- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Access Key
- User Groups
- Role
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Policies
- Permissions Boundary
- Troubleshooting
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Data Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Distributed cloud
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Image Creation
- AI Platform Service
- Natural Language Processing
- Optical Character Recognition
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Practical Tutorial
- Security Practical Tutorial
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- Authorizing Sub-account Full Access to COS Resources under the Account
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- Authorizing Sub-account Read-only Access to VPCs
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- User APIs
- DescribeSafeAuthFlagColl
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- Role APIs
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- GetRole
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Data Types
- Error Codes
- FAQs
- Glossary
- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Access Key
- User Groups
- Role
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Policies
- Permissions Boundary
- Troubleshooting
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Data Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Distributed cloud
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Image Creation
- AI Platform Service
- Natural Language Processing
- Optical Character Recognition
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Practical Tutorial
- Security Practical Tutorial
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- Authorizing Sub-account Full Access to COS Resources under the Account
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- Authorizing Sub-account Read-only Access to VPCs
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- User APIs
- DescribeSafeAuthFlagColl
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- Role APIs
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- GetRole
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Data Types
- Error Codes
- FAQs
- Glossary
When a Tencent Cloud user accesses Tencent Cloud resources, CAM determines whether to allow or deny the request by using the following evaluation logic:
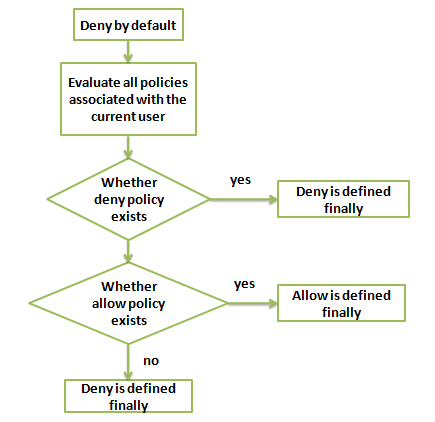

1. All requests will be denied by default.
2. CAM will check all the policies currently associated with the user.
1. It will determine whether any policies match, and if so, it will proceed to the next step. If not, the final result is "deny", and access to Tencent Cloud resources is not permitted.
2. It will determine whether any "deny" policies match, and if so, the final result will be "deny", and access to Tencent Cloud resources is not permitted. If not, it will proceed to the next step.
3. It will determine whether any "allow" policies match, and if so, the final result will be "allow", and access to Tencent Cloud resources will be permitted. If not, the final result is "deny", and access to Tencent Cloud resources is not permitted.
Note:
A root account has full access to all resources it owns by default. At present, cross-account resource access is only supported for COS.
There are some general policies that are associated with all CAM users by default. For more information, please see the General Policy Table below.
Other policies need to be explicitly specified. This applies to both allow and deny policies.
For services that support cross-account resource access, permission propagation applies. For example, if root account A grants a sub-account under root account B access to its resources, CAM will verify whether root account A has granted root account B access and whether root account B has granted the sub-account access. Both must be true for the sub-account of root account B to be allowed to access root account A's resources.A root account has full access to all resources it owns by default. At present, cross-account resource access is only supported for COS.
The followin
g table lis
ts currently supported general policies:Policy Description | Policy Definition |
MFA verification is required for querying keys | { "principal":"", "action":"account:QueryKeyBySecretId", "resource":"", "condition":{"string_equal":{"mfa":"0"}} } |
MFA verification is required for sensitive configurations | { "principal":"", "action":"account:SetSafeAuthFlag", "resource":"", "condition":{"string_equal":{"mfa":"0"}} } |
MFA verification is required for binding tokens | { "principal":"", "action":"account:BindToken", "resource":"", "condition":{"string_equal":{"mfa":"0"}} } |
MFA verification is required for unbinding tokens | { "principal":"", "action":"account:UnbindToken", "resource":"", "condition":{"string_equal":{"mfa":"0"}} } |
MFA verification is required for modifying email addresses | { "principal":"", "action":"account:ModifyMail", "resource":"", "condition":{"string_equal":{"mfa":"0"}} } |
MFA verification is required for modifying mobile numbers | { "principal":"", "action":"account:ModifyPhoneNum", "resource":"", "condition":{"string_equal":{"mfa":"0"}} } |

 예
예
 아니오
아니오
문제 해결에 도움이 되었나요?