- 动态与公告
- 产品简介
- 购买指南
- 快速入门
- TKE 标准集群指南
- TKE 标准集群概述
- 购买 TKE 标准集群
- 容器服务高危操作
- 云上容器应用部署 Check List
- 开源组件
- 权限管理
- 集群管理
- 镜像
- Worker 节点介绍
- 普通节点管理
- 原生节点管理
- 超级节点管理
- 注册节点管理
- 内存压缩
- GPU 共享
- Kubernetes 对象管理
- Service 管理
- Ingress 管理
- 存储管理
- 策略管理
- 应用与组件功能管理说明
- 组件管理
- 扩展组件概述
- 组件的生命周期管理
- Cluster Autoscaler 说明
- OOMGuard 说明
- NodeProblemDetectorPlus 说明
- NodeLocalDNSCache 说明
- DNSAutoscaler 说明
- COS-CSI 说明
- CFS-CSI 说明
- CFSTURBO-CSI 说明
- CBS-CSI 说明
- UserGroupAccessControl 说明
- TCR 说明
- TCR Hosts Updater
- DynamicScheduler 说明
- DeScheduler 说明
- Network Policy 说明
- Nginx-ingress 说明
- HPC 说明
- tke-monitor-agent 说明
- tke-log-agent 说明
- GPU-Manager 说明
- 应用管理
- 应用市场
- 网络管理
- 集群运维
- 日志管理
- 备份中心
- 远程终端
- TKE Serverless 集群指南
- TKE 注册集群指南
- TKE Insight
- TKE 调度
- 云原生服务指南
- 实践教程
- 集群
- 集群迁移
- Serverless 集群
- 调度
- 安全
- 服务部署
- 网络
- 发布
- 日志
- 监控
- 运维
- Terraform
- DevOps
- 弹性伸缩
- 容器化
- 微服务
- 成本管理
- 混合云
- 故障处理
- API 文档
- History
- Introduction
- API Category
- Making API Requests
- Elastic Cluster APIs
- Resource Reserved Coupon APIs
- Cluster APIs
- AcquireClusterAdminRole
- CreateClusterEndpoint
- CreateClusterEndpointVip
- DeleteCluster
- DeleteClusterEndpoint
- DeleteClusterEndpointVip
- DescribeAvailableClusterVersion
- DescribeClusterAuthenticationOptions
- DescribeClusterCommonNames
- DescribeClusterEndpointStatus
- DescribeClusterEndpointVipStatus
- DescribeClusterEndpoints
- DescribeClusterKubeconfig
- DescribeClusterLevelAttribute
- DescribeClusterLevelChangeRecords
- DescribeClusterSecurity
- DescribeClusterStatus
- DescribeClusters
- DescribeEdgeAvailableExtraArgs
- DescribeEdgeClusterExtraArgs
- DescribeResourceUsage
- DisableClusterDeletionProtection
- EnableClusterDeletionProtection
- GetClusterLevelPrice
- GetUpgradeInstanceProgress
- ModifyClusterAttribute
- ModifyClusterAuthenticationOptions
- ModifyClusterEndpointSP
- UpgradeClusterInstances
- CreateBackupStorageLocation
- CreateCluster
- DeleteBackupStorageLocation
- DescribeBackupStorageLocations
- DescribeEncryptionStatus
- DisableEncryptionProtection
- EnableEncryptionProtection
- UpdateClusterKubeconfig
- UpdateClusterVersion
- Third-party Node APIs
- Network APIs
- Node APIs
- Node Pool APIs
- TKE Edge Cluster APIs
- CheckEdgeClusterCIDR
- DescribeAvailableTKEEdgeVersion
- DescribeECMInstances
- DescribeEdgeCVMInstances
- DescribeEdgeClusterInstances
- DescribeEdgeClusterUpgradeInfo
- DescribeTKEEdgeClusterStatus
- ForwardTKEEdgeApplicationRequestV3
- DescribeEdgeLogSwitches
- CreateECMInstances
- CreateEdgeCVMInstances
- CreateEdgeLogConfig
- DeleteECMInstances
- DeleteEdgeCVMInstances
- DeleteEdgeClusterInstances
- DeleteTKEEdgeCluster
- DescribeTKEEdgeClusterCredential
- DescribeTKEEdgeExternalKubeconfig
- DescribeTKEEdgeScript
- InstallEdgeLogAgent
- UninstallEdgeLogAgent
- UpdateEdgeClusterVersion
- DescribeTKEEdgeClusters
- CreateTKEEdgeCluster
- Cloud Native Monitoring APIs
- Scaling group APIs
- Super Node APIs
- Add-on APIs
- Other APIs
- Data Types
- Error Codes
- TKE API 2022-05-01
- 常见问题
- 服务协议
- 联系我们
- 词汇表
- 动态与公告
- 产品简介
- 购买指南
- 快速入门
- TKE 标准集群指南
- TKE 标准集群概述
- 购买 TKE 标准集群
- 容器服务高危操作
- 云上容器应用部署 Check List
- 开源组件
- 权限管理
- 集群管理
- 镜像
- Worker 节点介绍
- 普通节点管理
- 原生节点管理
- 超级节点管理
- 注册节点管理
- 内存压缩
- GPU 共享
- Kubernetes 对象管理
- Service 管理
- Ingress 管理
- 存储管理
- 策略管理
- 应用与组件功能管理说明
- 组件管理
- 扩展组件概述
- 组件的生命周期管理
- Cluster Autoscaler 说明
- OOMGuard 说明
- NodeProblemDetectorPlus 说明
- NodeLocalDNSCache 说明
- DNSAutoscaler 说明
- COS-CSI 说明
- CFS-CSI 说明
- CFSTURBO-CSI 说明
- CBS-CSI 说明
- UserGroupAccessControl 说明
- TCR 说明
- TCR Hosts Updater
- DynamicScheduler 说明
- DeScheduler 说明
- Network Policy 说明
- Nginx-ingress 说明
- HPC 说明
- tke-monitor-agent 说明
- tke-log-agent 说明
- GPU-Manager 说明
- 应用管理
- 应用市场
- 网络管理
- 集群运维
- 日志管理
- 备份中心
- 远程终端
- TKE Serverless 集群指南
- TKE 注册集群指南
- TKE Insight
- TKE 调度
- 云原生服务指南
- 实践教程
- 集群
- 集群迁移
- Serverless 集群
- 调度
- 安全
- 服务部署
- 网络
- 发布
- 日志
- 监控
- 运维
- Terraform
- DevOps
- 弹性伸缩
- 容器化
- 微服务
- 成本管理
- 混合云
- 故障处理
- API 文档
- History
- Introduction
- API Category
- Making API Requests
- Elastic Cluster APIs
- Resource Reserved Coupon APIs
- Cluster APIs
- AcquireClusterAdminRole
- CreateClusterEndpoint
- CreateClusterEndpointVip
- DeleteCluster
- DeleteClusterEndpoint
- DeleteClusterEndpointVip
- DescribeAvailableClusterVersion
- DescribeClusterAuthenticationOptions
- DescribeClusterCommonNames
- DescribeClusterEndpointStatus
- DescribeClusterEndpointVipStatus
- DescribeClusterEndpoints
- DescribeClusterKubeconfig
- DescribeClusterLevelAttribute
- DescribeClusterLevelChangeRecords
- DescribeClusterSecurity
- DescribeClusterStatus
- DescribeClusters
- DescribeEdgeAvailableExtraArgs
- DescribeEdgeClusterExtraArgs
- DescribeResourceUsage
- DisableClusterDeletionProtection
- EnableClusterDeletionProtection
- GetClusterLevelPrice
- GetUpgradeInstanceProgress
- ModifyClusterAttribute
- ModifyClusterAuthenticationOptions
- ModifyClusterEndpointSP
- UpgradeClusterInstances
- CreateBackupStorageLocation
- CreateCluster
- DeleteBackupStorageLocation
- DescribeBackupStorageLocations
- DescribeEncryptionStatus
- DisableEncryptionProtection
- EnableEncryptionProtection
- UpdateClusterKubeconfig
- UpdateClusterVersion
- Third-party Node APIs
- Network APIs
- Node APIs
- Node Pool APIs
- TKE Edge Cluster APIs
- CheckEdgeClusterCIDR
- DescribeAvailableTKEEdgeVersion
- DescribeECMInstances
- DescribeEdgeCVMInstances
- DescribeEdgeClusterInstances
- DescribeEdgeClusterUpgradeInfo
- DescribeTKEEdgeClusterStatus
- ForwardTKEEdgeApplicationRequestV3
- DescribeEdgeLogSwitches
- CreateECMInstances
- CreateEdgeCVMInstances
- CreateEdgeLogConfig
- DeleteECMInstances
- DeleteEdgeCVMInstances
- DeleteEdgeClusterInstances
- DeleteTKEEdgeCluster
- DescribeTKEEdgeClusterCredential
- DescribeTKEEdgeExternalKubeconfig
- DescribeTKEEdgeScript
- InstallEdgeLogAgent
- UninstallEdgeLogAgent
- UpdateEdgeClusterVersion
- DescribeTKEEdgeClusters
- CreateTKEEdgeCluster
- Cloud Native Monitoring APIs
- Scaling group APIs
- Super Node APIs
- Add-on APIs
- Other APIs
- Data Types
- Error Codes
- TKE API 2022-05-01
- 常见问题
- 服务协议
- 联系我们
- 词汇表
简介
集群审计是基于 Kubernetes Audit 对 kube-apiserver 产生的可配置策略的 JSON 结构日志的记录存储及检索功能。本功能记录了对 kube-apiserver 的访问事件,会按顺序记录每个用户、管理员或系统组件影响集群的活动。
使用须知
已经创建注册集群,且注册集群的状态为运行中。
目前注册集群的审计日志仅支持投递至 腾讯云日志服务 CLS,暂不支持其他日志消费端。
注册集群开启审计功能,需要用户自行登录集群的 Master 节点配置相关审计策略和 API Server 相关参数。
开启集群审计功能,默认会同步开启集群日志采集功能。
若使用集群审计功能,请确认 Kubernetes 集群内节点能够访问日志消费端。这里我们提供公网和内网两种方式进行日志投递,用户可以根据业务情况自行选择:
公网投递:集群审计日志将通过公网的方式进行投递至日志服务 CLS ,需要集群中的节点具有访问公网的能力。
内网投递:集群审计日志将通过内网的方式进行投递至日志服务 CLS ,需要集群内的节点与腾讯云日志服务 CLS 内网互通。选择该选项前,请 提交工单 进行确认。
使用步骤
在集群 Master 节点上配置审计策略
依次登录集群的所有 Master 节点,配置审计策略文件
/etc/kubernetes/audit-policy.yaml。您可以根据业务的实际情况,按需修改。apiVersion: audit.k8s.io/v1beta1kind: PolicyomitStages:- "RequestReceived"rules:- level: Noneusers: ["system:kube-proxy"]verbs: ["watch"]resources:- group: ""resources: ["endpoints", "services"]- level: Noneusers: ["system:unsecured"]namespaces: ["kube-system"]verbs: ["get"]resources:- group: ""resources: ["configmaps"]- level: Noneusers: ["kubelet"]verbs: ["get"]resources:- group: ""resources: ["nodes"]- level: NoneuserGroups: ["system:nodes"]verbs: ["get"]resources:- group: ""resources: ["nodes"]- level: Noneusers:- system:kube-controller-manager- system:kube-scheduler- system:serviceaccount:kube-system:endpoint-controllerverbs: ["get", "update"]namespaces: ["kube-system"]resources:- group: ""resources: ["endpoints"]- level: Noneusers: ["system:apiserver"]verbs: ["get"]resources:- group: ""resources: ["namespaces"]- level: NonenonResourceURLs:- /healthz*- /version- /swagger*- level: Noneresources:- group: ""resources: ["events"]- level: Metadataresources:- group: "" # coreresources: ["secrets", "configmaps"]- group: authentication.k8s.ioresources: ["tokenreviews"]- level: Requestverbs: ["get", "list", "watch"]resources:- group: ""- group: "admissionregistration.k8s.io"- group: "apps"- group: "authentication.k8s.io"- group: "authorization.k8s.io"- group: "autoscaling"- group: "batch"- group: "certificates.k8s.io"- group: "extensions"- group: "networking.k8s.io"- group: "policy"- group: "rbac.authorization.k8s.io"- group: "settings.k8s.io"- group: "storage.k8s.io"- level: RequestResponseresources:- group: ""- group: "admissionregistration.k8s.io"- group: "apps"- group: "authentication.k8s.io"- group: "authorization.k8s.io"- group: "autoscaling"- group: "batch"- group: "certificates.k8s.io"- group: "extensions"- group: "networking.k8s.io"- group: "policy"- group: "rbac.authorization.k8s.io"- group: "settings.k8s.io"- group: "storage.k8s.io"- level: Metadata
在 Master 节点上配置 API Server 参数
依次登录集群所有的 Master 节点,修改
/etc/kubernetes/manifests/kube-apiserver.yaml文件1. 添加相关 command 参数,内容如下:
spec:containers:- command:- kube-apiserver- --audit-log-maxbackup=10- --audit-log-maxsize=100- --audit-log-path=/var/log/kubernetes/kubernetes.audit- --audit-log-maxage=30- --audit-policy-file=/etc/kubernetes/audit-policy.yaml
2. 添加相关的 Volume 参数,将 /etc/kubernetes/audit-policy.yaml 挂载到 API Server Pod,内容如下:
spec:containers:- command:- kube-apiserver- --audit-log-maxbackup=10- --audit-log-maxsize=100- --audit-log-path=/var/log/kubernetes/kubernetes.audit- --audit-log-maxage=30- --audit-policy-file=/etc/kubernetes/audit-policy.yaml......volumeMounts:- mountPath: /var/log/kubernetesname: k8s-audit- mountPath: /etc/kubernetes/audit-policy.yamlname: audit-policyreadOnly: true......volumes:- hostPath:path: /var/log/kubernetestype: DirectoryOrCreatename: k8s-audit- hostPath:path: /etc/kubernetes/audit-policy.yamltype: FileOrCreatename: audit-policy...
开启集群审计
1. 登录 腾讯云容器服务控制台 ,选择左侧导航中的运维功能管理。
2. 在功能管理页面上方选择地域和注册集群,单击希望开启集群审计的集群右侧的设置。如下图所示:
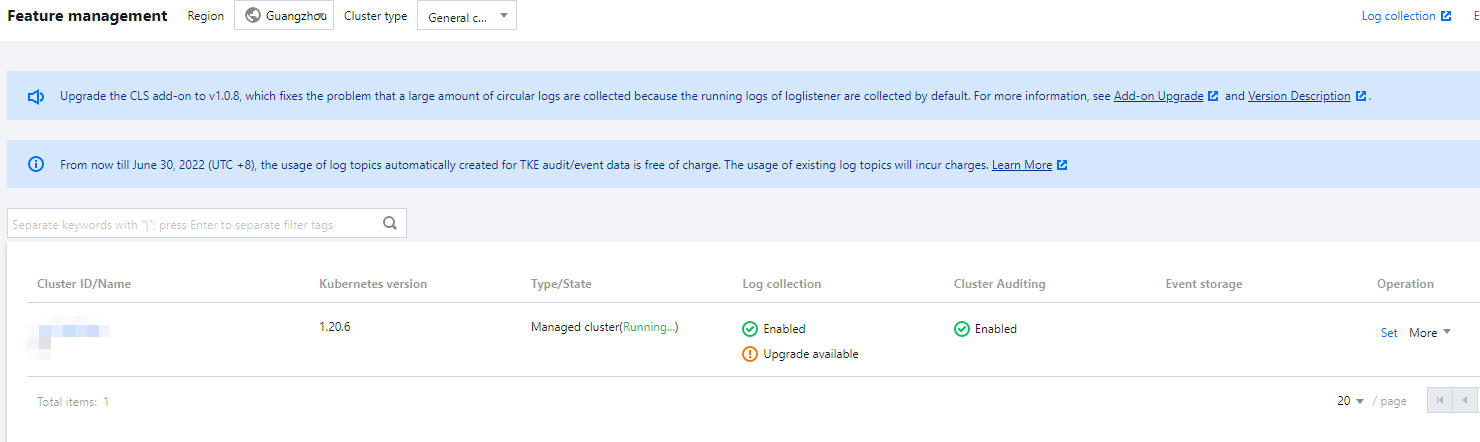

3. 在弹出的“设置功能”窗口,单击“集群审计”功能右侧的编辑。
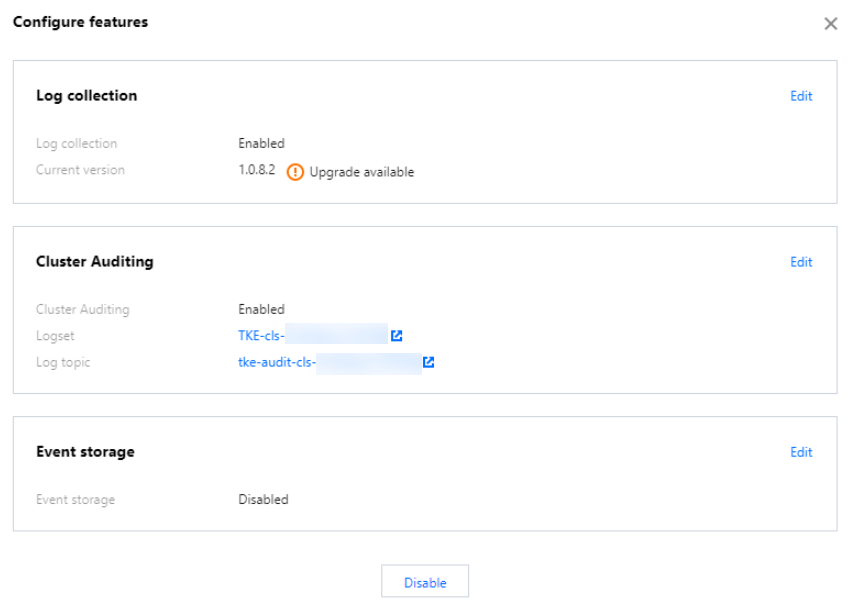

4. 勾选开启集群审计,选择投递方式和存储审计日志的日志集、日志主题,推荐选择自动创建日志主题。
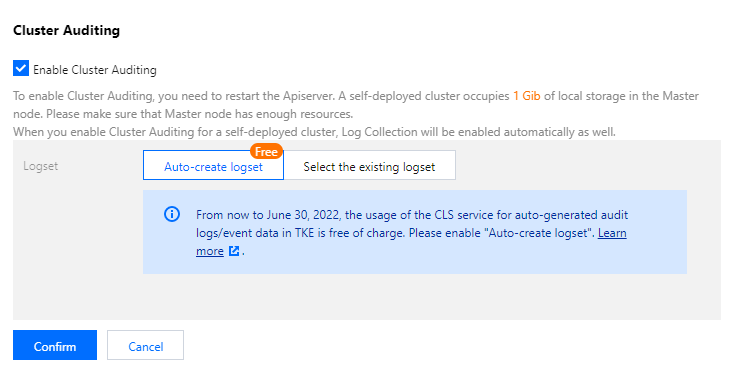

5. 单击确定即可开启注册集群审计功能。
审计仪表盘
容器服务为用户提供了开箱即用的审计仪表盘。在集群开启集群审计功能后,TKE 将自动为该集群配置审计总览、节点操作总览、K8S 对象操作概览、聚合检索仪表盘。还支持用户自定义配置过滤项,同时内置 CLS 的全局检索,方便用户观测和检索各类集群操作,以便于及时发现和定位问题。更多详细介绍,请参考 审计仪表盘。

 是
是
 否
否
本页内容是否解决了您的问题?