- 动态与公告
- 产品动态
- 公告
- 关于云点播即时转码计费通知
- 关于云点播场景转码功能正式上线公告
- 关于播放器 SDK 移动端新增高级功能授权校验的公告
- 播放器 SDK Web 端新增 License 授权
- 关于云点播实时日志分析功能正式上线公告
- 关于云点播添加域名功能调整相关通知
- 关于云点播低频存储数据取回和应用管理功能正式商业计费公告
- 关于云点播音画质检测、播放频道功能正式上线公告
- 关于云点播 QUIC 下行加速功能正式上线公告
- 关于云点播音画质重生功能正式上线公告
- 关于云点播月结账号支持使用资源包的公告
- 关于云点播标签分账功能正式上线公告
- 关于云点播内容审核功能升级公告
- 关于点播播放器签名升级的公告
- 关于直播剪辑正式商业计费的公告
- 关于音视频内容识别正式商业计费的公告
- 关于播放器 SDK “startPlay”接口名变更的公告
- 关于TESHD(Tencent Extreme Speed High Definition)名称变更的公告
- 关于云点播视频加速功能计费价格调整公告
- 关于云点播境外功能正式上线和计费变更公告
- 关于云点播/视频处理变更转码计费规则的公告
- 产品简介
- 购买指南
- 快速入门
- 控制台指南
- 实践教程
- 开发指南
- 播放器 SDK 文档
- 服务端 API 文档
- History
- Introduction
- API Category
- Other APIs
- Media processing related API
- No longer recommended APIs
- Task Management APIs
- Media Upload APIs
- Media Management APIs
- Event Notification Relevant API
- Media Categorization APIs
- Domain Name Management APIs
- Distribution APIs
- AI-based Sample Management APIs
- Region Management APIs
- Statistics APIs
- Just In Time Transcode APIs
- Making API Requests
- AI-based image processing APIs
- Parameter Template APIs
- CreateWatermarkTemplate
- CreateSnapshotByTimeOffsetTemplate
- CreateSampleSnapshotTemplate
- CreateImageSpriteTemplate
- CreateAnimatedGraphicsTemplate
- CreateAdaptiveDynamicStreamingTemplate
- CreateAIAnalysisTemplate
- ModifyWatermarkTemplate
- ModifySnapshotByTimeOffsetTemplate
- ModifySampleSnapshotTemplate
- ModifyImageSpriteTemplate
- ModifyAnimatedGraphicsTemplate
- ModifyAdaptiveDynamicStreamingTemplate
- ModifyAIAnalysisTemplate
- DescribeTranscodeTemplates
- DescribeWatermarkTemplates
- ModifyAIRecognitionTemplate
- DescribeSnapshotByTimeOffsetTemplates
- DescribeSampleSnapshotTemplates
- DescribeImageSpriteTemplates
- DescribeAnimatedGraphicsTemplates
- DescribeAdaptiveDynamicStreamingTemplates
- DescribeAIAnalysisTemplates
- DeleteTranscodeTemplate
- DescribeAIRecognitionTemplates
- DeleteWatermarkTemplate
- DeleteSnapshotByTimeOffsetTemplate
- DeleteSampleSnapshotTemplate
- DeleteImageSpriteTemplate
- DeleteAnimatedGraphicsTemplate
- DeleteAdaptiveDynamicStreamingTemplate
- DeleteReviewTemplate
- DeleteAIRecognitionTemplate
- DeleteAIAnalysisTemplate
- DeleteHeadTailTemplate
- DeleteImageProcessingTemplate
- DescribeReviewTemplates
- CreateReviewTemplate
- CreateTranscodeTemplate
- ModifyReviewTemplate
- ModifyTranscodeTemplate
- CreateHeadTailTemplate
- CreateImageProcessingTemplate
- CreateAIRecognitionTemplate
- DescribeHeadTailTemplates
- DescribeImageProcessingTemplates
- ModifyHeadTailTemplate
- CreateQualityInspectTemplate
- DeleteQualityInspectTemplate
- DescribeQualityInspectTemplates
- ModifyQualityInspectTemplate
- CreateEnhanceMediaTemplate
- DeleteEnhanceMediaTemplate
- ModifyEnhanceMediaTemplate
- DescribeEnhanceMediaTemplates
- Task Flow APIs
- Playlist APIs
- Data Types
- Error Codes
- 常见问题
- 相关协议
- VOD 政策
- 联系我们
- 词汇表
- 动态与公告
- 产品动态
- 公告
- 关于云点播即时转码计费通知
- 关于云点播场景转码功能正式上线公告
- 关于播放器 SDK 移动端新增高级功能授权校验的公告
- 播放器 SDK Web 端新增 License 授权
- 关于云点播实时日志分析功能正式上线公告
- 关于云点播添加域名功能调整相关通知
- 关于云点播低频存储数据取回和应用管理功能正式商业计费公告
- 关于云点播音画质检测、播放频道功能正式上线公告
- 关于云点播 QUIC 下行加速功能正式上线公告
- 关于云点播音画质重生功能正式上线公告
- 关于云点播月结账号支持使用资源包的公告
- 关于云点播标签分账功能正式上线公告
- 关于云点播内容审核功能升级公告
- 关于点播播放器签名升级的公告
- 关于直播剪辑正式商业计费的公告
- 关于音视频内容识别正式商业计费的公告
- 关于播放器 SDK “startPlay”接口名变更的公告
- 关于TESHD(Tencent Extreme Speed High Definition)名称变更的公告
- 关于云点播视频加速功能计费价格调整公告
- 关于云点播境外功能正式上线和计费变更公告
- 关于云点播/视频处理变更转码计费规则的公告
- 产品简介
- 购买指南
- 快速入门
- 控制台指南
- 实践教程
- 开发指南
- 播放器 SDK 文档
- 服务端 API 文档
- History
- Introduction
- API Category
- Other APIs
- Media processing related API
- No longer recommended APIs
- Task Management APIs
- Media Upload APIs
- Media Management APIs
- Event Notification Relevant API
- Media Categorization APIs
- Domain Name Management APIs
- Distribution APIs
- AI-based Sample Management APIs
- Region Management APIs
- Statistics APIs
- Just In Time Transcode APIs
- Making API Requests
- AI-based image processing APIs
- Parameter Template APIs
- CreateWatermarkTemplate
- CreateSnapshotByTimeOffsetTemplate
- CreateSampleSnapshotTemplate
- CreateImageSpriteTemplate
- CreateAnimatedGraphicsTemplate
- CreateAdaptiveDynamicStreamingTemplate
- CreateAIAnalysisTemplate
- ModifyWatermarkTemplate
- ModifySnapshotByTimeOffsetTemplate
- ModifySampleSnapshotTemplate
- ModifyImageSpriteTemplate
- ModifyAnimatedGraphicsTemplate
- ModifyAdaptiveDynamicStreamingTemplate
- ModifyAIAnalysisTemplate
- DescribeTranscodeTemplates
- DescribeWatermarkTemplates
- ModifyAIRecognitionTemplate
- DescribeSnapshotByTimeOffsetTemplates
- DescribeSampleSnapshotTemplates
- DescribeImageSpriteTemplates
- DescribeAnimatedGraphicsTemplates
- DescribeAdaptiveDynamicStreamingTemplates
- DescribeAIAnalysisTemplates
- DeleteTranscodeTemplate
- DescribeAIRecognitionTemplates
- DeleteWatermarkTemplate
- DeleteSnapshotByTimeOffsetTemplate
- DeleteSampleSnapshotTemplate
- DeleteImageSpriteTemplate
- DeleteAnimatedGraphicsTemplate
- DeleteAdaptiveDynamicStreamingTemplate
- DeleteReviewTemplate
- DeleteAIRecognitionTemplate
- DeleteAIAnalysisTemplate
- DeleteHeadTailTemplate
- DeleteImageProcessingTemplate
- DescribeReviewTemplates
- CreateReviewTemplate
- CreateTranscodeTemplate
- ModifyReviewTemplate
- ModifyTranscodeTemplate
- CreateHeadTailTemplate
- CreateImageProcessingTemplate
- CreateAIRecognitionTemplate
- DescribeHeadTailTemplates
- DescribeImageProcessingTemplates
- ModifyHeadTailTemplate
- CreateQualityInspectTemplate
- DeleteQualityInspectTemplate
- DescribeQualityInspectTemplates
- ModifyQualityInspectTemplate
- CreateEnhanceMediaTemplate
- DeleteEnhanceMediaTemplate
- ModifyEnhanceMediaTemplate
- DescribeEnhanceMediaTemplates
- Task Flow APIs
- Playlist APIs
- Data Types
- Error Codes
- 常见问题
- 相关协议
- VOD 政策
- 联系我们
- 词汇表
使用须知
Demo 功能介绍
架构和流程
Demo 基于云函数(SCF)搭建了一个 HTTP 服务,用于接收来自客户端的获取防盗链签名请求。服务从请求 Body 中获取 VOD 的视频原始 URL,计算防盗链签名,并返回带防盗链签名的 URL 给客户端。
系统主要涉及四个组成部分:开发者、API 网关、云函数和云点播,其中 API 网关和云函数即是本 Demo 的部署对象,如下图所示:
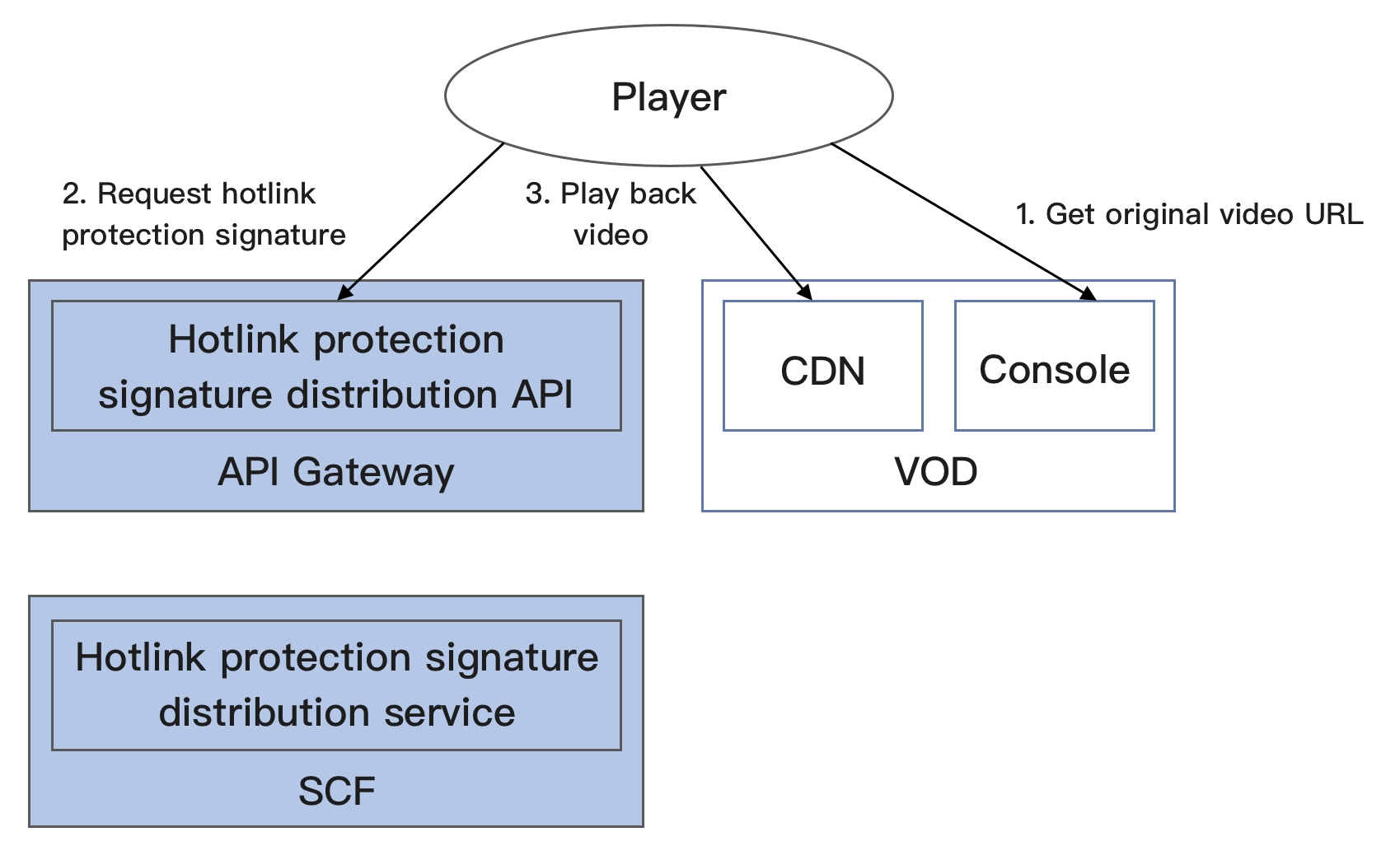

具体业务流程为:
1. 开发者在 VOD 控制台上获取到视频的原始 URL(实际生产环境中,应当是由播放器向业务后台请求视频的 URL,本文为了简化流程由开发者模拟该业务行为)。
2. 开发者使用视频原始 URL 向 SCF 请求防盗链签名。
3. 开发者使用带防盗链签名的视频 URL 请求 VOD CDN,播放视频。
说明:
Demo 中的 SCF 代码使用 Python3.6 进行开发,此外 SCF 还支持 Python2.7、Node.js、Golang、PHP 和 Java 等多种编程语言,开发者可以根据情况自由选择,具体请参考 SCF 开发指南。
费用
本文提供的云点播 Key 防盗链签名派发服务 Demo 是免费开源的,但在搭建和使用的过程中可能会产生以下费用:
购买腾讯云云服务器(CVM)用于执行服务部署脚本,详见 CVM 计费。
使用腾讯云 API 网关为 SCF 提供外网接口,详见 API 网关计费。
消耗云点播(VOD)存储用于存储上传的视频。
快速部署 Key 防盗链签名派发服务
步骤1:准备腾讯云 CVM
部署脚本需要运行在一台腾讯云 CVM 上,要求如下:
地域:任意。
机型:官网最低配置(1核1GB)即可。
公网:需要拥有公网 IP,带宽1Mbps或以上。
操作系统:官网公共镜像
Ubuntu Server 16.04.1 LTS 64位或Ubuntu Server 18.04.1 LTS 64位。注意:
Key 防盗链签名派发服务 Demo 本身并不依赖于 CVM,仅使用 CVM 来执行部署脚本。
如果您没有符合上述条件的腾讯云 CVM,也可以在其它带外网的 Linux(如 CentOS、Debian 等)或 Mac 机器上执行部署脚本,但需根据操作系统的区别修改脚本中的个别命令,具体修改方式请开发者自行搜索。
步骤2:开通云点播并配置 Key 防盗链
1. 参考 快速入门 - 步骤1 开通云点播服务。
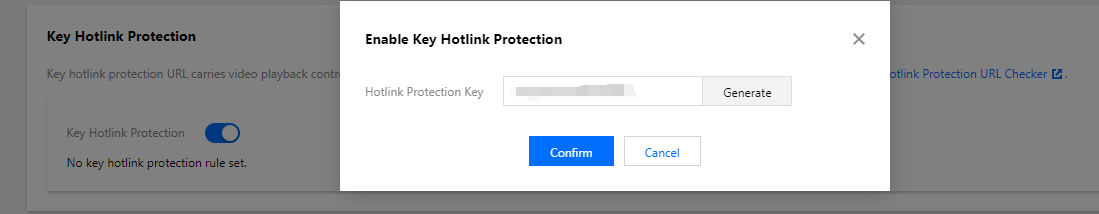
2. 开通完成后,参考 设置防盗链 文档启用 Key 防盗链,并记录下防盗链 Key:

注意:
此处是开通 Key 防盗链,而非开通 Referer 防盗链。如果您同步开通了 Referer 防盗链,那么下文的测试方法有可能因为不符合 Referer 防盗链的要求而导致请求失败。
步骤3:获取 API 密钥和 APPID
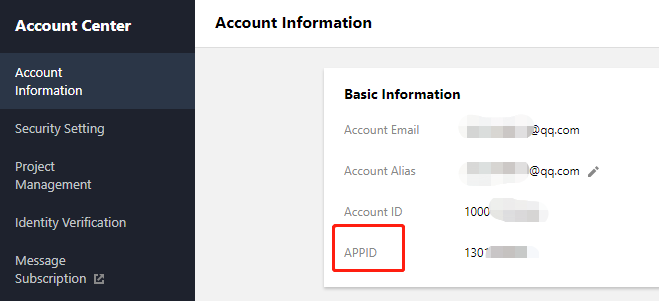
Key 防盗链签名派发服务 Demo 的部署和运行过程需要使用到开发者的 API 密钥(即 SecretId 和 SecretKey)和 APPID。
在控制台 账号信息 页面可以查看 APPID,如下图所示:

步骤4:部署防盗链签名派发服务
ubuntu@VM-69-2-ubuntu:~$ export SECRET_ID=AKxxxxxxxxxxxxxxxxxxxxxxx; export SECRET_KEY=xxxxxxxxxxxxxxxxxxxxx;export APPID=125xxxxxxx;export ANTI_LEECH_KEY=xxxx;git clone https://github.com/tencentyun/vod-server-demo.git ~/vod-server-demo; bash ~/vod-server-demo/installer/anti_leech_sign_scf_en.sh
该命令将从 Github 下载 Demo 源码并自动执行安装脚本。安装过程需几分钟(具体取决于 CVM 网络状况),期间远程终端会打印如下示例的信息:
[2020-06-04 15:57:10]开始检查npm。[2020-06-04 15:57:18]npm 安装成功。[2020-06-04 15:57:18]开始安装 ServerLess。[2020-06-04 15:57:19]serverless 安装成功。[2020-06-04 15:57:20]开始部署云点播 Key 防盗链签名派发服务。[2020-06-04 15:57:30]云点播 Key 防盗链签名派发服务部署完成。[2020-06-04 15:57:32]服务地址:https://service-xxxxxxxx-125xxxxxxx.gz.apigw.tencentcs.com/release/anti_leech_sign
复制输出日志中的签名派发服务地址(示例中的
https://service-xxxxxxxx-125xxxxxxx.gz.apigw.tencentcs.com/release/anti_leech_sign)。注意:
如果输出日志中出现如下所示的警告,一般是由于 CVM 无法立即解析刚部署好的服务域名,可尝试忽略该警告。
[2020-04-25 17:18:44]警告:Key 防盗链签名派发服务测试不通过。
步骤5:测试 Key 防盗链
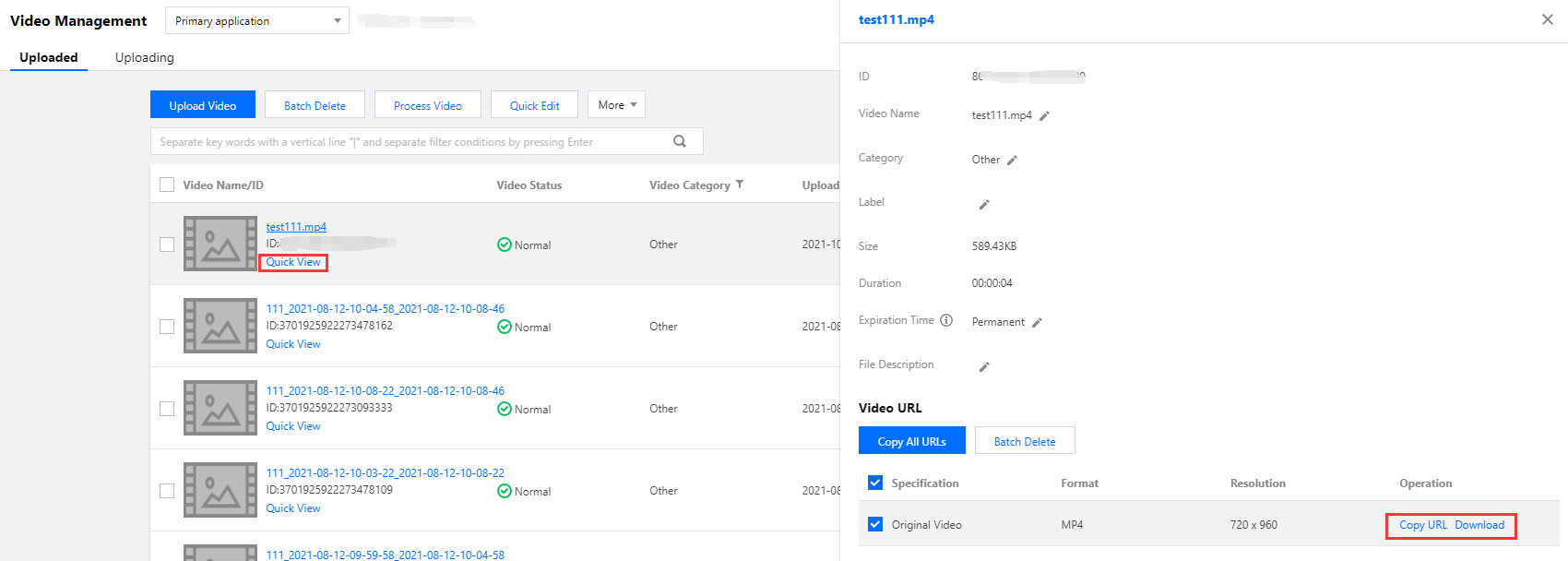
按照 上传视频 - 本地上传步骤 的说明,上传一个测试视频到云点播。上传完成后,单击快捷查看,然后单击右侧复制地址复制该视频的 URL。

curl命令尝试直接访问该 URL,结果会因不符合 Key 防盗链规则而被服务器拒绝访问,HTTP 返回码为403(测试时,请将命令中的 URL 替换为实际 URL,下同):ubuntu@VM-69-2-ubuntu:~$ curl -I "http://125xxxxxxx.vod2.myqcloud.com/f888c998vodcq125xxxxxxx/c849148f528xxxxxxxxxxxxxxxx/xxxxxxxxxx.mp4"HTTP/1.1 403 ForbiddenServer: NWS_VPConnection: keep-aliveDate: Thu, 04 Jun 2020 08:27:54 GMTContent-Type: text/plainContent-Length: 14
在 CVM 命令行执行
curl命令来请求步骤4中部署的服务,获取带防盗链签名的 URL(-d表示使用 POST 方式发起请求,所带的参数为视频 URL):ubuntu@VM-69-2-ubuntu:~$ curl -d 'http://125xxxxxxx.vod2.myqcloud.com/f888c998vodcq125xxxxxxx/c849148f528xxxxxxxxxxxxxxxx/xxxxxxxxxx.mp4' https://service-xxxxxxxx-125xxxxxxx.gz.apigw.tencentcs.com/release/anti_leech_sign; echohttp://125xxxxxxx.vod2.myqcloud.com/f888c998vodcq125xxxxxxx/c849148f528xxxxxxxxxxxxxxxx/xxxxxxxxxx.mp4?t=5ed8b8d2&exper=0&rlimit=0&us=455041&sign=fe6394007c2e7aef39fc70a02e897f69
再次使用
curl命令访问上一步得到的带防盗链签名的 URL,能够正常访问(HTTP 返回码为200):ubuntu@VM-69-2-ubuntu:~$ curl -I "http://125xxxxxxx.vod2.myqcloud.com/f888c998vodcq125xxxxxxx/c849148f528xxxxxxxxxxxxxxxx/xxxxxxxxxx.mp4?t=5ed8b8d2&exper=0&rlimit=0&us=455041&sign=fe6394007c2e7aef39fc70a02e897f69"HTTP/1.1 200 OKServer: tencent-cosConnection: keep-aliveDate: Thu, 04 Jun 2020 08:37:17 GMTLast-Modified: Fri, 22 May 2020 15:06:15 GMTContent-Type: video/mp4Content-Length: 232952632Accept-Ranges: bytesETag: "1da6be3a0d1da5edae4ff0b1feff02cf-223"x-cos-hash-crc64ecma: 16209801220610226954x-cos-request-id: NWVkOGIyYmVfZDUyMzYyNjRfYWMwMF85YjkyNzA=X-Daa-Tunnel: hop_count=4X-NWS-LOG-UUID: b404f43e-3c86-4c54-8a78-fb78e4e85cf2 add71e19fb08c6d9dbe1b21a2fb157bfAccess-Control-Allow-Credentials: trueAccess-Control-Allow-Headers: Origin,No-Cache,X-Requested-With,If-Modified-Since,Pragma,Last-Modified,Cache-Control,Expires,Content-Type,X_Requested_With,RangeAccess-Control-Allow-Methods: GET,POST,OPTIONSAccess-Control-Allow-Origin: *
说明:
您可以在浏览器中访问带防盗链签名的 URL,通过播放视频的方式来验证防盗链签名。但这种方式对视频格式有要求,一般来说使用 H.264 编码的 MP4 文件具有较好的兼容性,建议选用这类视频;您也可以使用 Postman 等第三方工具来发送 HTTP 请求,具体用法请自行搜索。
系统设计说明
接口协议
Key 防盗链签名派发云函数通过 API 网关对外提供接口,具体接口协议如下:
服务 | 云函数名 | 接口形式 | 请求内容 | 返回内容 |
Key 防盗链签名派发 | anti_leech_sign | HTTP POST | 视频原始 URL | 带防盗链签名 URL |
签名派发服务代码解读
1.
main_handler()为入口函数。2. 调用
parse_conf_file(),从config.json文件中读取配置信息。配置项说明如下(详细参数请参见 Key 防盗链签名参数):字段 | 数据类型 | 功能 |
key | String | Key 防盗链密钥 |
t | Integer | 签名有效时间,单位:秒。在处理请求时,该参数与 SCF 服务器的当前时间相加后,才是防盗链参数中的 t |
exper | Integer | 试看时长 |
rlimit | Integer | 签名最多允许被多少个客户端 IP 访问 |
3. 从请求 Body 中解析出
Dir参数,本地生成t和us参数,从配置文件中读取exper和rlimit参数:original_url = event["body"]parse_result = urlparse(original_url)directory = path.split(parse_result.path)[0] + '/'# 签名参数timestamp = int(time.time())rand = random.randint(0, 999999)sign_para = {"t": hex(timestamp + configuration['t'])[2:],"exper": configuration['exper'],"rlimit": configuration['rlimit'],"us": rand}
4. 调用
generate_sign()计算防盗链签名,详细算法请参见 Key 防盗链签名。5. 生成 QueryString,拼接在原始 URL 后组成带防盗链签名的 URL:
sign_para["sign"] = signaturequery_string = urlencode(sign_para)new_parse_result = parse_result._replace(query=query_string)signed_url = urlunparse(new_parse_result)
6. 返回签名。返回的数据格式及含义请参见 云函数集成响应。
return {"isBase64Encoded": False,"statusCode": 200,"headers": {"Content-Type": "text/plain; charset=utf-8","Access-Control-Allow-Origin": "*","Access-Control-Allow-Methods": "POST,OPTIONS"},"body": signed_url}

 是
是
 否
否
本页内容是否解决了您的问题?