控制台权限管理
最后更新时间:2025-01-16 17:56:09
腾讯云数据仓库 TCHouse-D 在控制台中提供了一个可视化界面,能够对集群便捷、高效地开展账户管理、权限管理操作。
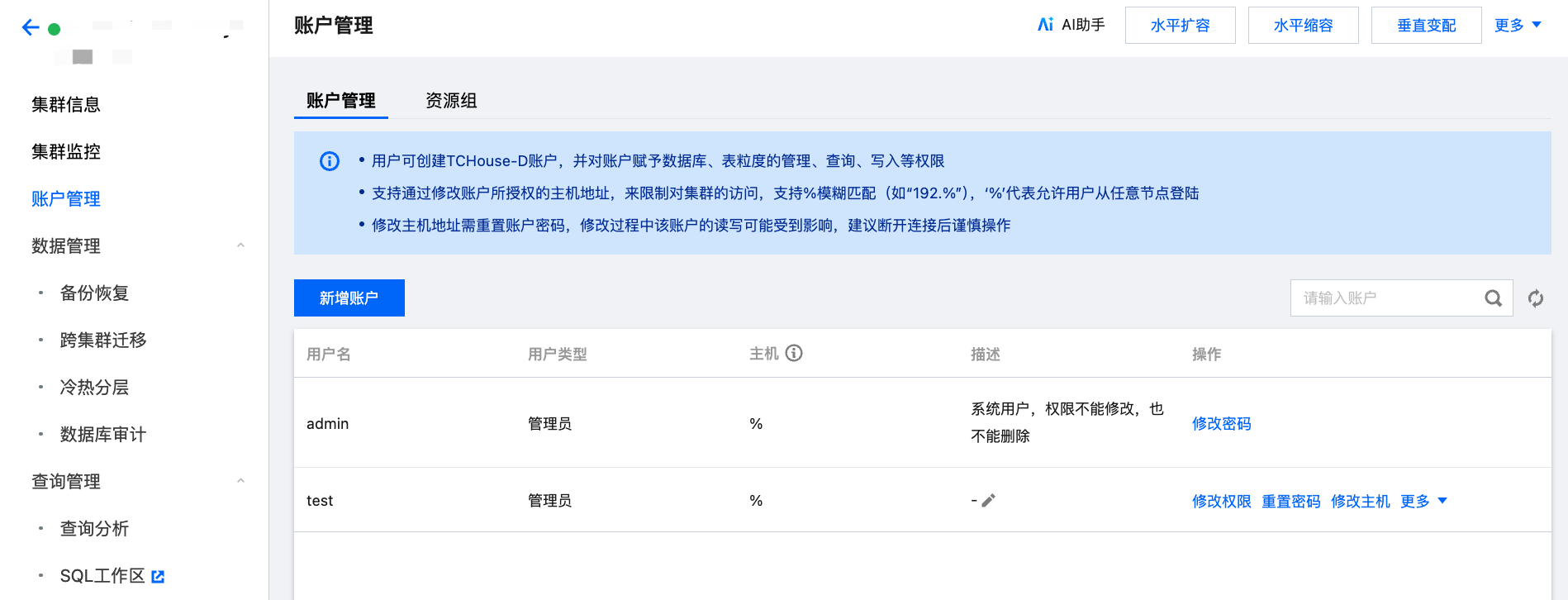
账户管理
1. 登录 腾讯云数据仓库 TCHouse-D 控制台,单击目标集群 ID/名称,跳转后可在左边列表中找到 账户管理 菜单。
2. 在账户管理页面中,提供了新增 / 删除账户、修改权限、重置密码功能。

新增账户
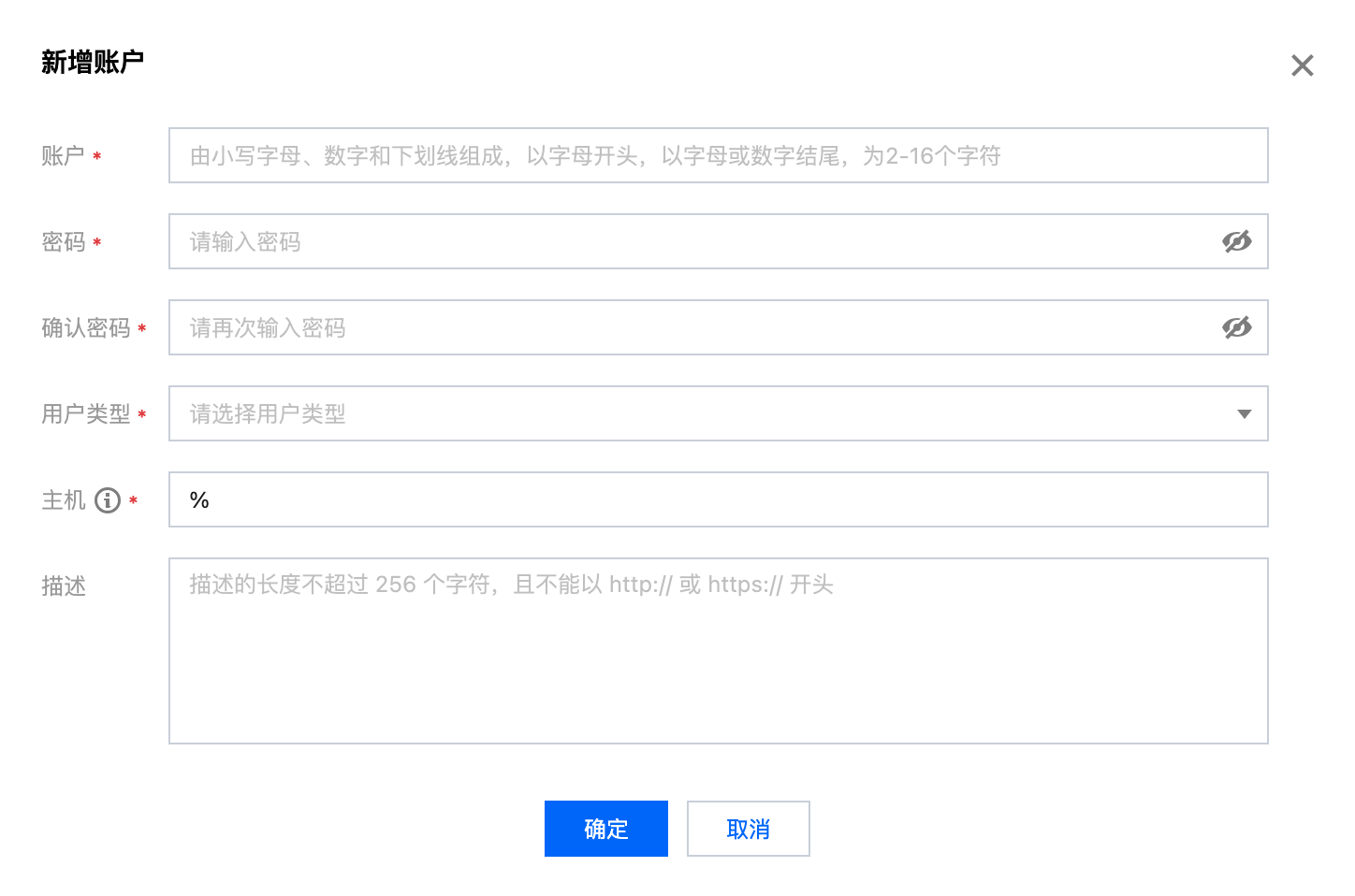
1. 单击新增账户按钮,填写账户、密码、主机和描述(选填),单击确定即可新增账户。
2. 新用户创建后默认仅对 information_schema 库及其中的表有读权限。
3. 用户类型:可选择管理员、普通用户,管理员无需额外授权即拥有所有库表的权限。
4. 主机:支持单个 IP 形式的地址,也支持填入%表示不做限制。

删除账户
删除操作不可逆,请在删除前确认该账户后续不再使用。
删除后,即使立即重新添加同名账户,权限也将初始化。
重置密码
腾讯云数据仓库 TCHouse-D 不支持查看已有账户的密码,仅允许通过控制台重置密码。
若忘记密码,建议操作如下:
若忘记 Admin 账户密码,请通过工单联系我们,进行密码重置。
若忘记子账户密码,可通过控制台重置其密码。
权限管理
用户列表单击 修改权限 可进到权限修改窗口,为普通用户授予内表及 Muticatalog 的权限,该窗口也可用来 查看权限。
管理员默认有所有库表的权限,无需额外授权。
内表权限-库/表权限批量设置:
可选择 internal 级别批量设置:进行 internal 级别授权后,将拥有 internal 下的所有库表权限。
可选择库级别批量设置:同时授权多个库。
可选择表级别批量设置:同时授权多个表。
内表权限-列级权限设置:
选定某个表后,可为此表的指定字段额外授予 Select 权限。
注:表级权限、列级权限会叠加生效,如“用户1”无“表 A”的权限,可额外为其授予“表 A”的指定列的 Select 权限。
Muticatalog外表权限:
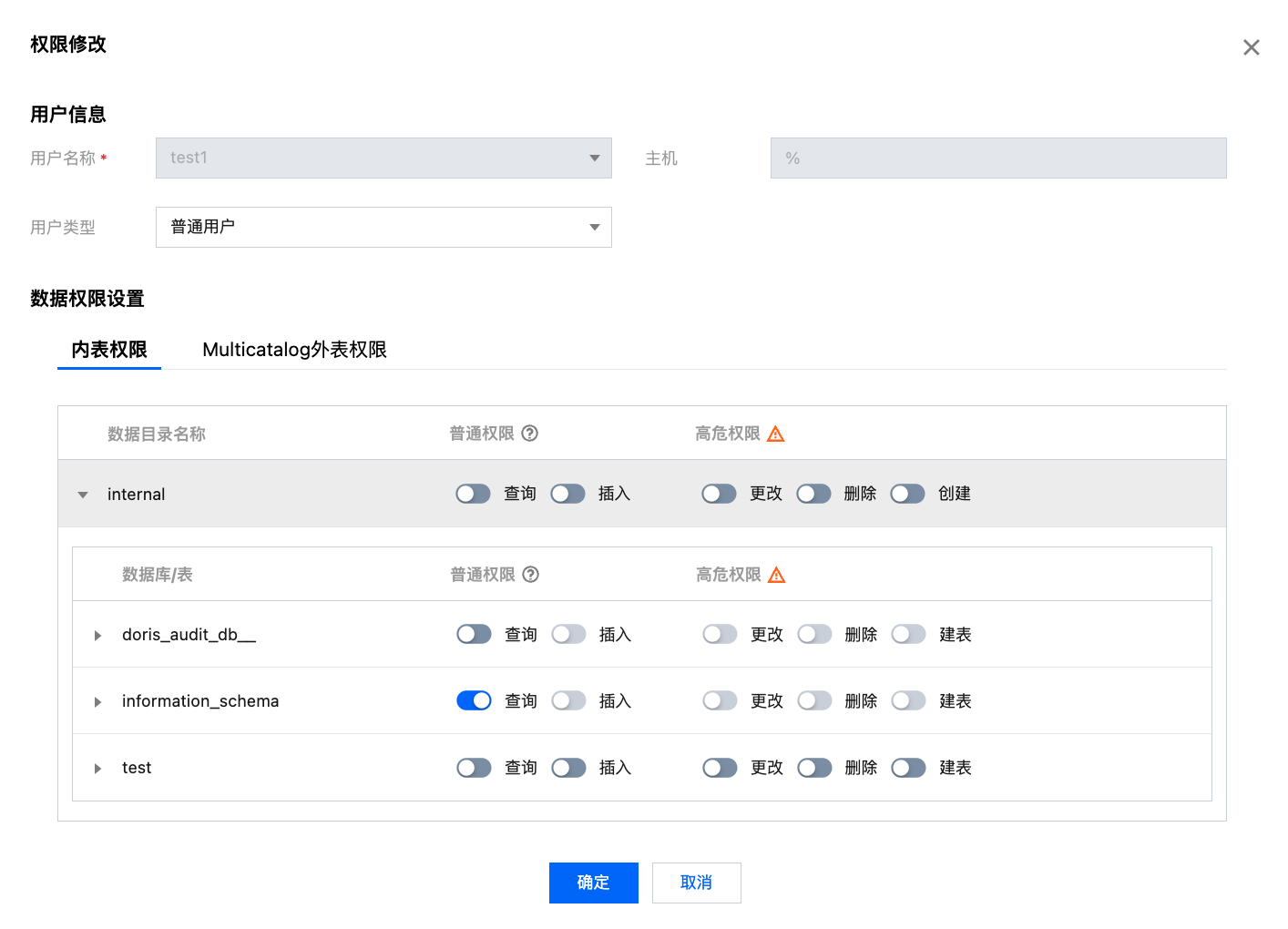

授权操作
授权范围:支持授予集群管理权限,或授予全局、数据目录、数据库/表权限。
授予集群管理权限:
开启后将授予用户集群管理权限(Admin_priv),包括全局范围内的查询、插入、更改、删除、创建权限。
授予全局、数据目录、数据库/表权限:
授予全局权限:授权将在全局范围生效。
授予数据目录权限:授权将对数据目录下所有库表生效。
授予库/表权限:可具体选定库、表后进行授权。
说明:
对于连通性正常的外部数据源,支持授予对应 Catalog 查询权限。
权限分类
对内部数据源(internal),可授予的权限包含普通权限和高危权限,具体分类如下:
普通权限:
查询:对数据库、表的只读权限(Select)。
插入:对数据库、表的写权限(Load、Insert、Delete)。
高危权限:
更改:对数据库表的更改权限,包括重命名库/表、添加/删除/变更列、添加/删除分区等操作(Alter)。
删除:删除数据库、表、视图的权限(Drop)。
创建:创建数据库、表、视图的权限(Create)。
对外部数据源(multi-catalog),仅支持授予查询权限。
修改授权访问的主机地址
您可以通过控制台设置、修改账号所授权的主机地址,来限制对集群的访问,进而提升集群安全性。
说明:
admin 账号不支持修改主机地址。
设置主机
新建账户时需设置主机(默认为%),支持单个 IP 形式的地址,也支持填入%表示不做限制。
允许创建账户名相同,主机不同的账户信息,权限、密码均相互独立。
说明:
支持%模糊匹配(如“192.%”),“%”代表允许用户从任意节点登录。
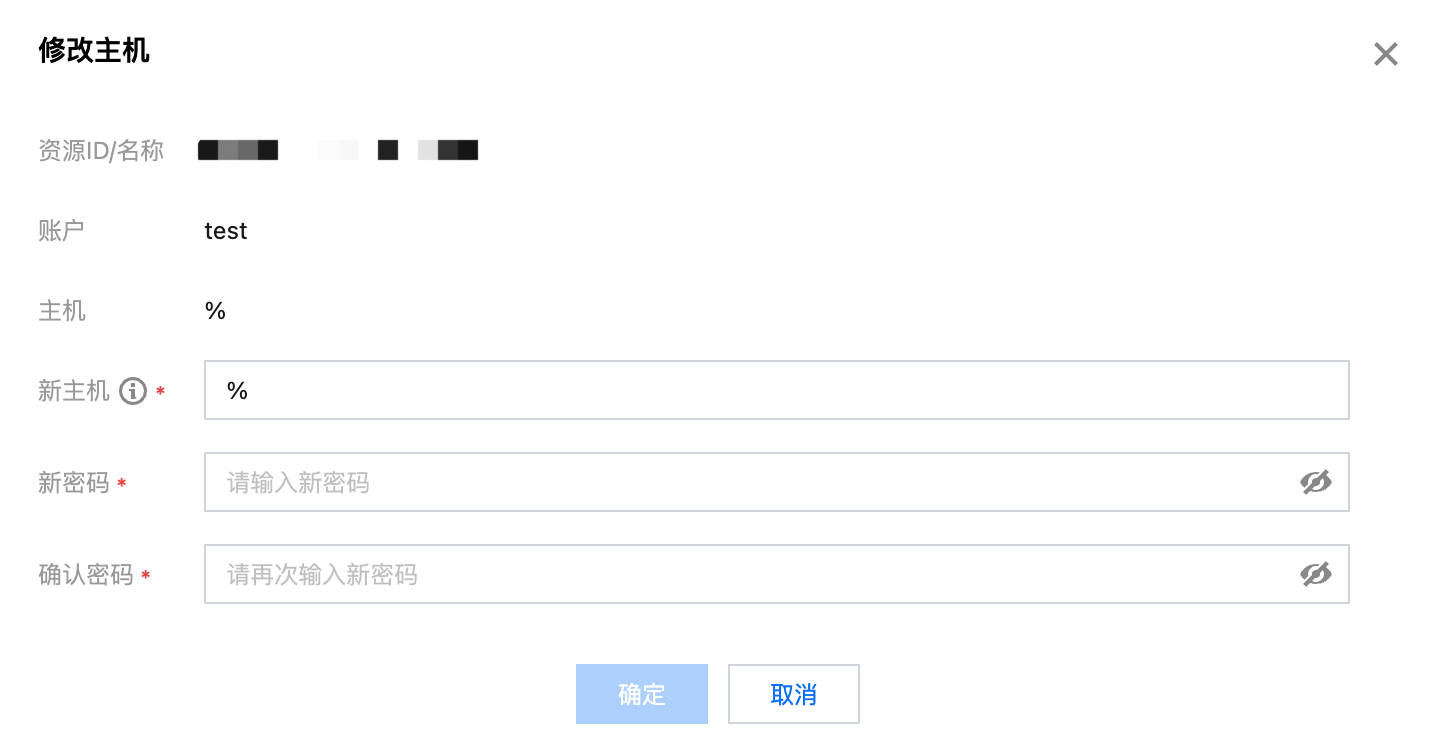
修改主机
修改主机地址需重置账户密码,修改过程中该账户的读写可能受到影响,建议断开连接后谨慎操作。

文档反馈

