NAT Gateway
- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Public NAT Gateway Operation Guide
- Managing Port Forwarding Rules
- Monitoring and Alarms
- Private NAT Gateway Operation Guide
- Practical Tutorial
DocumentationNAT GatewayPractical TutorialEnabling Mutual Access between a Specified VPC Subnet and Public Network Resources via Private NAT Gateway
Enabling Mutual Access between a Specified VPC Subnet and Public Network Resources via Private NAT Gateway
Last updated: 2024-08-01 14:14:19
Enabling Mutual Access between a Specified VPC Subnet and Public Network Resources via Private NAT Gateway
Last updated: 2024-08-01 14:14:19
Overview
It applies to address translation of a specified subnet within a VPC, and is used for mutual access between the specified subnet in the VPC and the public network resources.
This document takes the following use case as an example. In the Guangzhou VPC, there are multiple subnets. Subnet 1 is not allowed to perform mutual access with the Shanghai VPC, while Subnet 2 is allowed. Therefore, in this case, Subnet 1 in the Guangzhou VPC implements mutual access with the Shanghai VPC by SNAT to other IPs.
Configuration Scheme
Refer to the diagram for the networking scheme configuration:
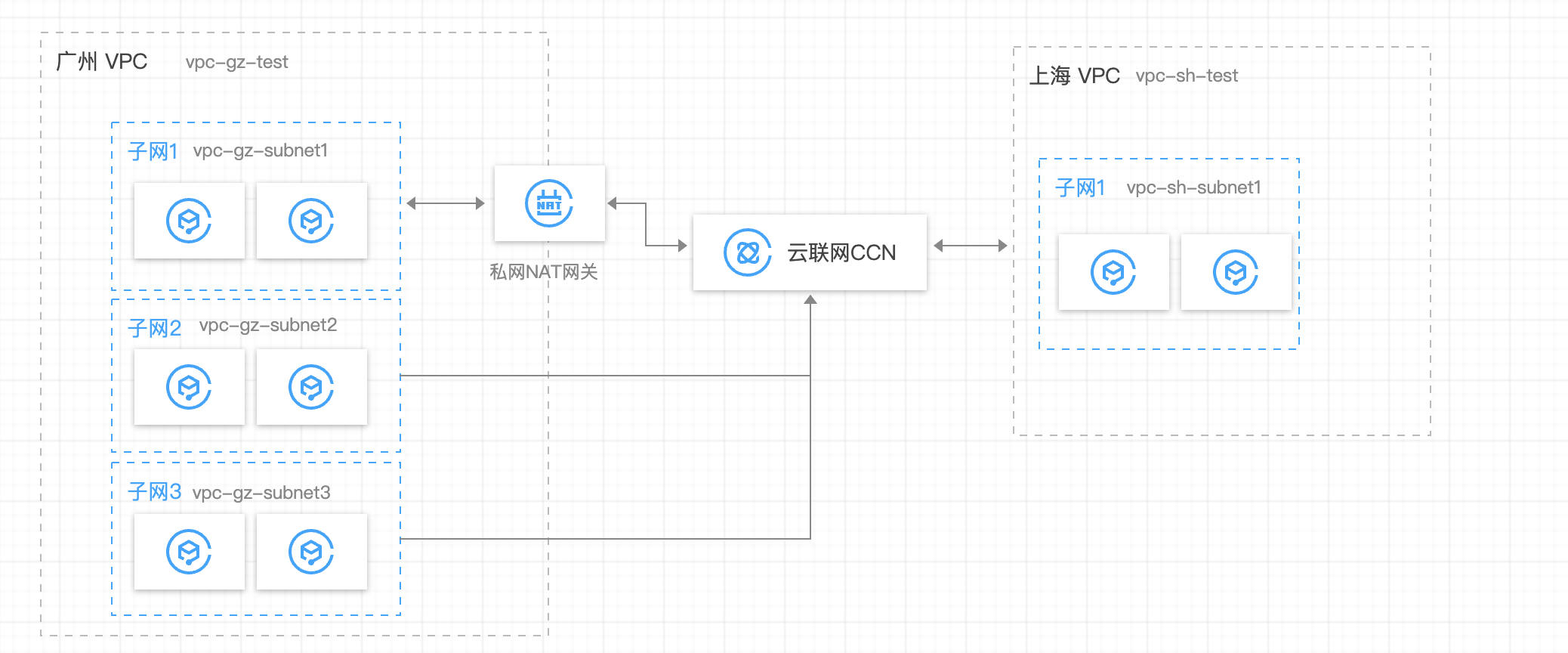
Step 1: Creating VPC Resources
Create a VPC in each of the Guangzhou region and the Shanghai region. For VPC creation, refer to Creating VPC. Create 3 subnets in the Guangzhou VPC and 1 subnet in the Shanghai VPC. Refer to Creating Subnets.
Guangzhou Region:
Create 1 VPC: vpc-gz-test.
Create 3 subnets:
Subnet 1: vpc-gz-subnet1, including 1 CVM: vpc-gz-cvm1;
Subnet 2: vpc-gz-subnet2, including 0 CVMs: none;
Subnet 3: vpc-gz-subnet3, including 1 CVM: vpc-gz-cvm2.
Shanghai Region:
Create 1 VPC: vpc-sh-test.
Create 1 subnet: vpc-sh-subnet1, including 1 CVM: vpc-sh-cvm1.
Step 2: Creating CCN Resources and Binding the 2 VPCs Created in Step 1
Log in to the CCN console and click New to create a CCN instance. For operation details, refer to Creating a CCN Instance.
Step 3: Disabling Self-learning Routes for NAT on the CCN Side
1. Log in to the CCN console and click the CCN instance created in Step 2 to enter the instance page.
2. Select the Route Table tab and disable the routes of the subnet IP range requiring NAT (corresponding to vpc-gz-subnet1 in the example).
Note:
If the IP range used as the NAT IP also belongs to a subnet IP range or its subset, you must disable the routes of the corresponding subnet. For example, if the IP range of vpc-gz-subnet2 is used as the NAT IP, you must disable the routes of vpc-gz-subnet2.
Step 4: Creating a VPC Private NAT Gateway in the Guangzhou VPC (vpc-gz-test)
Step 5: Editing the NAT Gateway Rules (Layer-4 SNAT Rules)
1. Log in to the Private NAT Gateway console and click the VPC private NAT gateway ID created in Step 4 to enter the gateway details page.
2. Click the SNAT tab, and edit the NAT gateway rules (Layer-4 SNAT rules).
Note:
The original IP is the IP of vpc-gz-cvm1, and the mapped IP pool (namely NAT IP) can be other third-party IPs, or a subset of other subnet IP ranges (e.g., obtained from the subnet IP range of vpc-gz-subnet2).
Step 6: Configuring the vpc-gz-test Side Routing
1. Log in to the VPC console. In the vpc-gz-test instance, create 2 route tables, vpc-gz-rtb1 and vpc-gz-rtb2, in which vpc-gz-rtb1 is bound to Subnet 1 (vpc-gz-subnet1).
2. In the route table vpc-gz-rtb1, disable all routes learned from CCN.
Note:
Whenever a new VPC joins the CCN, you must disable the corresponding learned routing entries in this route table.
3. Create a routing entry in vpc-gz-rtb1 with the destination being the IP range to be accessed and the next hop being the NAT instance created in Step 4.
4. Create a routing entry in vpc-gz-rtb2 with the destination being the NAT IP range (if allocated from other subnet IP ranges, it must be a subset of the subnet IP range and cannot be exactly the same as the subnet IP range), and publish it to the CCN.
Note:
The destination IP range must cover the NAT IP range of the mapped address pool in Step 4. (It's recommended to take the same values for both.) You can check the CCN route table to confirm whether the routing entry is published.
Step 7: Traffic Verification
Ping Shanghai vpc-sh-cvm1 from Guangzhou vpc-gz-cvm1, to check whether the network is normal and the source IP of the packets captured from vpc-sh-cvm1 is the NAT IP.
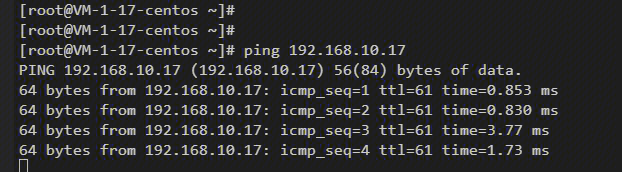
If the traffic ping fails, pay attention to the following cases:
1. In vpc-gz-rtb1, the routes published by CCN must be disabled.
2. vpc-gz-rtb2 should not be bound to any subnet.
3. If the NAT IP is allocated from a subnet, the NAT IP range must be a subset of the subnet IP range.
4. CCN must disable the routes of the subnet requiring NAT. (If the NAT IP is allocated from another subnet IP range, the routes of the corresponding IP range must also be disabled.)
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

