Virtual Private Cloud
- Release Notes and Announcements
- Product Introduction
- Purchase Guide
- Quick Start
- VPC Connections
- Operation Guide
- Virtual Private Cloud (VPC)
- Classiclink
- Subnets
- Route Tables
- IPs and ENIs
- Network Connection
- Security Management
- Security Groups
- Managing Security Groups
- Managing Security Group Rules
- Network ACL
- Parameter Template
- Diagnostic Tools
- Traffic Mirroring
- Practical Tutorial
- Migrating from the Classic Network to VPC
- Best Practices of Security Group Change
- Troubleshooting
- API Documentation
- Making API Requests
- VPC APIs
- Route Table APIs
- Elastic Public IP APIs
- Elastic IPv6 APIs
- Highly Available Virtual IP APIs
- ENI APIs
- Bandwidth Package APIs
- NAT Gateway APIs
- Direct Connect Gateway APIs
- Cloud Connect Network APIs
- Network ACL APIs
- Network Detection-Related APIs
- Flow Log APIs
- Gateway Traffic Monitor APIs
- Private Link APIs
- Other APIs
- Subnet APIs
- VPN Gateway APIs
- Security Group APIs
- Network Parameter Template-Related APIs
- Snapshot Policy APIs
- FAQs
Failed to Ping CVMs in the Same VPC
Last updated: 2024-10-22 16:53:57
Problem Description
The ping between two CVM instances in the same VPC fails.
Possible Causes
The access is blocked by the security group.
The access is blocked by the network ACL rules of the subnet.
There is a container route in a CVM instance.
Troubleshooting
Check the security group rules
1. Log in to the CVM console.
2. Click a CVM instance ID to enter the details page.
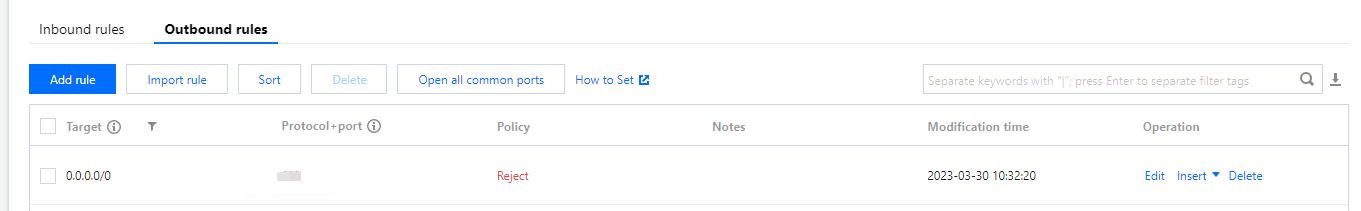
3. Click the Security Group tab to check whether the ICMP protocol and the inbound and outbound security group rules for the source/destination IPs are allowed.
If there is no corresponding protocol rule, or the rule is Reject, click Edit to modify the security group rule for the protocol, and then ping again to see whether the problem is solved.
If the inbound and outbound rules of the security group are correct, proceed to the next step.
Reject:
Allow:
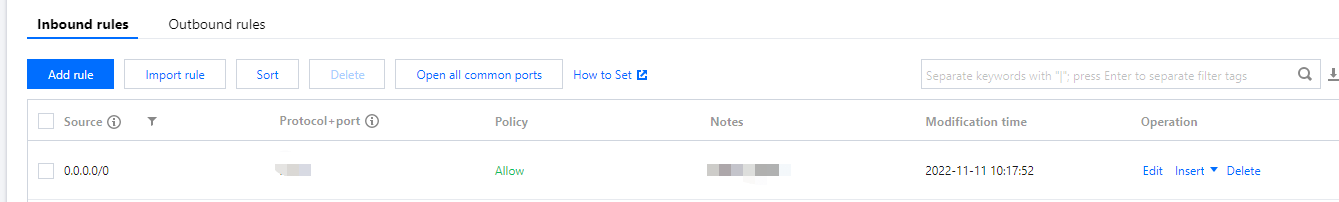
Check the network ACL rules associated with subnets
1. Log in to the CVM console.
2. Click a CVM instance ID to enter the details page.
3. Go to Instance details -> Basic information, click the subnet ID in Network information,
4. Click the ACL Rule tab to check the ACL-related settings.
An ACL is bound but there is no ICMP rule or ICMP set to rejected: Click the ACL ID to enter the ACL page, allow the corresponding protocol and source/destination IPs, and move the rule to the first place so that it will be matched first. Then, ping again to see whether the problem is solved, and if not, proceed to the next step.
No ACL is bound, or the protocol and IPs are allowed in the ACL: Proceed to the next step.
Checking for container route in CVM instance
1. Go to the CVM console, click Log in on the right of a CVM instance, enter the password or key as prompted to log in to the instance in the standard method, and run
route to view the internal route table of the system.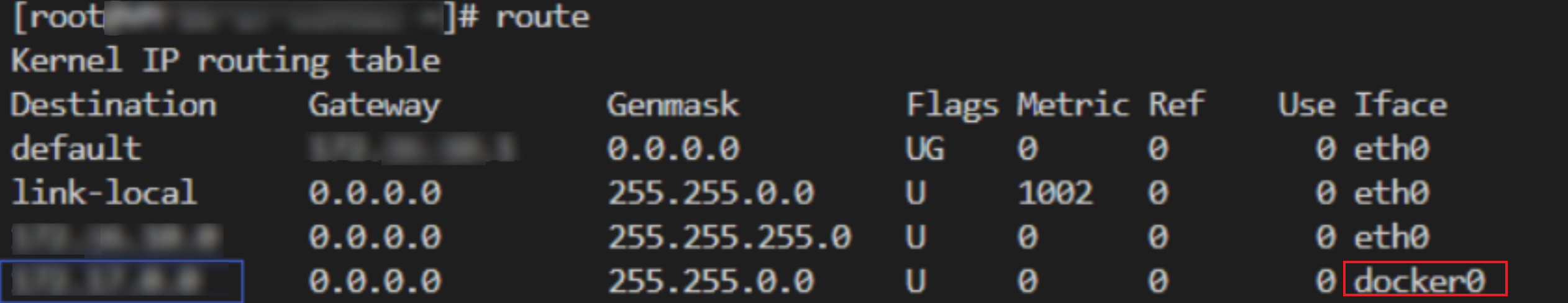
2. Check whether there is a Docker container route in the system with the same IP range as the subnet of the accessed CVM instance.
If yes, this problem is caused by the conflict with the container route. You need to delete the corresponding subnet.
If no, contact us for assistance.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

