防护策略,实现 API 风险事件的处置闭环。目前已支持如下6大类17种 API 风险事件检测:
事件类型 | 事件说明 |
缺失用户值 | 请求缺少必要的用户信息,例如用户 ID、用户名等,可能是攻击者在对业务进行攻击性尝试,如 Fuzzing(模糊测试)等。 |
缺失用户参数 | 请求缺少必要的参数,例如用户 ID、用户名等,可能是攻击者在对业务进行攻击性尝试,如 Fuzzing(模糊测试)等。 |
缺失用户和密码 | 请求缺少必要的用户和密码信息,可能是攻击者在对业务进行攻击性尝试,如 Fuzzing(模糊测试)等。 |
缺失登录动作 | 请求缺少必要的登录动作,例如登录请求中缺少登录动作参数,可能是攻击者在对业务进行攻击性尝试,如 Fuzzing(模糊测试)等。 |
垂直越权 | 用户或者攻击者通过修改参数、URL 等方式获取到本不属于其权限范围内的数据,可能导致敏感数据泄露和内部信息不安全。 |
未授权访问获取敏感信息 | 用户或者攻击者在未经授权的情况下访问到系统内的敏感数据,导致敏感数据泄露和内部信息不安全。 |
事件类型 | 事件说明 |
暴力破解 | 攻击者使用自动化工具对目标系统的密码进行暴力破解的行为。攻击者通常会使用字典攻击或暴力破解工具来尝试多个密码组合,直到找到正确的密码为止。 |
撞库攻击 | 攻击者使用已知的用户名和密码组合对目标系统进行登录尝试的行为,通常是通过泄露的用户信息进行攻击。攻击者通常会使用泄露的用户名和密码组合来尝试登录到其他网站或系统,以查看是否可以访问目标系统。 |
恶意注册 | 这意味着攻击者使用虚假或者盗用的用户信息进行注册的行为,通常是为了进行其他恶意行为,如垃圾邮件发送等。 |
事件类型 | 事件说明 |
刷短信接口 | 攻击者使用自动化工具对短信接口进行频繁的请求,通常是为了进行短信轰炸、消耗短信资源等恶意行为。 |
刷验证码接口 | 攻击者使用自动化工具对验证码接口进行频繁的请求,通常是为了进行验证码绕过,验证码资源消耗等恶意行为。 |
接口滥用 | 用户或者攻击者对接口进行频繁的请求,超出了正常的使用范围,可能会对系统造成负担或者安全风险。攻击者通常会使用自动化工具来发送大量的请求,以尝试消耗系统资源或者进行其他恶意行为。 |
事件类型 | 事件说明 |
来自异常地区的接口调用 | 日常访问该接口的请求集中在某地域,发现来自其他地域的请求大量调用了该接口,疑似异常调用。 |
来自异常源 IP 的接口调用 | 日常访问该接口的 IP 集中在某网段,发现大量异常 IP 段调用了该接口,疑似异常调用。 |
来自异常终端的接口调用 | 日常访问该接口的客户端主要是某类型,发现有大量请求通过其他类型客户端调用了该接口,疑似异常调用。 |
事件类型 | 事件说明 |
过多的敏感数据获取 | 用户或者攻击者通过调用该接口获取了大量的敏感数据,可能导致敏感数据泄露和内部信息不安全。 |
未授权访问获取敏感信息 | 用户或者攻击者在未经授权的情况下访问到系统内的敏感数据,导致敏感数据泄露和内部信息不安全。 |
事件类型 | 事件说明 |
Web 攻击 | 接口频繁遭受 SQL 注入攻击、XSS 攻击、命令注入攻击、核心文件非法访问、文件上传攻击、恶意扫描、木马后门攻击、XML 注入攻击、Web 应用漏洞攻击、LDAP 注入攻击、服务器端请求伪造、服务端模板注入漏洞、未授权访问漏洞、不合规协议等十余种类型 Web 攻击。 |
操作步骤
1. 登录 Web 应用防火墙控制台,在左侧导航栏中选择事件管理 > API 事件。
2. 在 AP I事件页面,单击左上角“全部域名”下拉框,选择要查看的域名,右侧展示当前域名是否开启 API 安全。
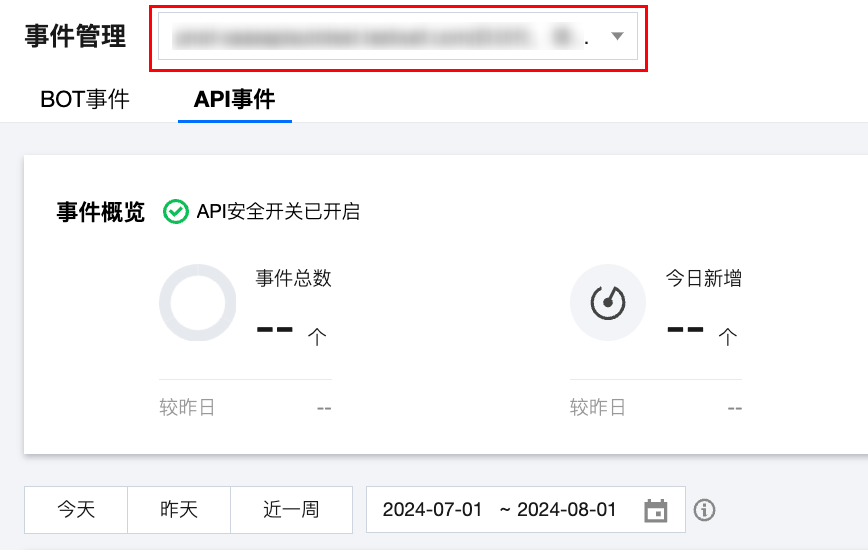
如 API 安全开关已开启,则可以开始使用相关功能。
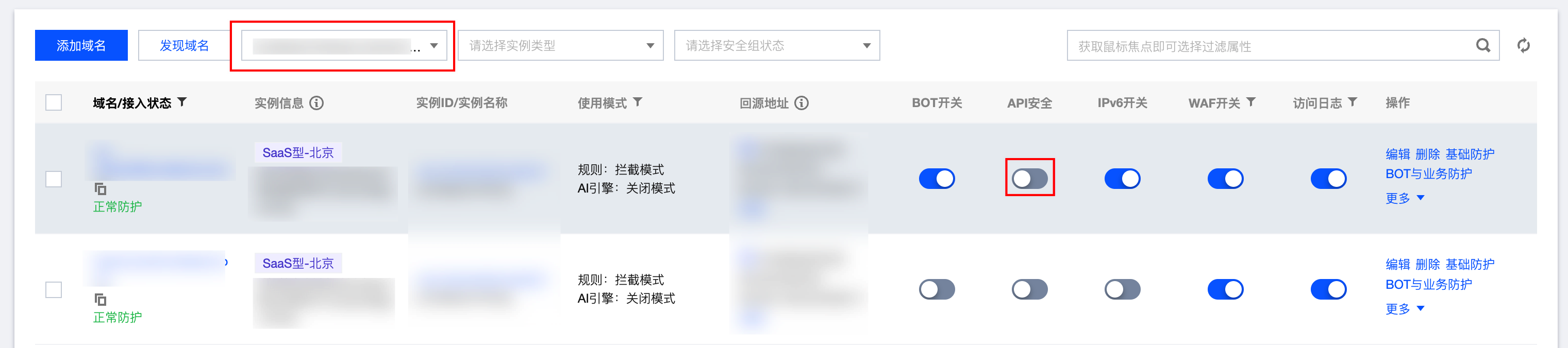
如 API 安全开关未开启,需前往 接入管理 页面,筛选已购买 API 安全的实例下需开启 API 安全开关的域名,单击

3. 在 API 事件管理页面,展示各类事件的统计概览,包括事件总数、今日新增事件数、状态为新发现、已处置、处置中的 API 事件数。

字段名称 | 说明 |
事件总数 | 当前域名下 API 事件总数。 |
今日新增 | 当前域名下今日新增 API 事件总数。 |
新发现 | 当前域名下新发现状态的 API 事件总数。 |
已处置 | 当前域名下已处置状态的 API 事件总数。 |
处置中 | 当前域名下已处置状态的 API 事件总数。 |
已忽略 | 当前域名下已忽略状态的 API 事件总数。 |
4. 在 API 事件管理页面,可以检索指定的时间范围内的 API 事件数据。
5. 在事件列表区域,主要包括 API 事件数据列表、API 事件进行状态变更、API 事件详情展示、API 事件搜索,以及 API 事件下载等功能。
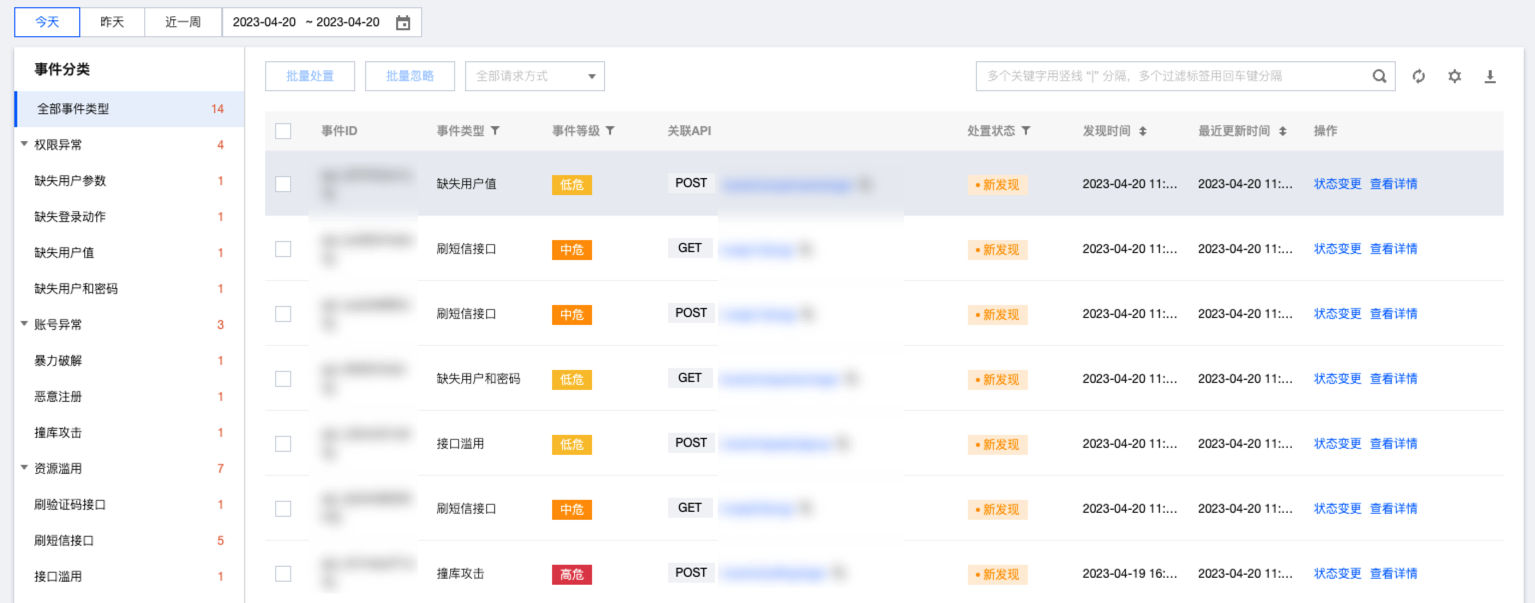
API事件数据列表:可查看当前域名在选中时间范围内的 API 事件列表。
字段名称 | 说明 |
事件 ID | API 事件名称。 |
事件类型 | API 事件类型。 |
事件等级 | API 事件风险等级。 |
关联 API | API 事件所关联的 API 名称。 |
处置状态 | API 事件当前的事件状态。 新发现:新发现且尚未确认的 API 事件。 处置中:正在确认风险并配置相关规则的 API 事件。该状态中有针对该事件类型的处理建议(CC/访问控制/BOT 等),可一键添加相应规则。 已确认:已确认风险并添加处置规则的 API 事件。 已忽略:确认不需处置,忽略该 API 事件。 已关闭:观察访问流量及攻击流量情况,确认该事件可以彻底关闭。 |
发现时间 | 该 API 事件最早发现时间。 |
最近更新时间 | 该 API 事件最近更新时间。 |
操作 | 状态变更和查看详情。 |
状态变更:单击状态变更,即可对当前 API 事件状态进行状态变更处理。
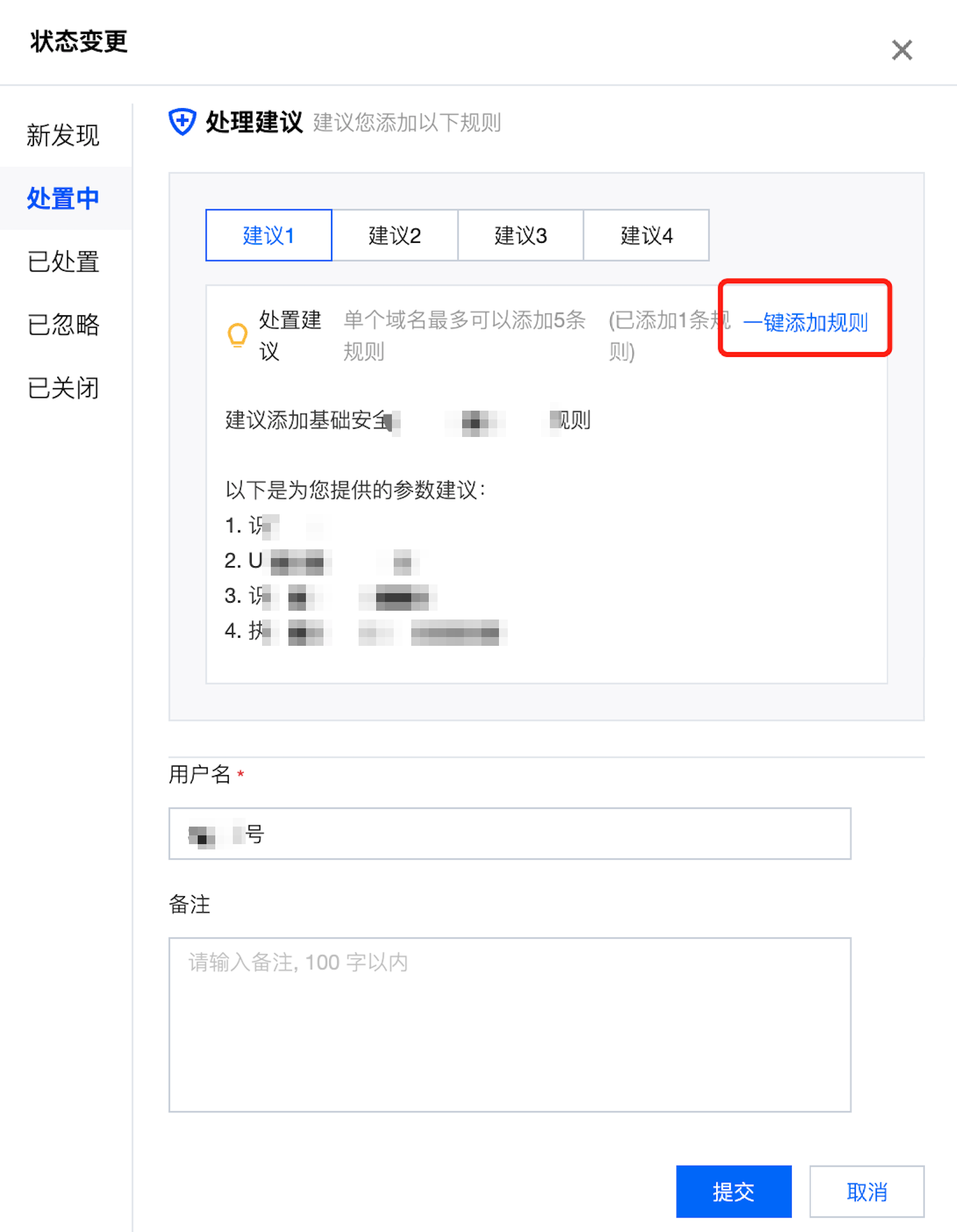
用户名:非空,默认填充当前控制台账户名称。
备注:可填写相应备注信息。
处置建议:根据不同的事件类型,提供对应的事件处置建议,可单击一键添加规则相应处置规则。
查看详情:单击查看详情,即可查看当前 API 事件的事件详情。
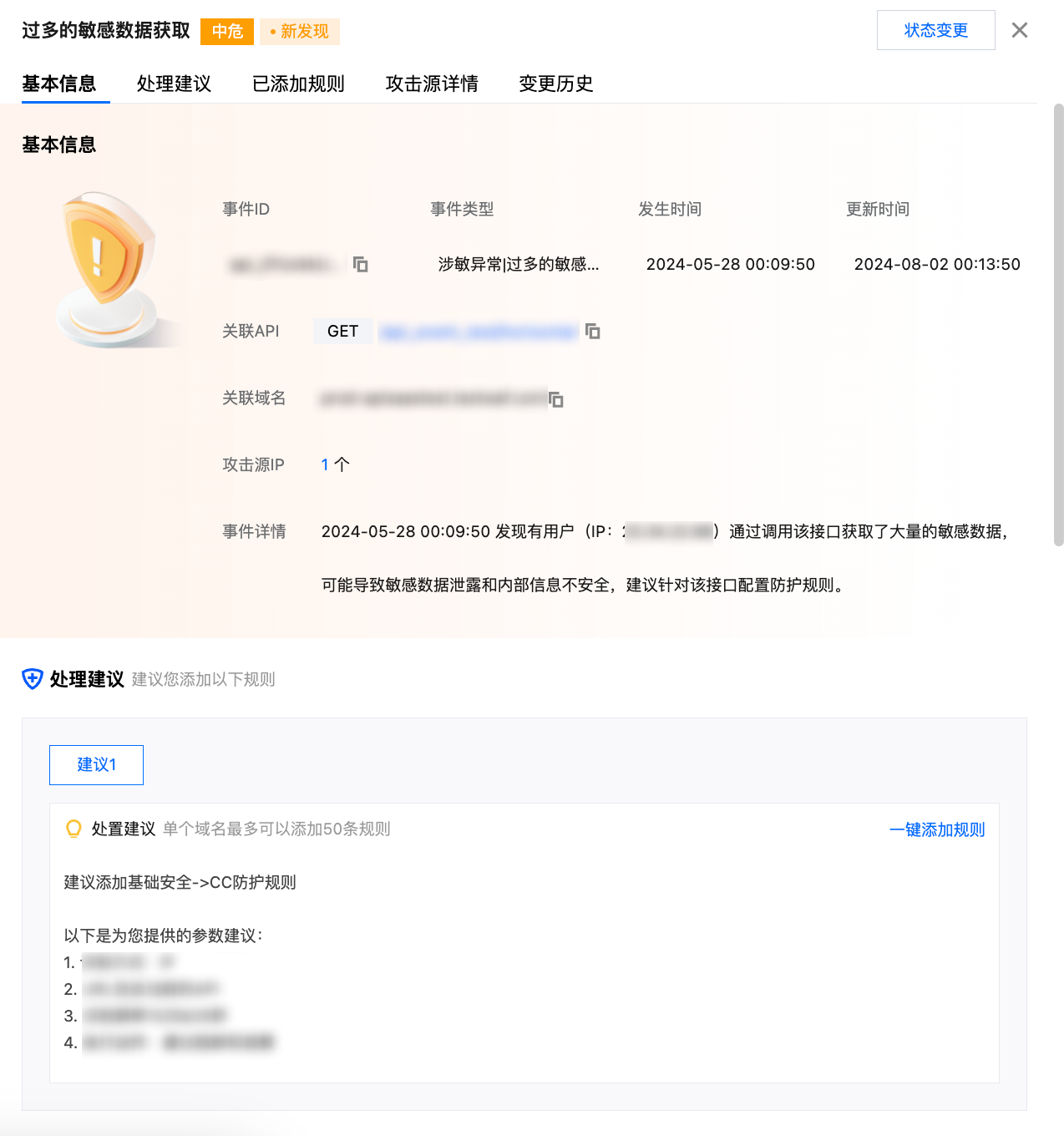
字段名称 | 说明 |
基本信息 | 主要包括事件 ID、事件类型、发生时间、更新时间、关联 API、关联域名以及事件详情等。 |
处理建议 | 根据不同的事件类型,提供对应的事件处置建议,可单击一键添加相应处置规则。 |
已添加规则 | 已添加规则情况。 |
攻击源详情 | 事件攻击源详情。 |
变更历史 | 事件状态变更历史情况。 |
API 事件搜索:可根据“API 名称和所属域名”进行搜索。
API 资产下载:单击
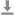

事件告警
告警开关:单击

设置:支持自定义告警类型和告警频率。
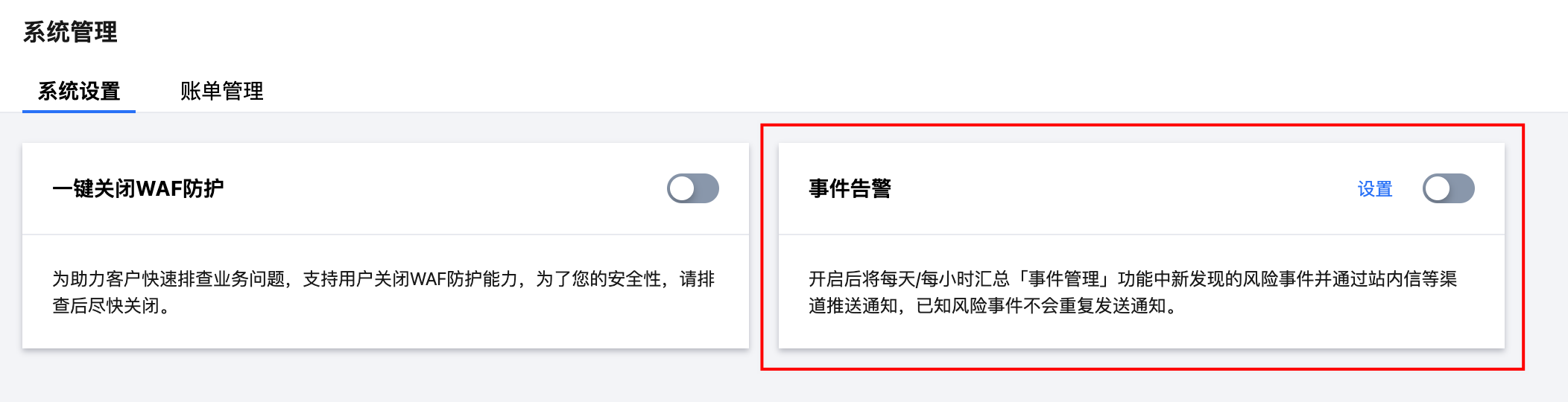
告警类型:支持选择 BOT 事件及 API 事件,勾选不同风险等级的事件进行告警,建议全部勾选。
告警时间:支持选择每天汇总告警或每小时汇总告警,默认为每天上午10点告警。
每天汇总:支持设置每日告警的通知时间,每天仅在指定时间汇总所有新增事件告警一次。
每小时汇总:支持设置需要通知的时间范围,在指定时间范围内每小时整点推送一次告警,非设置时间点或时间范围内不进行通知。
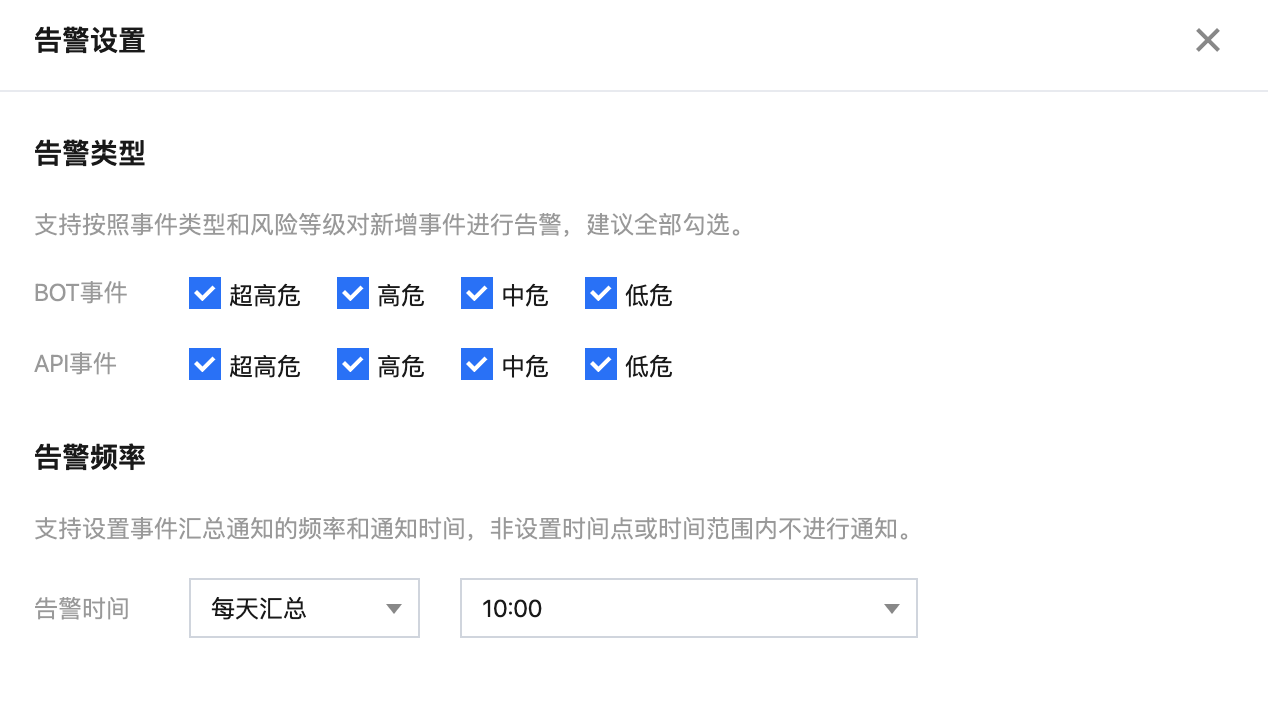
接收渠道及接受人设置:如需修改消息接收人或接收方式,请前往 消息中心 ,选择产品服务相关通知进行设置。
文档反馈

