- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Access Key
- User Groups
- Role
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Policies
- Permissions Boundary
- Troubleshooting
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Data Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Distributed cloud
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Image Creation
- AI Platform Service
- Natural Language Processing
- Optical Character Recognition
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Practical Tutorial
- Security Practical Tutorial
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- Authorizing Sub-account Full Access to COS Resources under the Account
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- Authorizing Sub-account Read-only Access to VPCs
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- User APIs
- DescribeSafeAuthFlagColl
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Role APIs
- GetRole
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- Data Types
- Error Codes
- FAQs
- Glossary
- Product Introduction
- Purchase Guide
- Getting Started
- User Guide
- Overview
- Users
- Access Key
- User Groups
- Role
- Identity Provider
- SSO Overview
- Practical Scenarios for SSO
- User-Based SSO
- Role-Based SSO
- Overview
- Overview of SAML Role-Based SSO
- Overview of OIDC Role-Based Single Sign-On
- SAML 2.0-Based Federation
- Accessing Tencent Cloud Console as SAML 2.0 Federated Users
- Creating a SAML IdP
- Creating an OIDC Identity Provider
- Managing IdPs
- Azure Active Directory Single Sign-On
- OneLogin Single Sign-On
- Okta Single Sign-On
- ADFS SSO to Tencent Cloud
- Implementing OIDC-Based Role-Based SSO
- Policies
- Permissions Boundary
- Troubleshooting
- Downloading Security Analysis Report
- CAM-Enabled Role
- Overview
- Compute
- Container
- Microservice
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Data Security
- Application Security
- Domains & Websites
- Big Data
- Middleware
- Interactive Video Services
- Media On-Demand
- Cloud Real-time Rendering
- Game Services
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- CAM-Enabled API
- Overview
- Compute
- Edge Computing
- Container
- Distributed cloud
- Microservice
- Serverless
- Essential Storage Service
- Data Process and Analysis
- Data Migration
- Relational Database
- Enterprise Distributed DBMS
- NoSQL Database
- Database SaaS Tool
- Networking
- CDN and Acceleration
- Network Security
- Endpoint Security
- Data Security
- Business Security
- Application Security
- Domains & Websites
- Big Data
- Voice Technology
- Image Creation
- AI Platform Service
- Natural Language Processing
- Optical Character Recognition
- Middleware
- Communication
- Interactive Video Services
- Stream Services
- Media On-Demand
- Media Process Services
- Cloud Real-time Rendering
- Game Services
- Education Sevices
- Cloud Resource Management
- Management and Audit Tools
- Monitor and Operation
- More
- Practical Tutorial
- Security Practical Tutorial
- Multi-Identity Personnel Permission Management
- Authorizing Certain Operations by Tag
- Supporting Isolated Resource Access for Employees
- Enterprise Multi-Account Permissions Management
- Reviewing Employee Operation Records on Tencent Cloud
- Implementing Attribute-Based Access Control for Employee Resource Permissions Management
- During tag-based authentication, only tag key matching is supported
- Business Use Cases
- TencentDB for MySQL
- CLB
- CMQ
- COS
- Authorizing Sub-account Full Access to Specific Directory
- Authorizing Sub-account Read-only Access to Files in Specific Directory
- Authorizing Sub-account Read/Write Access to Specific File
- Authorizing Sub-account Read-only Access to COS Resources
- Authorizing a Sub-account Read/Write Access to All Files in Specified Directory Except Specified Files
- Authorizing Sub-account Read/Write Access to Files with Specified Prefix
- Authorizing Another Account Read/Write Access to Specific Files
- Authorizing Cross-Account ’s Sub-account Read/Write Access to Specified File
- Authorizing Sub-account Full Access to COS Resources under the Account
- CVM
- Authorizing Sub-account Full Access to CVMs
- Authorizing Sub-account Read-only Access to CVMs
- Authorizing Sub-account Read-only Access to CVM-related Resources
- Authorizing Sub-account Access to Perform Operations on CBSs
- Authorizing Sub-account Access to Perform Operations on Security Groups
- Authorizing Sub-account Access to Perform Operations on EIPs
- Authorizing Sub-account Access to Perform Operations on Specific CVM
- Authorizing Sub-account Access to Perform Operations on CVMs in Specific Region
- Authorizing Sub-account Full Access to CVMs Except Payment
- VPC
- Authorizing Sub-account Access to Perform Operations on Specific VPC and Resources of This VPC
- Authorizing Sub-account Access to Perform Operations on VPC Except on Routing Table
- Authorizing Sub-account Access to Perform Operations on VPN
- Authorizing Sub-account Full Access to VPCs
- Authorizing a Sub-account Full Access to VPCs Except Payment
- Authorizing Sub-account Read-only Access to VPCs
- VOD
- Others
- API Documentation
- History
- Introduction
- API Category
- User APIs
- DescribeSafeAuthFlagColl
- CreateGroup
- UpdateUser
- UpdateGroup
- RemoveUserFromGroup
- ListUsersForGroup
- ListUsers
- ListGroupsForUser
- ListGroups
- GetUser
- GetGroup
- DeleteUser
- DeleteGroup
- AddUserToGroup
- AddUser
- SetMfaFlag
- GetCustomMFATokenInfo
- ConsumeCustomMFAToken
- ListCollaborators
- ListAccessKeys
- PutUserPermissionsBoundary
- DeleteUserPermissionsBoundary
- DescribeSubAccounts
- GetSecurityLastUsed
- GetAccountSummary
- GetUserAppId
- UpdateAccessKey
- DeleteAccessKey
- CreateAccessKey
- Role APIs
- GetRole
- UpdateRoleDescription
- UpdateAssumeRolePolicy
- ListAttachedRolePolicies
- DetachRolePolicy
- DescribeRoleList
- DeleteRole
- CreateRole
- AttachRolePolicy
- UpdateRoleConsoleLogin
- GetServiceLinkedRoleDeletionStatus
- DeleteServiceLinkedRole
- CreateServiceLinkedRole
- PutRolePermissionsBoundary
- DeleteRolePermissionsBoundary
- DescribeSafeAuthFlag
- DescribeSafeAuthFlagIntl
- UntagRole
- TagRole
- Making API Requests
- Identity Provider APIs
- Policy APIs
- UpdatePolicy
- ListPolicies
- ListEntitiesForPolicy
- ListAttachedUserPolicies
- ListAttachedGroupPolicies
- GetPolicy
- DetachUserPolicy
- DetachGroupPolicy
- DeletePolicy
- CreatePolicy
- AttachUserPolicy
- AttachGroupPolicy
- SetDefaultPolicyVersion
- ListPolicyVersions
- GetPolicyVersion
- DeletePolicyVersion
- CreatePolicyVersion
- ListAttachedUserAllPolicies
- Data Types
- Error Codes
- FAQs
- Glossary
Overview
This document describes how to grant permissions by resource ID to allow the sub-user
cvmtest01 only to manage the resource-level APIs of ins-duglsqg0.
For more information, see overview >>Policy Content
To grant permissions by resource ID to implement the above need, use the following policy content:
{"version": "2.0","statement": [{"effect": "allow","action": ["cvm:*"],"resource": ["qcs::cvm::uin/12345678:instance/ins-duglsqg0",// `12345678` is `UIN` of the root account"qcs::cvm::uin/12345678:image/img-eb30mz89"]},{"effect": "allow","action": ["vpc:DescribeVpcEx","vpc:DescribeNetworkInterfaces","cvm:DescribeCbsStorages"],"resource": ["*"]}]}
Directions
Step 1. Use the admin account to create a policy and configure permissions
1. Log in to the CAM console with the admin account. On the Policy page, create a custom policy with the policy generator as instructed in Creating Custom Policy > Creating by policy generator.
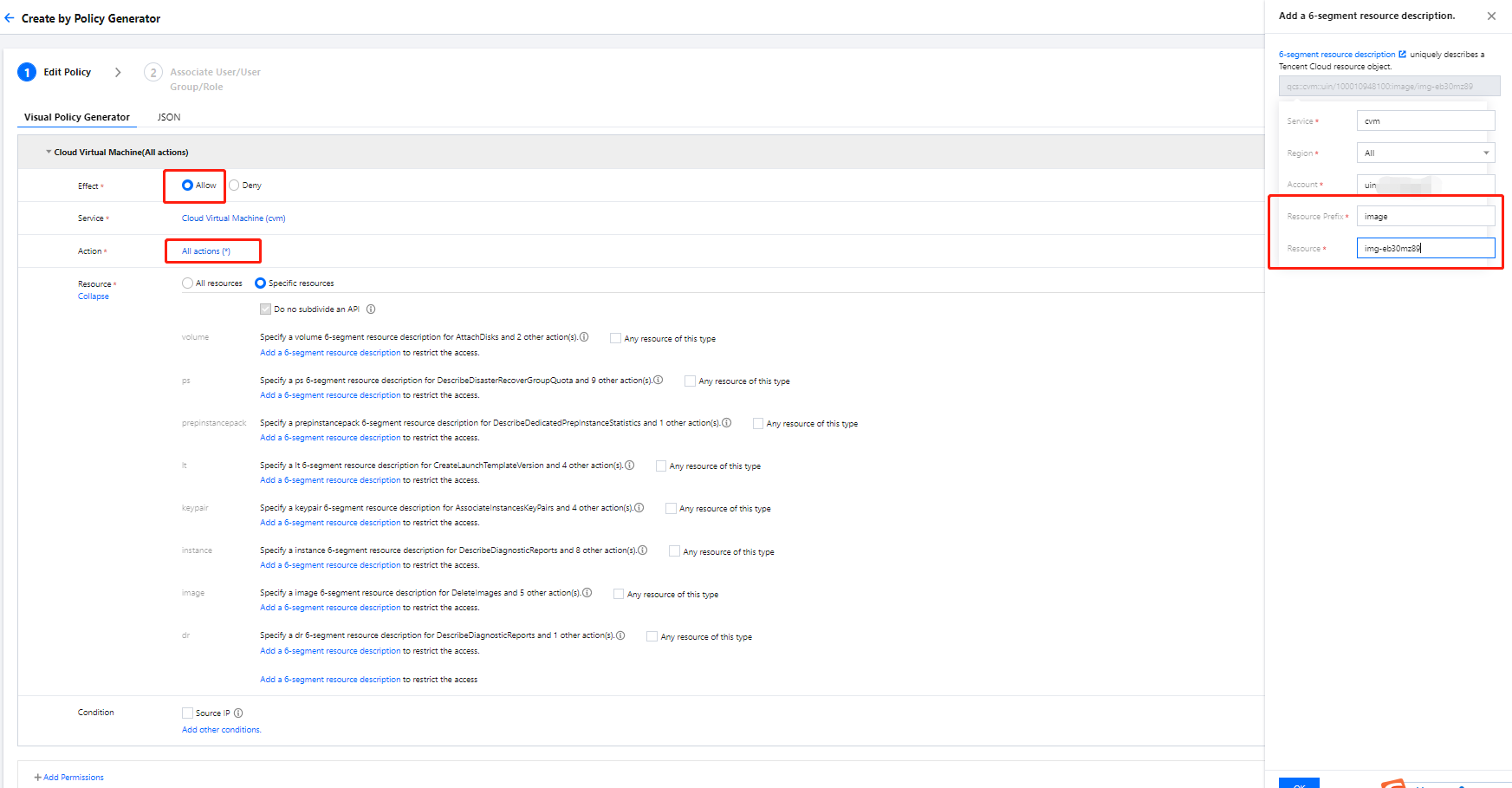

Effect: Allowed
Service: CVM
Operation: All
Resource: Specific Resources > Add a custom six-segment resource description
Enter the resource prefixes
instance and image and resource IDs ins-duglsqg0 and img-eb30mz89 respectively.Note:
How to determine the resource prefix: You can view the CVM six-segment resource description in CAM APIs supported by CVM.
In addition to CVM APIs, APIs of other Tencent Cloud products such as VPC will also be used on the CVM product page. In this example, you can skip them and directly generate the policy. However, during actual operations, you need to add such APIs as prompted in CAM.
2. Click Next, name the policy
cvm-test01, and grant it to the sub-account cvmtest01.3. Click Complete.
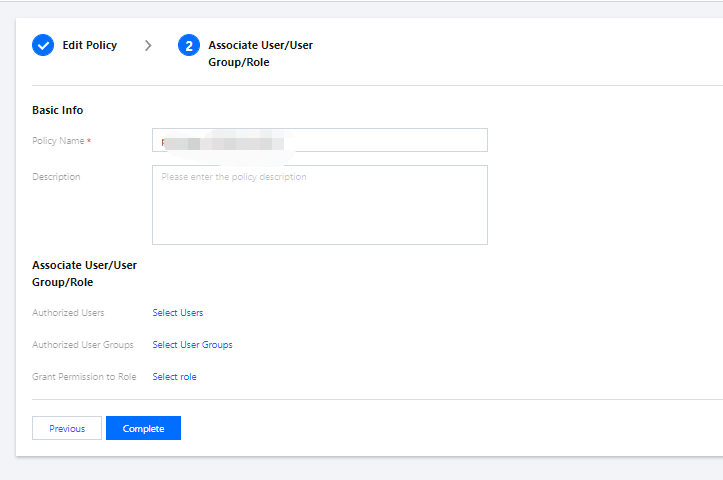

Step 2. Use the sub-account to log in and verify permissions
1. Log in to the CVM console with the sub-user account and enter the instance list page. The page prompts that
DescribeVpcEx and relevant resource permissions of VPC are missing.2. Contact the admin account to add such permissions to the policy as prompted.
Step 3. Use the admin account to adjust the policy content
1. Use the root account to find the
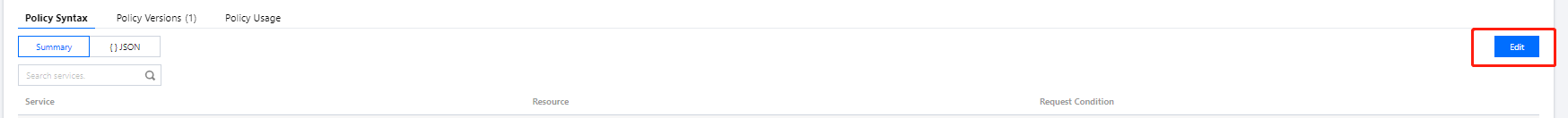
DescribeVpcEx API in the list of CAM APIs supported by VPC and verify that the API is at the operation level.2. On the Policy page in the CAM console, find the
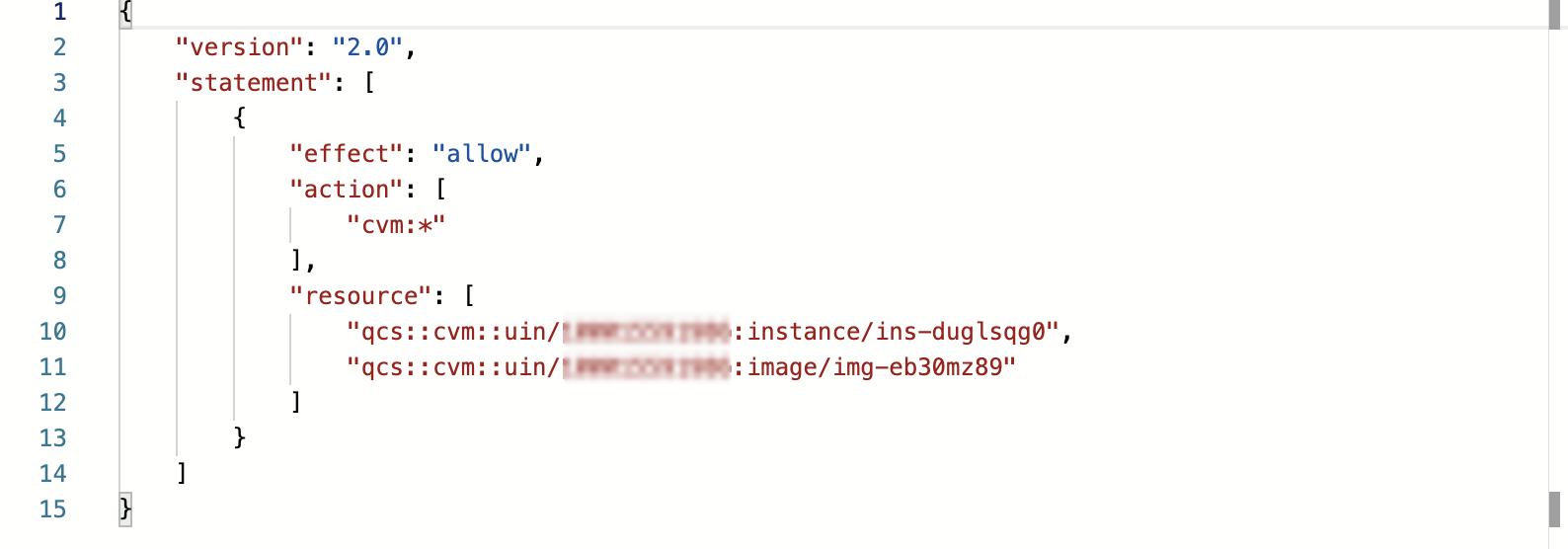
cvm-test01 policy and click its name to enter the policy details page.3. In the policy syntax, click Edit and add API authorization to the policy details in the format of operation-level API authorization.
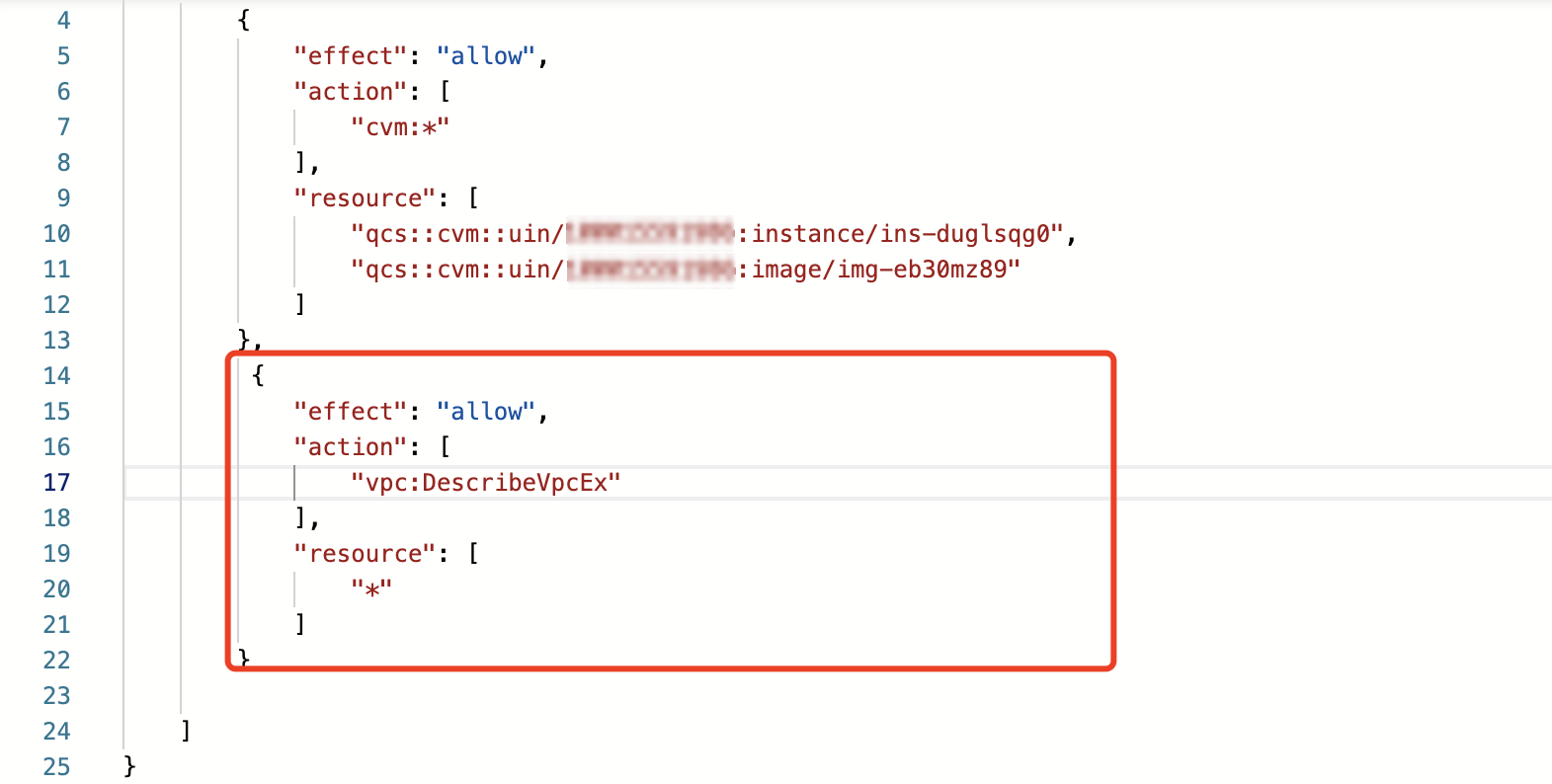



4. Repeat step 2 to use the sub-account
cvmtest01 to verify permissions again, and you can see that DescribeNetworkInterfaces and relevant resource access permissions of VPC are still missing. View the list of CAM APIs supported by VPC and verify that the DescribeNetworkInterfaces API is at the operation level. 5. Repeat step 3 to adjust the policy content until the system no longer reports errors.
The eventual policy content is as follows:
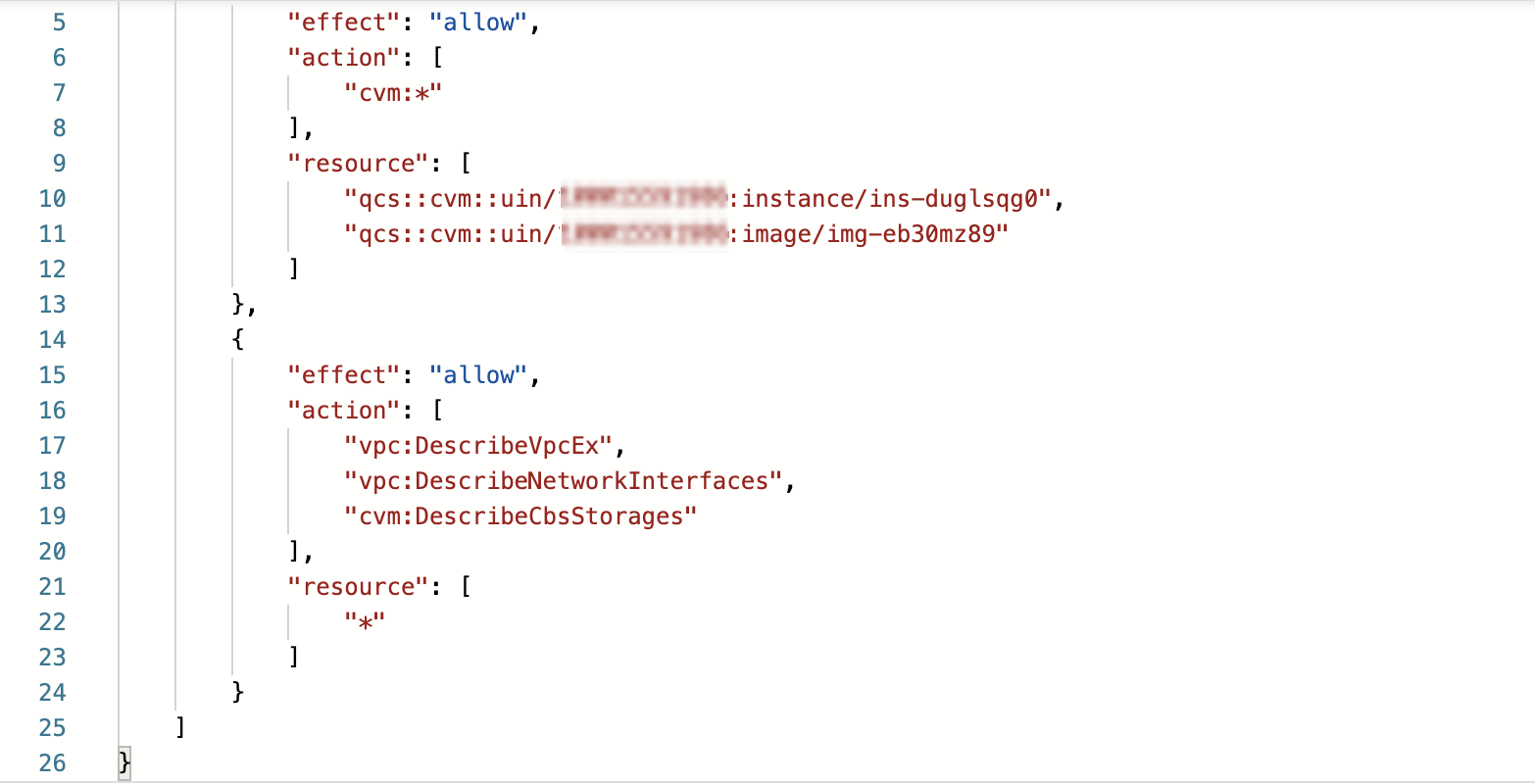

Note:
When writing a CAM policy, if you want to manipulate a specific resource, you need to separate the resource-level API authorization from operation-level API authorization, but you can put multiple operation-level APIs together.
Step 4. Verify the result
Use the sub-user 
cvmtest01 to verify the policy again, and the expected effect is achieved.
At this point, the sub-user cvmtest01 can start, shut down, restart, rename, and reset the password of the CVM instance.


 예
예
 아니오
아니오
문제 해결에 도움이 되었나요?