- Release Notes and Announcements
- Tencent Cloud Network Overview
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Network Topology
- Network performance dashboard
- Virtual Private Cloud (VPC)
- Subnets
- Route Tables
- IPs and ENIs
- Bandwidth Package
- Network Connection
- Security Management
- Diagnostic Tools
- Alarming and Monitoring
- Practical Tutorial
- View the Total Bandwidth for Single-Region Traffic-Based Billing
- Migrating from the Classic Network to VPC
- Best Practices of Security Group Change
- Configuring CVM Instance as Public Gateway
- Building HA Primary/Secondary Cluster with HAVIP + Keepalived
- Creating a High-availability Database by Using HAVIP + Windows Server Failover Cluster
- Hybrid Cloud Primary/Secondary Communication (DC and VPN)
- Hybrid Cloud Primary/Secondary Communication (CCN and VPN)
- CVM Access to Internet Through EIP
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- VPC APIs
- CreateAssistantCidr
- DeleteAssistantCidr
- DeleteTrafficPackages
- DescribeClassicLinkInstances
- DescribeTrafficPackages
- ModifyAssistantCidr
- AssignIpv6CidrBlock
- CreateDefaultVpc
- CreateLocalGateway
- DeleteLocalGateway
- DescribeAccountAttributes
- DescribeAssistantCidr
- DescribeLocalGateway
- DescribeUsedIpAddress
- DescribeVpcInstances
- DescribeVpcIpv6Addresses
- DescribeVpcPrivateIpAddresses
- ModifyLocalGateway
- UnassignIpv6CidrBlock
- AttachClassicLinkVpc
- CheckAssistantCidr
- DeleteVpc
- DescribeVpcResourceDashboard
- DetachClassicLinkVpc
- CreateVpc
- DescribeVpcs
- AdjustPublicAddress
- ModifyVpcAttribute
- ModifyReserveIpAddress
- DescribeReserveIpAddresses
- DeleteReserveIpAddresses
- CreateReserveIpAddresses
- Route Table APIs
- EIP APIs
- Highly Available Virtual IP APIs
- ENI APIs
- AssignIpv6Addresses
- AssignPrivateIpAddresses
- AssociateNetworkInterfaceSecurityGroups
- CreateAndAttachNetworkInterface
- CreateNetworkInterface
- DescribeNetworkInterfaceLimit
- DisassociateNetworkInterfaceSecurityGroups
- ModifyIpv6AddressesAttribute
- ModifyNetworkInterfaceAttribute
- UnassignIpv6Addresses
- DeleteNetworkInterface
- DescribeNetworkInterfaces
- DetachNetworkInterface
- MigrateNetworkInterface
- MigratePrivateIpAddress
- ModifyPrivateIpAddressesAttribute
- UnassignPrivateIpAddresses
- AttachNetworkInterface
- Bandwidth Package APIs
- NAT Gateway APIs
- CreateNatGatewayDestinationIpPortTranslationNatRule
- CreateNatGatewaySourceIpTranslationNatRule
- DeleteNatGateway
- DeleteNatGatewayDestinationIpPortTranslationNatRule
- DeleteNatGatewaySourceIpTranslationNatRule
- DescribeNatGatewayDestinationIpPortTranslationNatRules
- DescribeNatGatewayDirectConnectGatewayRoute
- DescribeNatGatewaySourceIpTranslationNatRules
- DescribeNatGateways
- DisassociateNatGatewayAddress
- ModifyNatGatewayDestinationIpPortTranslationNatRule
- ModifyNatGatewaySourceIpTranslationNatRule
- RefreshDirectConnectGatewayRouteToNatGateway
- ResetNatGatewayConnection
- AssociateNatGatewayAddress
- CreateNatGateway
- ModifyNatGatewayAttribute
- Direct Connect Gateway APIs
- CreateDirectConnectGateway
- CreateDirectConnectGatewayCcnRoutes
- DeleteDirectConnectGateway
- DeleteDirectConnectGatewayCcnRoutes
- DescribeDirectConnectGatewayCcnRoutes
- DescribeDirectConnectGateways
- InquirePriceCreateDirectConnectGateway
- ModifyDirectConnectGatewayAttribute
- ReplaceDirectConnectGatewayCcnRoutes
- AssociateDirectConnectGatewayNatGateway
- DisassociateDirectConnectGatewayNatGateway
- Cloud Connect Network APIs
- AcceptAttachCcnInstances
- DescribeCrossBorderCompliance
- DetachCcnInstances
- EnableCcnRoutes
- ModifyCcnAttachedInstancesAttribute
- ModifyCcnAttribute
- RejectAttachCcnInstances
- ResetAttachCcnInstances
- CreateCcn
- DeleteCcn
- DisableCcnRoutes
- SetCcnRegionBandwidthLimits
- AttachCcnInstances
- DescribeCcnRegionBandwidthLimits
- AuditCrossBorderCompliance
- DescribeCcnAttachedInstances
- DescribeCcnRoutes
- DescribeCcns
- GetCcnRegionBandwidthLimits
- ModifyCcnRegionBandwidthLimitsType
- Network ACL APIs
- Network Detection-Related APIs
- Flow Log APIs
- Gateway Traffic Monitor APIs
- Private Link APIs
- CreateVpcEndPoint
- CreateVpcEndPointService
- CreateVpcEndPointServiceWhiteList
- DeleteVpcEndPoint
- DeleteVpcEndPointService
- DeleteVpcEndPointServiceWhiteList
- DescribeVpcEndPointServiceWhiteList
- DisassociateVpcEndPointSecurityGroups
- ModifyVpcEndPointAttribute
- ModifyVpcEndPointServiceWhiteList
- ModifyVpcEndPointServiceAttribute
- DescribeVpcEndPoint
- EnableVpcEndPointConnect
- DescribeVpcEndPointService
- Other APIs
- Subnet APIs
- VPN Gateway APIs
- RenewVpnGateway
- ModifyVpnGatewayRoutes
- CreateVpnGatewayRoutes
- DeleteVpnGatewayRoutes
- DescribeCustomerGateways
- DescribeVpnConnections
- DescribeVpnGatewayCcnRoutes
- DescribeVpnGatewayRoutes
- DownloadCustomerGatewayConfiguration
- ModifyVpnGatewayCcnRoutes
- SetVpnGatewaysRenewFlag
- CreateCustomerGateway
- CreateVpnConnection
- CreateVpnGateway
- DeleteCustomerGateway
- DeleteVpnConnection
- DeleteVpnGateway
- DescribeCustomerGatewayVendors
- DescribeVpnGateways
- GenerateVpnConnectionDefaultHealthCheckIp
- InquiryPriceRenewVpnGateway
- InquiryPriceResetVpnGatewayInternetMaxBandwidth
- ModifyCustomerGatewayAttribute
- ModifyVpnConnectionAttribute
- ModifyVpnGatewayAttribute
- ResetVpnConnection
- ResetVpnGatewayInternetMaxBandwidth
- InquiryPriceCreateVpnGateway
- Security Group APIs
- DescribeSecurityGroupReferences
- CloneSecurityGroup
- DeleteSecurityGroup
- DeleteSecurityGroupPolicies
- DescribeSecurityGroupAssociationStatistics
- DescribeSecurityGroupPolicies
- DescribeSecurityGroups
- ModifySecurityGroupAttribute
- ModifySecurityGroupPolicies
- ReplaceSecurityGroupPolicies
- ReplaceSecurityGroupPolicy
- CreateSecurityGroupPolicies
- CreateSecurityGroupWithPolicies
- CreateSecurityGroup
- Network Parameter Template-Related APIs
- CreateAddressTemplate
- CreateAddressTemplateGroup
- DeleteAddressTemplate
- DeleteAddressTemplateGroup
- DeleteServiceTemplate
- DeleteServiceTemplateGroup
- DescribeAddressTemplateGroups
- DescribeAddressTemplates
- DescribeServiceTemplateGroups
- DescribeServiceTemplates
- ModifyAddressTemplateAttribute
- ModifyAddressTemplateGroupAttribute
- ModifyServiceTemplateGroupAttribute
- CreateServiceTemplate
- CreateServiceTemplateGroup
- ModifyServiceTemplateAttribute
- Snapshot Policy APIs
- Error Codes
- Data Types
- FAQs
- Contact Us
- Glossary
- Release Notes and Announcements
- Tencent Cloud Network Overview
- Product Introduction
- Purchase Guide
- Quick Start
- Operation Guide
- Network Topology
- Network performance dashboard
- Virtual Private Cloud (VPC)
- Subnets
- Route Tables
- IPs and ENIs
- Bandwidth Package
- Network Connection
- Security Management
- Diagnostic Tools
- Alarming and Monitoring
- Practical Tutorial
- View the Total Bandwidth for Single-Region Traffic-Based Billing
- Migrating from the Classic Network to VPC
- Best Practices of Security Group Change
- Configuring CVM Instance as Public Gateway
- Building HA Primary/Secondary Cluster with HAVIP + Keepalived
- Creating a High-availability Database by Using HAVIP + Windows Server Failover Cluster
- Hybrid Cloud Primary/Secondary Communication (DC and VPN)
- Hybrid Cloud Primary/Secondary Communication (CCN and VPN)
- CVM Access to Internet Through EIP
- Troubleshooting
- API Documentation
- History
- Introduction
- API Category
- Making API Requests
- VPC APIs
- CreateAssistantCidr
- DeleteAssistantCidr
- DeleteTrafficPackages
- DescribeClassicLinkInstances
- DescribeTrafficPackages
- ModifyAssistantCidr
- AssignIpv6CidrBlock
- CreateDefaultVpc
- CreateLocalGateway
- DeleteLocalGateway
- DescribeAccountAttributes
- DescribeAssistantCidr
- DescribeLocalGateway
- DescribeUsedIpAddress
- DescribeVpcInstances
- DescribeVpcIpv6Addresses
- DescribeVpcPrivateIpAddresses
- ModifyLocalGateway
- UnassignIpv6CidrBlock
- AttachClassicLinkVpc
- CheckAssistantCidr
- DeleteVpc
- DescribeVpcResourceDashboard
- DetachClassicLinkVpc
- CreateVpc
- DescribeVpcs
- AdjustPublicAddress
- ModifyVpcAttribute
- ModifyReserveIpAddress
- DescribeReserveIpAddresses
- DeleteReserveIpAddresses
- CreateReserveIpAddresses
- Route Table APIs
- EIP APIs
- Highly Available Virtual IP APIs
- ENI APIs
- AssignIpv6Addresses
- AssignPrivateIpAddresses
- AssociateNetworkInterfaceSecurityGroups
- CreateAndAttachNetworkInterface
- CreateNetworkInterface
- DescribeNetworkInterfaceLimit
- DisassociateNetworkInterfaceSecurityGroups
- ModifyIpv6AddressesAttribute
- ModifyNetworkInterfaceAttribute
- UnassignIpv6Addresses
- DeleteNetworkInterface
- DescribeNetworkInterfaces
- DetachNetworkInterface
- MigrateNetworkInterface
- MigratePrivateIpAddress
- ModifyPrivateIpAddressesAttribute
- UnassignPrivateIpAddresses
- AttachNetworkInterface
- Bandwidth Package APIs
- NAT Gateway APIs
- CreateNatGatewayDestinationIpPortTranslationNatRule
- CreateNatGatewaySourceIpTranslationNatRule
- DeleteNatGateway
- DeleteNatGatewayDestinationIpPortTranslationNatRule
- DeleteNatGatewaySourceIpTranslationNatRule
- DescribeNatGatewayDestinationIpPortTranslationNatRules
- DescribeNatGatewayDirectConnectGatewayRoute
- DescribeNatGatewaySourceIpTranslationNatRules
- DescribeNatGateways
- DisassociateNatGatewayAddress
- ModifyNatGatewayDestinationIpPortTranslationNatRule
- ModifyNatGatewaySourceIpTranslationNatRule
- RefreshDirectConnectGatewayRouteToNatGateway
- ResetNatGatewayConnection
- AssociateNatGatewayAddress
- CreateNatGateway
- ModifyNatGatewayAttribute
- Direct Connect Gateway APIs
- CreateDirectConnectGateway
- CreateDirectConnectGatewayCcnRoutes
- DeleteDirectConnectGateway
- DeleteDirectConnectGatewayCcnRoutes
- DescribeDirectConnectGatewayCcnRoutes
- DescribeDirectConnectGateways
- InquirePriceCreateDirectConnectGateway
- ModifyDirectConnectGatewayAttribute
- ReplaceDirectConnectGatewayCcnRoutes
- AssociateDirectConnectGatewayNatGateway
- DisassociateDirectConnectGatewayNatGateway
- Cloud Connect Network APIs
- AcceptAttachCcnInstances
- DescribeCrossBorderCompliance
- DetachCcnInstances
- EnableCcnRoutes
- ModifyCcnAttachedInstancesAttribute
- ModifyCcnAttribute
- RejectAttachCcnInstances
- ResetAttachCcnInstances
- CreateCcn
- DeleteCcn
- DisableCcnRoutes
- SetCcnRegionBandwidthLimits
- AttachCcnInstances
- DescribeCcnRegionBandwidthLimits
- AuditCrossBorderCompliance
- DescribeCcnAttachedInstances
- DescribeCcnRoutes
- DescribeCcns
- GetCcnRegionBandwidthLimits
- ModifyCcnRegionBandwidthLimitsType
- Network ACL APIs
- Network Detection-Related APIs
- Flow Log APIs
- Gateway Traffic Monitor APIs
- Private Link APIs
- CreateVpcEndPoint
- CreateVpcEndPointService
- CreateVpcEndPointServiceWhiteList
- DeleteVpcEndPoint
- DeleteVpcEndPointService
- DeleteVpcEndPointServiceWhiteList
- DescribeVpcEndPointServiceWhiteList
- DisassociateVpcEndPointSecurityGroups
- ModifyVpcEndPointAttribute
- ModifyVpcEndPointServiceWhiteList
- ModifyVpcEndPointServiceAttribute
- DescribeVpcEndPoint
- EnableVpcEndPointConnect
- DescribeVpcEndPointService
- Other APIs
- Subnet APIs
- VPN Gateway APIs
- RenewVpnGateway
- ModifyVpnGatewayRoutes
- CreateVpnGatewayRoutes
- DeleteVpnGatewayRoutes
- DescribeCustomerGateways
- DescribeVpnConnections
- DescribeVpnGatewayCcnRoutes
- DescribeVpnGatewayRoutes
- DownloadCustomerGatewayConfiguration
- ModifyVpnGatewayCcnRoutes
- SetVpnGatewaysRenewFlag
- CreateCustomerGateway
- CreateVpnConnection
- CreateVpnGateway
- DeleteCustomerGateway
- DeleteVpnConnection
- DeleteVpnGateway
- DescribeCustomerGatewayVendors
- DescribeVpnGateways
- GenerateVpnConnectionDefaultHealthCheckIp
- InquiryPriceRenewVpnGateway
- InquiryPriceResetVpnGatewayInternetMaxBandwidth
- ModifyCustomerGatewayAttribute
- ModifyVpnConnectionAttribute
- ModifyVpnGatewayAttribute
- ResetVpnConnection
- ResetVpnGatewayInternetMaxBandwidth
- InquiryPriceCreateVpnGateway
- Security Group APIs
- DescribeSecurityGroupReferences
- CloneSecurityGroup
- DeleteSecurityGroup
- DeleteSecurityGroupPolicies
- DescribeSecurityGroupAssociationStatistics
- DescribeSecurityGroupPolicies
- DescribeSecurityGroups
- ModifySecurityGroupAttribute
- ModifySecurityGroupPolicies
- ReplaceSecurityGroupPolicies
- ReplaceSecurityGroupPolicy
- CreateSecurityGroupPolicies
- CreateSecurityGroupWithPolicies
- CreateSecurityGroup
- Network Parameter Template-Related APIs
- CreateAddressTemplate
- CreateAddressTemplateGroup
- DeleteAddressTemplate
- DeleteAddressTemplateGroup
- DeleteServiceTemplate
- DeleteServiceTemplateGroup
- DescribeAddressTemplateGroups
- DescribeAddressTemplates
- DescribeServiceTemplateGroups
- DescribeServiceTemplates
- ModifyAddressTemplateAttribute
- ModifyAddressTemplateGroupAttribute
- ModifyServiceTemplateGroupAttribute
- CreateServiceTemplate
- CreateServiceTemplateGroup
- ModifyServiceTemplateAttribute
- Snapshot Policy APIs
- Error Codes
- Data Types
- FAQs
- Contact Us
- Glossary
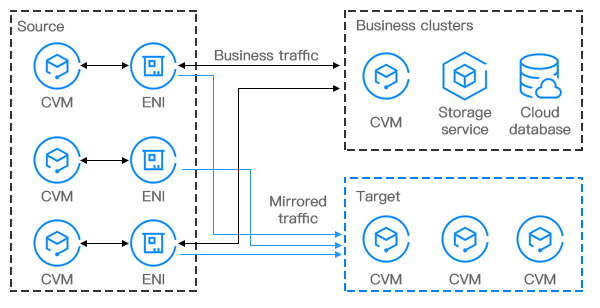
Traffic mirror provides a traffic collection service that filters and copies desired traffic from the specified network interface to CVM instances in the same VPC. This feature is applicable to use cases including security audit, risk monitoring, troubleshooting and business analysis.
Note:
However, traffic mirror consumes CVM resources such as CPU, memory and bandwidth pro rata. For example, if you mirror a network interface that has 1 Gbps of inbound traffic and 1 Gbps of outbound traffic. In this case, the instance needs to handle 1 Gbps of inbound traffic and 3 Gbps of outbound traffic (1 Gbps for the outbound traffic, 1 Gbps for the mirrored inbound traffic and 1 Gbps for the mirrored outbound traffic).
Procedure
The following are key components of a traffic mirror, together with its workflow.
Source: the specified ENI in the VPC that applies the filter rules such as network, collection range, collection type and traffic filtering.
Target: the receiving IPs that get the collected traffic.

Use Cases
Security auditing
A running system may occur unhealthy network traffic or generate an error message due to software exception, hardware fault, computer virus or improper use. To locate causes of these issues, you can use traffic mirror to analyze the network messages.
Intrusion checking
To ensure the confidentiality, integrity and availability of network system resources, you can use traffic mirror to copy traffic to CVM clusters for real-time analysis.
Business analysis
Use traffic mirror to clearly and visually present the business traffic mode.

 예
예
 아니오
아니오
문제 해결에 도움이 되었나요?