- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Access Key
- User Groups
- Role
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Policies
- Permissions Boundary
- Troubleshooting
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Data Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Distributed cloud
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Image Creation
- AI Platform Service
- Natural Language Processing
- Optical Character Recognition
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Practical Tutorial
- Security Practical Tutorial
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- Authorizing Sub-account Full Access to COS Resources under the Account
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- Authorizing Sub-account Read-only Access to VPCs
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- User APIs
- DescribeSafeAuthFlagColl
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Role APIs
- GetRole
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- Data Types
- Error Codes
- FAQs
- Glossary
- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Access Key
- User Groups
- Role
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Policies
- Permissions Boundary
- Troubleshooting
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Data Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Distributed cloud
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Image Creation
- AI Platform Service
- Natural Language Processing
- Optical Character Recognition
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Practical Tutorial
- Security Practical Tutorial
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- Authorizing Sub-account Full Access to COS Resources under the Account
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- Authorizing Sub-account Read-only Access to VPCs
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- User APIs
- DescribeSafeAuthFlagColl
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Role APIs
- GetRole
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- Data Types
- Error Codes
- FAQs
- Glossary
Overview
This document describes how to create a policy to resolve a fault according to the fault report. After the fault is resolved, the sub-account will be able to manage the resources of the root account within the scope of the newly configured permissions.
Example
When a sub-account associated with the 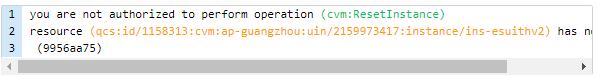
QcloudCVMReadOnlyAccess policy attempts to reinstall a CVM instance, the following error is reported:

Directions
1. Log in to the CAM console, enter the Policies page, and click Create Custom Policy.
2. In the selection window that pops up, click Create by Policy Generator to enter the Edit Policy page.
3. On the
Edit Po
licy page, set the following information:Effect (required): select whether the operation is allowed. In this example, select "Allow".
Service (required): select the product based on the abbreviation to authorize. In this example, it is CVM corresponding to
cvm in the operation field of the error message.Action (required): select the operation to authorize. In this example, select ResetInstance corresponding to the
operation field of the error message.Resource (required): for products that don't support resource-level authorization, you can only select all resources as the authorization granularity. For products that support resource-level authorization, you can select a specific resource. To do so, click Add a six-segment resource description and enter the resource prefix and resource. In this example, the error message is for a specific resource, so you need to authorize it: select the specific resource, click Add a six-segment resource description, and then you can directly copy the prefix and resource in
qcs:id/1158313:cvm:ap-guangzhou:uin/2159973417:instance/instance/ins-esuithv2 and paste them.Condition (optional): set the conditions that must be met for the permission to take effect, such as a specified access IP. In this example, leave it empty.
4. Click Next to enter the Associate Users/User Groups page.
5. On the Associate Users/User Groups page, add the policy name (automatically generated by the console) and description.
Note:
The policy name is
policygen suffixed with the creation time by default, which is customizable.The policy description corresponds to the service and operations selected in step 3. You can modify them as needed.
6. Click Done to complete the custom policy creation.
7. Authorize the sub-account as instructed in Authorization Management. After authorization, the sub-account will be granted the needed permission, and the fault will be resolved.

 예
예
 아니오
아니오
문제 해결에 도움이 되었나요?