透明数据加密
最后更新时间:2025-11-20 15:37:41
本文为您介绍云数据库 SQL Server 透明数据加密功能。
功能概述
透明数据加密(Transparent Data Encryption,以下简称 TDE)功能,指数据的加解密操作对用户透明,TDE 提供文件级别的加密,支持对数据文件进行实时 I/O 加密和解密,可以做到对数据库上层的应用透明,用户不需要修改业务代码,在数据写入磁盘前进行加密,存储在磁盘上的数据是加密的,从磁盘读取内存时进行解密,即对磁盘数据读取和写入时透明地进行加解密,TDE 不会增加数据文件的大小,可满足静态数据加密的合规性要求。
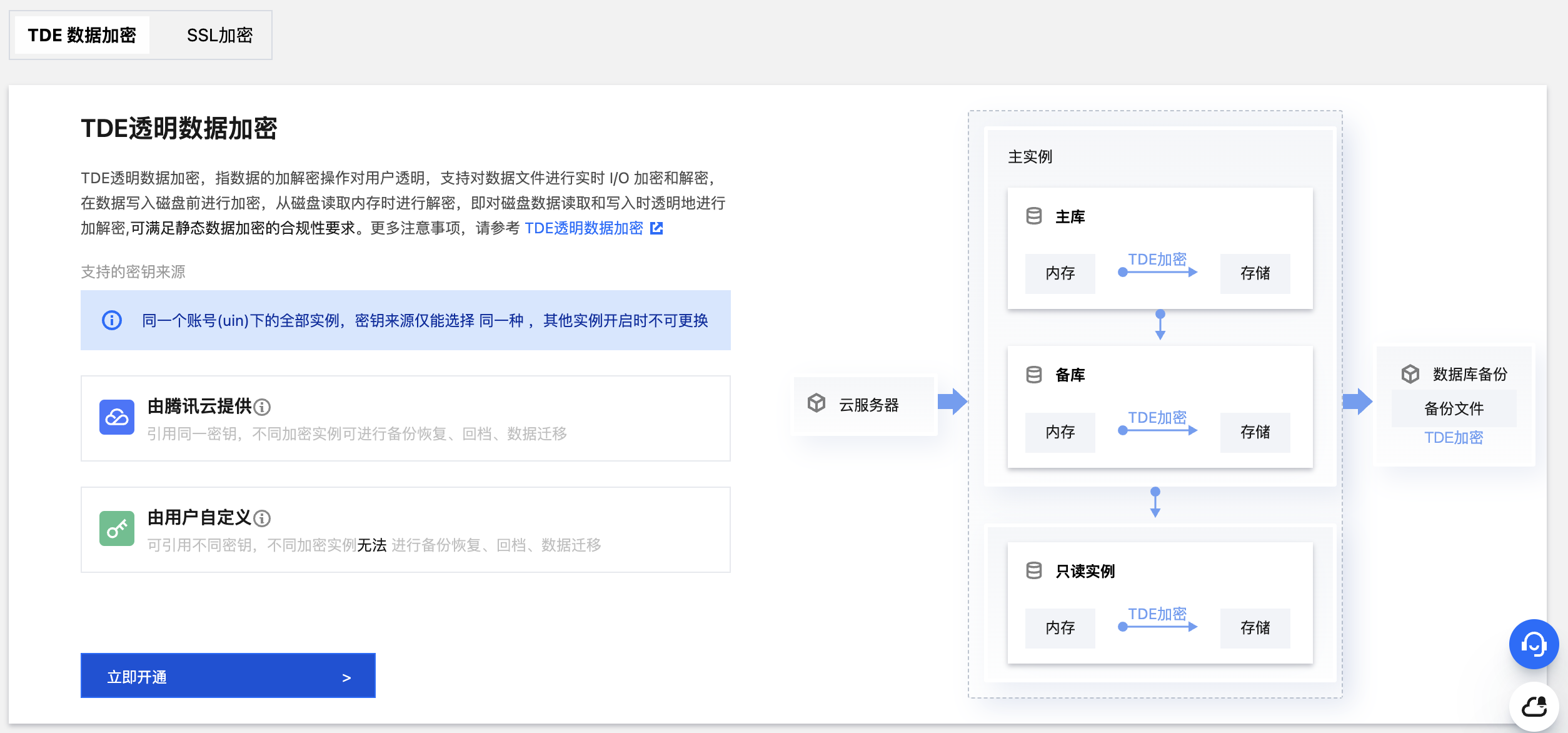
应用场景
TDE 常用于解决一些安全合规问题,如符合 PCI DSS、等级安全保护等标准对静态数据保护的要求。
注意事项
开启透明数据加密时,需要选择密钥来源,当前支持选择密钥来源为“由腾讯云提供”,以及“由用户自定义”。如果选择为“由用户自定义”,需要已开通 密钥管理服务 KMS,如未开通,可在开启透明数据加密的过程中根据指引开通;还需要已授予 KMS 密钥权限,如未授权,可在开启透明数据加密的过程中根据指引进行授权。
计费说明
云数据库 SQL Server 的透明数据加密功能不会额外收费,但加密使用的密钥来源如果是“由用户自定义”,由于该由 密钥管理服务 KMS 产生和管理,因此密钥管理服务 KMS 有可能产生额外费用,请参考 计费概述。
功能限制
密钥不支持下载。
实例级别的 TDE 只能开通,无法关闭。即开通 TDE 后,实例上的密钥无法删除。数据库级别的 TDE 可以开通或关闭。
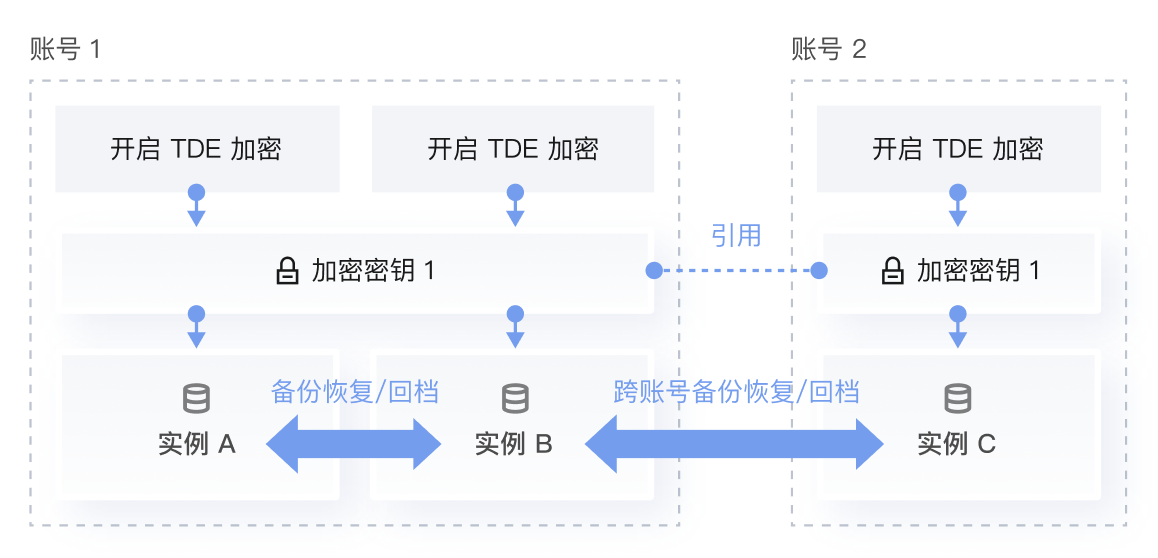
同一个账号(UIN)下仅所有实例的加密密钥相同时,才可以进行实例间的备份恢复及回档。
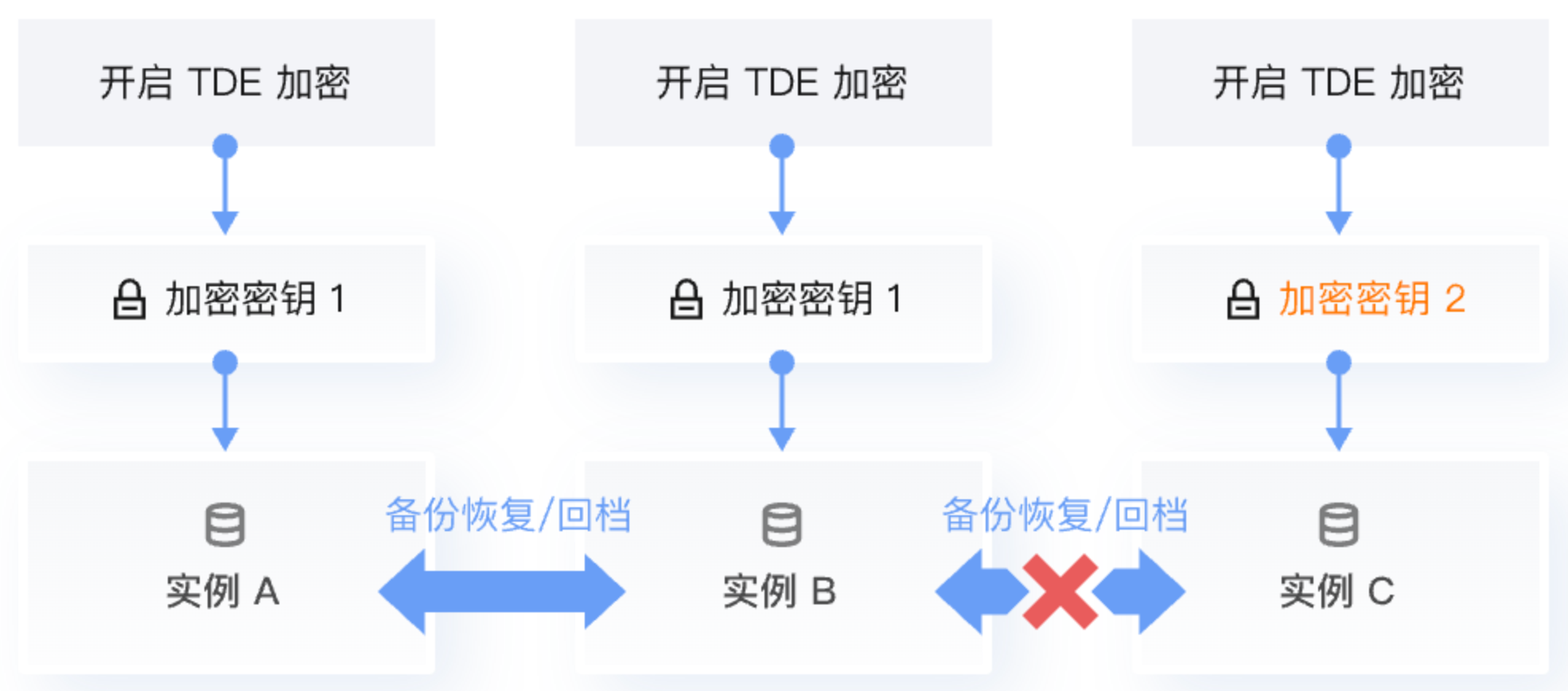
同一个账号(UIN)下的全部实例,密钥来源仅能选择同一种。即:仅能全部选择“由腾讯云提供”,或者全部选择“由用户自定义”。具体两种密钥来源的说明和对比,请参考 密钥来源说明。
不同账号(UIN)下的实例,如需进行备份恢复及回档,需要密钥来源选择使用腾讯云提供的密钥,并引用相同的密钥。
商业智能服务实例不支持开通 TDE 功能。
密钥来源说明
对比参数 | 密钥来源 | |
| 由腾讯云提供 | 由用户自定义 |
定义 | 开启透明数据加密后,密钥由腾讯云生成。 | |
同账号(UIN)引用密钥 | 同一个账号(UIN)下,不同加密实例的引用密钥必须一致。 | 同一个账号(UIN)下,不同加密实例的引用密钥可以相同,也可以不同。 |
跨账号(UIN)引用密钥 | 跨账号(UIN)下,不同加密实例的引用密钥可以相同,也可以不同。 | 跨账号(UIN)下,不同加密实例的引用密钥一定不同。 |
功能限制 | 若不同加密实例之间需要进行备份恢复、回档、数据迁移操作,建议选择密钥来源为使用腾讯云提供的密钥。 | 同一账号(UIN)下不同实例之间引用不同的密钥,加密实例无法进行备份恢复、回档、数据迁移操作;同一账号(UIN)下不同实例之间引用相同的密钥,可以进行备份恢复、回档、数据迁移操作;不同账号(UIN)下不同实例之间由于无法引用相同密钥,一定无法进行备份恢复、回档、数据迁移操作。 |
密钥场景架构图
功能说明
引用相同加密证书的实例,在备份恢复和数据迁移中,如果源数据库使用了 TDE 加密,而目标实例未开通实例级 TDE 功能,在同一账号(UIN)的情况下,目标实例会自动开通实例级 TDE 功能,此操作不影响业务。
若云数据库 SQL Server 实例分布在腾讯云不同账号(UIN)下,且后续需要进行跨账号备份恢复,开通 TDE 时,密钥来源请选择由腾讯云提供 > 引用其他账号的密钥,即需要保证不同账号下的实例开启 TDE 的密钥一致。即一个主账号(UIN)仅能有一个密钥,一个密钥可能会被多个主账号(UIN)所使用。
如果实例关联只读实例,只需主动开通主实例的 TDE 功能即可,其只读实例的透明数据加密会一并开通。
对于双节点架构的实例而言,要对实例开启/关闭数据库维度的 TDE 功能,则此实例不能关联有只读实例或发布订阅,需先解除只读实例或发布订阅后,再开启/关闭数据库维度的 TDE 功能,然后再重新添加只读实例和发布订阅;对于多节点架构的实例而言,无论是否开启备节点只读,对实例开启/关闭数据库维度的 TDE 功能,均无需先删除只读节点。
开通 TDE 功能后,不支持使用备份文件在线下恢复数据,若想恢复数据到本地,需要先关闭 TDE 功能,然后创建手动备份后,再通过备份文件恢复数据。
线下加密的数据库无法直接迁移上云数据库 SQL Server 实例,需要先关闭线下数据库级别的 TDE 功能,再进行迁移。
开通 TDE 功能后,可提高数据安全性,但同时会影响访问加密数据库的读写性能,也会明显增加实例 CPU 使用率,请谨慎选择开启 TDE 功能。此外,CPU 小于4核的实例不建议开启 TDE 功能。
开启/关闭数据库维度的 TDE 功能的持续时间可能会比较久,过程中请不要对实例进行以下任务操作,否则数据库 TDE 可能会开启/关闭失败,建议在业务低峰期进行。包括但不限于以下操作:
修改、删除数据库,使数据库脱机、分离数据库。
将数据库或文件组转换为 READ ONLY 状态。
数据库备份。
数据库回档/还原。
变更数据捕获 CDC。
更改跟踪 CT。
收缩数据库。
数据库克隆。
修改数据库权限。
注意:
若用户有多个主账号(UIN),且全部需要开启 TDE 功能,且不同主账号(UIN)之间后续需要进行跨账号备份恢复/迁移/回档等操作,请务必保证所有主账号引用相同的密钥。即在账号1中的实例开启 TDE 功能后,账号2、账号3、账号4……中的实例在开启 TDE 功能时,密钥来源需务必选择为“由腾讯云提供”,并且引用账号1的加密密钥,否则后续将无法进行跨账号操作(包括但不限于:跨账号回档、跨账号备份恢复、跨账号迁移等)。
开启实例级透明数据加密
场景一、当前账号下没有实例开启透明数据加密
1. 登录 SQL Server 控制台。
2. 选择地域,在实例列表单击需要开启 TDE 的实例 ID 或操作列的管理。
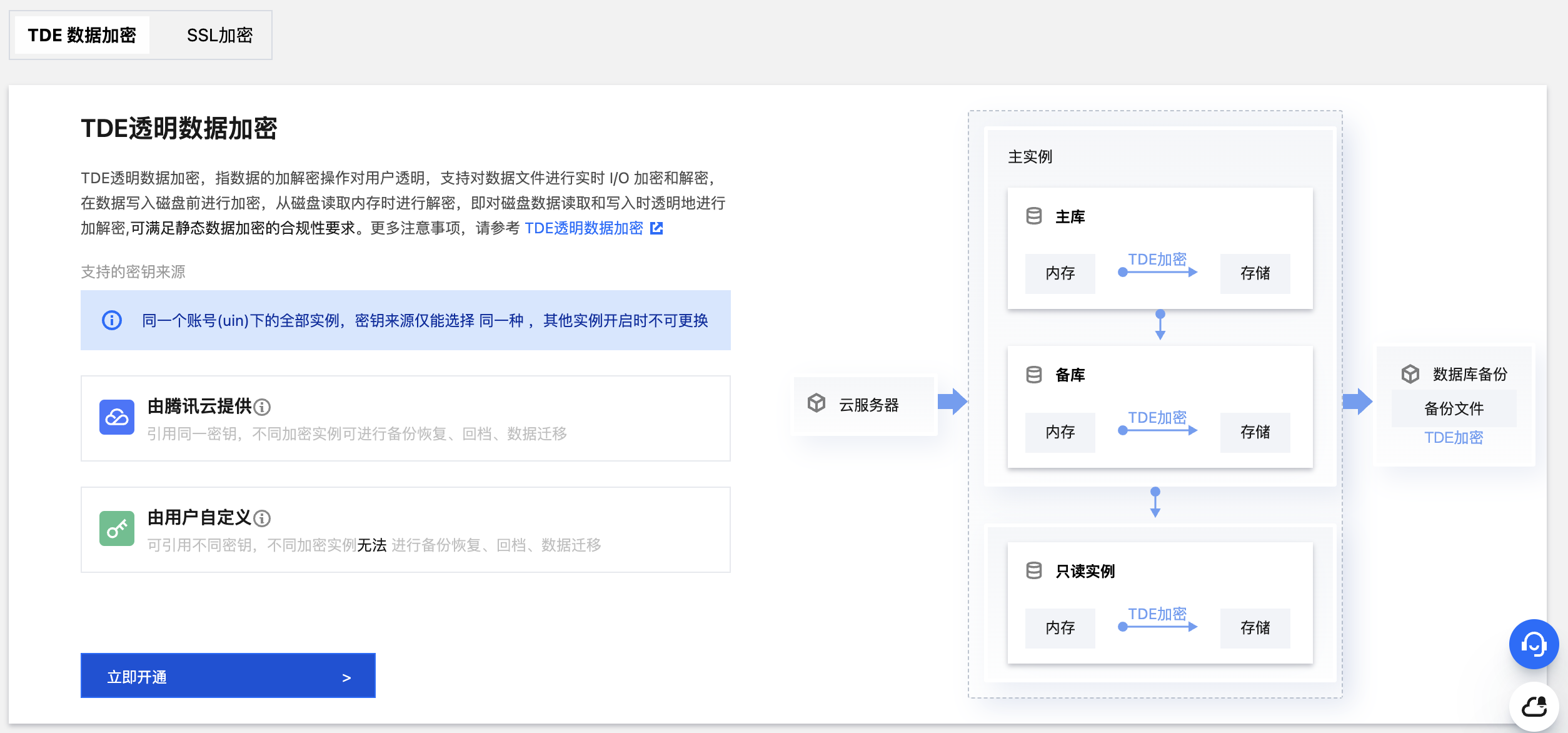
3. 在实例管理页选择数据安全 > TDE 数据加密。
4. 选择密钥来源,然后单击立即开通。
说明:
同一账号(UIN)下的全部实例,密钥来源仅能选择为同一种,即:仅能全部选择“由腾讯云提供”,或者全部选择“由用户自定义”,其他实例开启时不可更换。
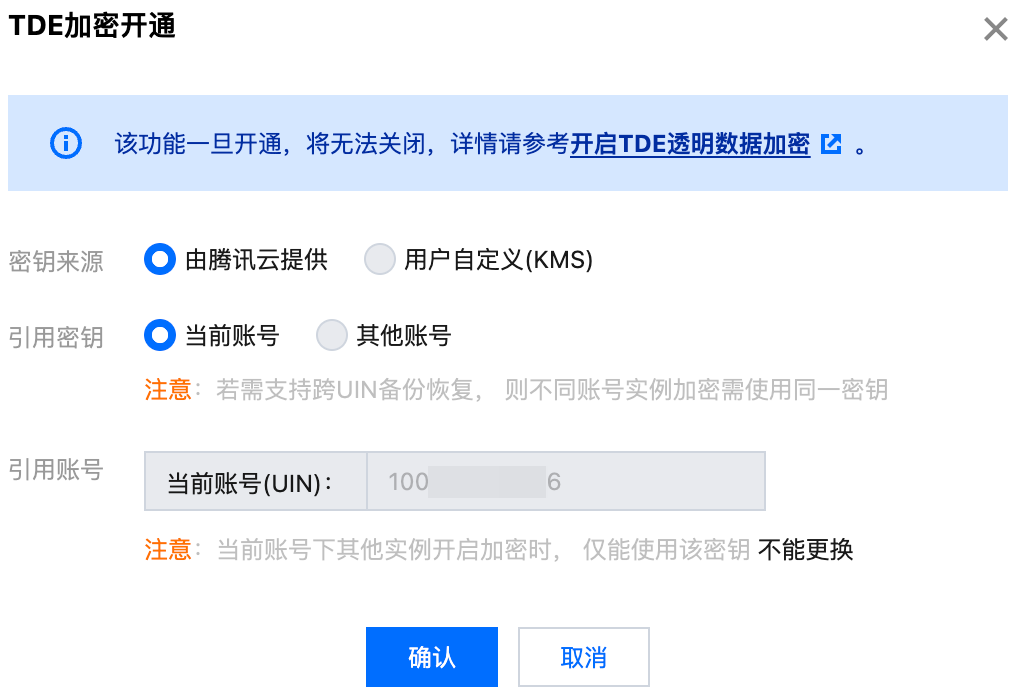
1. 选择密钥来源,支持选择为当前账号或其他账号。
2. 若选择为当前账号,密钥会默认设置为当前账号下的密钥,然后单击确定。
注意:
若需支持跨账号备份恢复,则不同账号实例加密需使用同一密钥。
当前账号下其他实例开启加密时,仅能使用该密钥且不能更换。
3. 若密钥来源选择为其他账号,请在引用密钥后选择其他账号下的目标密钥,然后单击确定。
注意:
若需支持跨账号备份恢复,则不同账号实例加密需使用同一密钥。
当前账号下其他实例开启加密时,仅能使用该密钥且不能更换。
1. 单击前往开通,开通 KMS 服务,若已开通则此步骤跳过。
2. 单击前往授权,进行 KMS 密钥授权,若已授权则此步骤跳过。
3. 选择密钥所在地域,选择密钥,单击确定。如需使用其他自定义密钥,请 前往创建。
注意:
若需支持同账号(UIN)备份恢复、回档、迁移,则不同实例的密钥需要保持一致。
5. 成功开启透明数据加密后,TDE 加密状态后会显示已开通(开通后不可关闭)。

场景二、当前账号下已有实例开启透明数据加密,且密钥来源为腾讯云
1. 登录 SQL Server 控制台。
2. 选择地域,在实例列表单击需要开启 TDE 的实例 ID 或操作列的管理。
3. 在实例管理页选择数据安全 > TDE 数据加密。
4. 由于当前账号下已有实例在开启加密时选择了密钥来源为“由腾讯云提供”,所以此时的密钥来源将默认为“由腾讯云提供”,您可直接单击立即开通。
5. 在弹窗下确认密钥后单击确定。
说明:
在此步骤无需选择引用密钥为当前账号(UIN)或其他账号(UIN),因为当前账号(UIN)下已有实例开启过透明数据加密,所以此时引用的密钥将默认和已开启实例保持一致。
6. 成功开启透明数据加密后,TDE 加密状态后会显示已开通(开通后不可关闭)。
场景三、当前账号下已有实例开启透明数据加密,且密钥来源为用户自定义
1. 登录 SQL Server 控制台。
2. 选择地域,在实例列表单击需要开启 TDE 的实例 ID 或操作列的管理。
3. 在实例管理页选择数据安全 > TDE 数据加密。
4. 由于当前账号下已有实例在开启加密时选择了密钥来源为“由用户自定义”,所以此时的密钥来源将默认为“由用户自定义”,您可直接单击立即开通。
5. 在弹窗下,若已开通 KMS 服务,已进行 KMS 密钥授权,您可选择密钥所在地域,选择密钥,单击确定。若之前取消了 KMS 相关的开通和授权,可根据弹窗下的提示重新开通和授权,然后再选择密钥所在地域,选择密钥,单击确定。
6. 成功开启透明数据加密后,TDE 加密状态后会显示已开通(开通后不可关闭)。
开启或关闭加密数据库
说明:
要对实例开启/关闭数据库维度的 TDE 功能,则此实例不能关联有只读实例或发布订阅,需先解除只读实例或发布订阅后,再开启/关闭数据库维度的 TDE 功能,然后再重新添加只读实例和发布订阅。
设置加密数据库前提是已开启实例级透明数据加密功能,步骤可参见 开启实例级透明数据加密。
1. 登录 SQL Server 控制台。
2. 选择地域,在实例列表单击目标实例的实例 ID 或操作列的管理。
3. 在实例管理页选择数据安全 > TDE 数据加密,然后在加密数据库后单击设置。
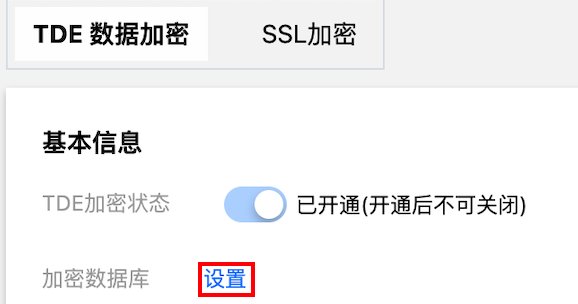
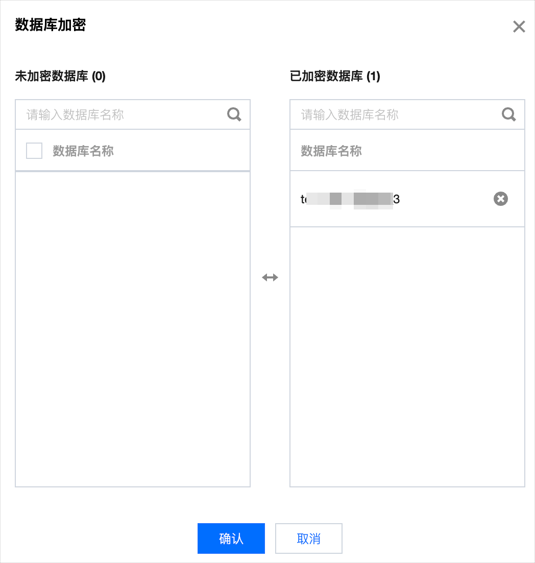
4. 在弹窗下,在左侧未加密数据库里勾选需要的数据库,表示对该数据库开启加密,在右侧已加密数据库里删除数据库,表示对该数据库关闭加密,根据需要操作后单击确认。
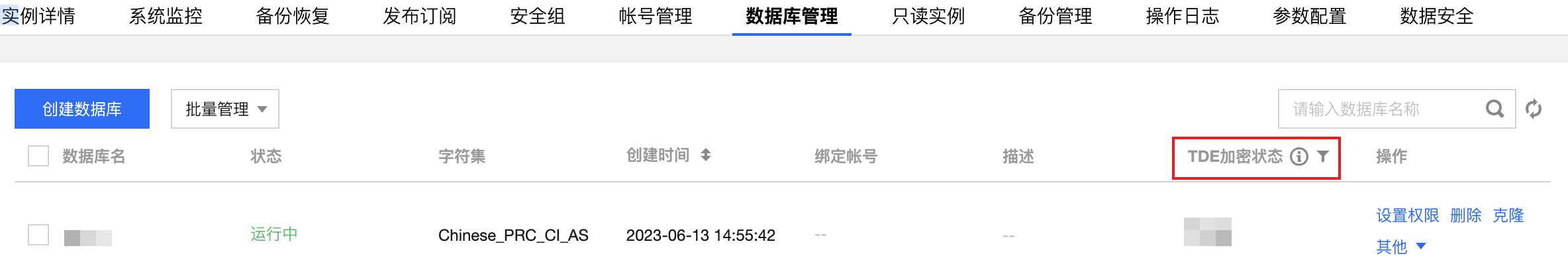
5. 开启数据库维度的 TDE 功能指定数据库后,在数据库管理下可根据字段 TDE 加密状态查看开启或关闭加密功能的数据库。
查看任务
在您开启实例级透明数据加密功能、开启或关闭加密数据库时,可通过控制台右上角的任务图标了解当前任务进度。

开启 TDE 功能的云上数据库在回档、备份恢复、迁移、克隆数据库时的限制说明
功能项 | 具体功能 | 说明 |
回档 | 回档至源实例 | 同实例密钥一致,可进行回档。 |
| 回档至同账号(UIN)下其他已有实例 | 同账号(UIN)下不同实例,要么密钥来源均为“由腾讯云提供”,要么密钥来源均为“由用户自定义”。回档时,若源实例和目标实例密钥一致,或者源数据库关闭加密,或者目标实例开启加密且密钥一致,才可以进行回档。 |
| 跨地域回档 | 开启跨地域备份的实例,跨地域备份文件会同步加密,使用加密的跨地域备份在异地进行回档时,需要同账号下不同地域实例的密钥也初始化一致,才能支持跨地域回档。跨地域回档时,若源实例和目标实例密钥一致,或者源数据库关闭加密,或者目标实例开启加密且密钥一致,才可以进行回档。 |
克隆数据库 | 克隆至源实例 | 同实例密钥一致,可进行克隆。 |
备份恢复(冷迁移) | 备份恢复至源实例 | 同实例密钥一致,可进行备份恢复。 |
| 备份恢复至同账号(UIN)下其他已有实例 | 已加密文件在做备份恢复时,需要具备源备份文件已关闭加密或目标实例开启加密的条件,才可以进行备份恢复。因此如果源数据库开启了 TDE 加密,而目标实例未开启实例级 TDE 加密,若密钥来源采用“由腾讯云提供”,由于同一账号下的加密密钥相同,则系统会自动给目标实例开通实例级 TDE 功能;若密钥来源采“由用户自定义”,则需用户自行开启目标实例的 TDE 加密且需要保证与源实例的密钥相同。 |
| 备份恢复至跨账号(UIN)实例 | 已加密文件在做备份恢复时,需要具备源备份文件已关闭加密或目标实例开启加密的条件,才可以进行备份恢复。因此当源数据库开启了 TDE 加密,而目标实例未开启实例级 TDE 加密时,若源数据库和目标实例所在账号(UIN)引用密钥相同,则系统会自动给目标实例开通实例级 TDE 功能;若源数据库和目标实例所在账号(UIN)引用密钥不同,则需要将源数据库关闭加密或者将目标实例开启加密并引用相同密钥后再进行备份恢复。 说明: 备份恢复至跨账号(UIN)实例功能,仅密钥来源采用“由腾讯云提供”时的场景支持,密钥来源采用“由用户自定义”时的场景不支持。 |
DTS (热迁移) | DTS 迁移至源实例 | 同实例密钥一致,可进行迁移。 |
| DTS 迁移至同账号(UIN)下其他已有实例 | 已加密文件在做数据迁移时,需要具备源备份文件已关闭加密或目标实例开启加密的条件,才可以进行数据迁移。因此如果源数据库开启了 TDE 加密,而目标实例未开启实例级 TDE 加密,若密钥来源采用“由腾讯云提供”,由于同一账号(UIN)下的加密密钥相同,则系统会自动给目标实例开通实例级 TDE 功能;若密钥来源采“由用户自定义”,则需用户自行开启目标实例的 TDE 加密且需要保证与源实例的密钥相同。 |
| DTS 迁移至跨账号(UIN)实例 | 已加密文件在做数据迁移时,需要具备源备份文件已关闭加密或目标实例开启加密的条件,才可以进行数据迁移。因此当源数据库开启了 TDE 加密,而目标实例未开启实例级 TDE 加密时,若源数据库和目标实例所在账号(UIN)引用密钥相同,则系统会自动给目标实例开通实例级 TDE 功能;若源数据库和目标实例所在账号(UIN)引用密钥不同,则需要将源数据库关闭加密或者将目标实例开启加密并引用相同密钥后再进行数据迁移。 说明: DTS 迁移至跨账号(UIN)实例功能,仅密钥来源采用“由腾讯云提供”时的场景支持,密钥来源采用“由用户自定义”时的场景不支持。 |
发布订阅 | 从源实例链路到同地域下其他已有实例 | 发布订阅时系统会判定,具备源实例和目标实例密钥一致,或者源数据库关闭加密,或者目标实例开启加密且密钥一致的条件,才可以进行发布订阅。 |
相关 API
API | 描述 |
接口(ModifyInstanceEncryptAttributes)用于开通实例的 TDE 加密功能。 | |
接口(ModifyDBEncryptAttributes)用于开启、关闭数据库的 TDE 加密功能。 |
文档反馈

