Tencent Kubernetes Engine
- Release Notes and Announcements
- Release Notes
- Announcements
- Security Vulnerability Fix Description
- Release Notes
- Kubernetes Version Maintenance
- Runtime Version Maintenance Description
- Product Introduction
- Quick Start
- TKE General Cluster Guide
- Purchase a TKE General Cluster
- Permission Management
- Controlling TKE cluster-level permissions
- TKE Kubernetes Object-level Permission Control
- Cluster Management
- Images
- Worker node introduction
- Normal Node Management
- Native Node Management
- Purchasing Native Nodes
- Supernode management
- Purchasing a Super Node
- Registered Node Management
- Memory Compression Instructions
- GPU Share
- qGPU Online/Offline Hybrid Deployment
- Kubernetes Object Management
- Workload
- Configuration
- Auto Scaling
- Service Management
- Ingress Management
- CLB Type Ingress
- API Gateway Type Ingress
- Storage Management
- Use File to Store CFS
- Use Cloud Disk CBS
- Add-On Management
- CBS-CSI Description
- Network Management
- GlobalRouter Mode
- VPC-CNI Mode
- Static IP Address Mode Instructions
- Cilium-Overlay Mode
- OPS Center
- Audit Management
- Event Management
- Monitoring Management
- Log Management
- Using CRD to Configure Log Collection
- Backup Center
- TKE Serverless Cluster Guide
- Purchasing a TKE Serverless Cluster
- TKE Serverless Cluster Management
- Super Node Management
- Kubernetes Object Management
- OPS Center
- Log Collection
- Using a CRD to Configure Log Collection
- Audit Management
- Event Management
- TKE Registered Cluster Guide
- Registered Cluster Management
- Ops Guide
- TKE Insight
- TKE Scheduling
- Job Scheduling
- Native Node Dedicated Scheduler
- Cloud Native Service Guide
- Cloud Service for etcd
- Version Maintenance
- Cluster Troubleshooting
- Practical Tutorial
- Cluster
- Serverless Cluster
- Mastering Deep Learning in Serverless Cluster
- Scheduling
- Security
- Service Deployment
- Proper Use of Node Resources
- Network
- DNS
- Self-Built Nginx Ingress Practice Tutorial
- Logs
- Monitoring
- OPS
- DevOps
- Construction and Deployment of Jenkins Public Network Framework Appications based on TKE
- Auto Scaling
- KEDA
- Containerization
- Microservice
- Cost Management
- Hybrid Cloud
- Fault Handling
- Pod Status Exception and Handling
- Pod exception troubleshooter
- API Documentation
- Making API Requests
- Elastic Cluster APIs
- Resource Reserved Coupon APIs
- Cluster APIs
- Third-party Node APIs
- Network APIs
- Node APIs
- Node Pool APIs
- TKE Edge Cluster APIs
- Cloud Native Monitoring APIs
- Super Node APIs
- TKE API 2022-05-01
- Making API Requests
- Node Pool APIs
- FAQs
- TKE General Cluster
- TKE Serverless Cluster
- About OPS
- Service Agreement
- User Guide(Old)
Common Service & Ingress Errors and Solutions
Last updated: 2024-08-09 10:23:41
Kubernetes manages resources declaratively. Declarative APIs only require declaring a desired state, to make the system adjust itself to suit the state. However, declarative APIs also introduce new problems: inability to perceive the current state information of resources and insufficient understanding of task processes.
To ensure the consistency of CLB instance configuration information, the entire Service/Ingress is synchronized as a whole resource. If there is any listener-level configuration error in a CLB-type Service/Ingress, it will cause the entire CLB synchronization to fail, and the problem will be reported as an Event for the user to handle. When Resource synchronization is correct, there will also be an Event update indicating the resource has been successfully synchronized.
As the Service/Ingress resource offers services directly to users, any exception can lead to service unavailability, affecting service quality. This document describes the common causes of Service/Ingress errors and solutions.
How to View the Error Messages of Service/Ingress Events?
1. Log in to the Tencent Kubernetes Engine console, and select Cluster in the left sidebar.
2. On the Cluster Management page, select the cluster ID for which you need to update the YAML to go to the page of basic cluster information.
3. Select Service and Routing > Service or Ingress to go to the Service or Ingress information page.
4. Click a specific Service or Ingress name.
5. On the Event tab, you can view the event information of the current Service or Ingress. As shown below, you can view the Event error code of the current Service/Ingress.
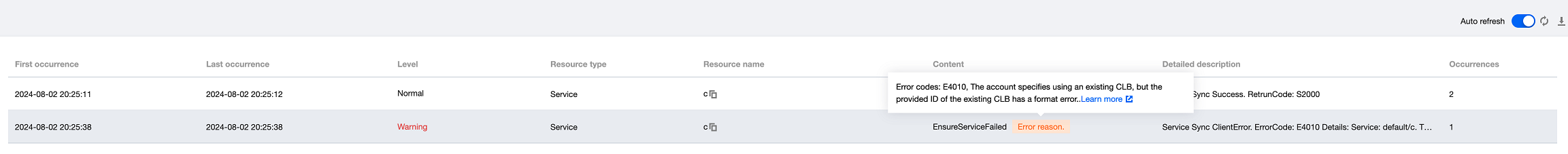
Note:
Only resource events that occurred within the last 1 hour are saved. Check them as soon as possible.
Obtain the Ingress resource exception list and error message:
kubectl get event | grep ingress
Obtain the Service resource exception list and error message:
kubectl get event | grep service
Causes of Service Event Errors and Solutions
Error Code | Description | Solutions | Potential Risk if not Corrected |
E4001 | TKE_QCSRoles authorization | Log in to the CAM console, check TKE service account authorization, and re-add authorization. For details, see the description of role permissions related to service authorization. | In the cluster dimension, components cannot operate properly. |
E4004 | The number of CLBs exceeds the upper limit. | Submit a ticket to apply for a CLB quota. | New resources have no traffic access. |
E4005 | There is an error in created CLB parameters. | Check the created parameters: service.kubernetes.io/service.extensiveParameters. For details, see the description of service annotation. | New resources have no traffic access. |
E4008 | Insufficient subnet IPs | Three solutions: 1. Replace the subnet with another subnet with enough IPs and create a subnet. 2. Update the Service annotation and use a new subnet ID. 3. Use the public network type CLB instead. | New resources have no traffic access. |
E4009 | Overdue payment | You need to top up your account. | New resources have no traffic access. |
E4011 | An existing CLB does not exist. | Log in to the CLB console, find the CLB instance under the same VPC as the current cluster, confirm the CLB ID, and use a real and valid CLB ID. For details, see the use of an existing CLB in a Service. | New resources have no traffic access. |
E4012 | An existing CLB is a resource managed by another TKE. | An existing CLB must have been created by the user on the CLB console. For details, see the use of an existing CLB in a Service. | New resources have no traffic access. |
E4013 | An existing CLB is a resource used by another cluster. | The cross-cluster use of a CLB is not supported. Use another CLB or delete this resource. For details, see the sharing of a CLB by multiple Services. | New resources have no traffic access. |
E4014 | An existing CLB has a port conflict. | Multiple Service declarations use the same port. Modify the port declaration of the Service with an error, and use another port to avoid the conflict. For details, see the use of an existing CLB in a Service. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4016 | The user has not enabled the sharing feature. | Apply to enable Services' sharing capability. For details, see the sharing of a CLB by multiple Services. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4026 | The external configuration fails to be found. | The user configuration is not blocked. For details, see the Service CLB configuration. There are two solutions: 1. Delete the external configuration feature in the Service. 2. Add a TkeServiceConfig resource with the corresponding name to the annotation. | N/A |
E4033 | Direct connection is enabled, but no workload backend supports direct access. | Use the ENI network mode for the workload, and disable HostNetwork. Delete the direct connection annotation, and use NodePort for access. For instructions on using direct Service connection, see the use of LoadBalancer to directly connect a Service in Pod mode. | Backend updates may fail, causing possible interruption during the user's rolling updates. |
E4036 | Backend quadruplet conflict | The quadruplet, including CLB VIP, listener protocol, backend IP and backend port, must remain unique. With CLB restrictions, the user needs to listen to multiple ports on the Pod and bind them separately to solve this problem. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4037 | The subnet does not exist. | Three solutions: 1. Replace the subnet with another subnet with enough IPs and create a subnet. 2. Update the Service annotation and use a new subnet ID. 3. Use the public network type CLB instead. | New resources have no traffic access. |
E4062 | The certificate has expired. | Add a new certificate to the certificate service and update the Secret resource content declared in the extension protocol annotation. Fill in the certificate ID according to the document format. For details, see the Service extension protocol. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4075 | In the cross-regional feature, the region ID is incorrect. | Check the cross-regional annotation in the Service. For the region ID, see the regions and availability zones. | New resources have no traffic access. |
Causes of Ingress Event Errors and Solutions
Error Code | Description | Solutions | Potential Risk if not Corrected |
E4003 | The number of CLBs has reached the upper limit. | Submit a ticket to apply for a CLB quota. | New resources have no traffic access. |
E4005 | The number of forwarding rules has reached the upper limit. | Submit a ticket to apply for a CLB quota. | New resources have no traffic access. |
E4008 | The TKE_QCSRole authorization has been deleted | Log in to the CAM console, check TKE service account authorization, and re-add authorization. For details, see the description of role permissions related to service authorization. | In the cluster dimension, components cannot operate properly. |
E4009 | The Secret name is not configured in the TLS field. | If you need the forwarding rules of the HTTPS protocol, modify the TLS field in the Ingress and configure the certificate required for the HTTPS listener. For details, see the Ingress certificate configuration. If you do not need the forwarding rules of the HTTPS protocol, delete the TLS field and use the HTTP protocol for service exposure. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4010 | The Secret configured in the TLS field cannot be found. | Create the Secret resource declared in the Ingress, and fill in the certificate ID according to the document format. For details, see the Ingress certificate configuration. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4011 | The Secret content configured in the TLS field is erroneous, with no certificate ID. | Update the Secret resource content declared in the TLS, and fill in the certificate ID according to the document format. For details, see the Ingress certificate configuration. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4012 | Abnormal certificate status | Add a new certificate to the certificate service and update the Secret resource content declared in TLS. Fill in the certificate ID according to the document format. For details, see the Ingress certificate configuration. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4018 | The specified existing CLB does not exist. | Go to the CLB console to find the CLB instance under the same VPC as the current cluster, confirm the CLB ID, and use a real and valid CLB ID. For details, see the use of an existing CLB in an Ingress. | New resources have no traffic access. |
E4019 | The specified existing CLB has been created by TKE. | The existing CLB must have been created by the user on the CLB Console. For details, see the use of an existing CLB in an Ingress. | New resources have no traffic access. |
E4020 | The specified existing CLB is used by another Ingress | The existing CLB must have been created by the user on the CLB Console. For details, see the use of an existing CLB in an Ingress. | New resources have no traffic access. |
E4021 | The specified existing CLB listener has not been emptied. | Log in to the CLB console, and remove all listeners of this CLB. | New resources have no traffic access. |
E4022 | The annotation format of kubernetes.io/ingress.http-rules is incorrect. | Refer to the description of Ingress annotations to confirm if the annotation content is valid. It is recommended to use the console to update the resources. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4023 | The annotation format of kubernetes.io/ingress.https-rules is incorrect. | Refer to the description of Ingress annotations to confirm if the annotation content is valid. It is recommended to use the console to update the resources. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4027 | Overdue payment for account | You need to top up your account. | New resources have no traffic access. |
E4031 | Forwarding rules contain invalid characters. | Modify the Rule field of forwarding rules. The CLB forwarding path does not support regular expressions. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4034 | The Host field of the IPv6 CLB is not declared. (Host is not required for IPv4, and it is VIP by default, which is not supported by IPv6) | Complete all Host fields in the Ingress, with no blank left. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4035 | Incorrect certificate ID format | Update the Secret resource content declared in TLS, and fill in the certificate ID according to the document format. For details, see the Ingress certificate configuration. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4039 | The certificate has expired. | Add a new certificate to the certificate service and update the Secret resource content declared in TLS. Fill in the certificate ID according to the document format. For details, see the renewal of a TKE Ingress certificate. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4040 | The Ingress contains a domain name with the corresponding certificate not declared. | Modify the TLS field and configure the certificate required for the HTTPS listener. For details, see the Ingress certificate configuration. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4041 | The Service specified by forwarding rules in the Ingress does not exist. | If your Service indeed does not exist, you need to delete the forwarding rules in the Ingress that use the Service. If you need to use the Service, create a Service resource with the same name in the namespace as the Ingress. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4042 | The Service specified by forwarding rules in the Ingress does not have a corresponding forwarding port. | If your Service does not have such a port, you need to delete the forwarding rules in the Ingress that use the Service. If the problem involves port configuration, a port update is required. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4043 | The TkeServiceConfig resource specified in the Ingress does not exist. | Does not block user configuration. For details, see the use of TKEServiceConfig to configure CLBs in an Ingress. There are two solutions: delete the external configuration feature annotation in the Service, and add the TKEServiceConfig resource with the corresponding name. | N/A |
E4044 | Invalid kubernetes.io/ingress.rule-mix value | Change it to true or false. For details, see the mixed use of HTTP and HTTPS protocols in an Ingress. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4046 | Resource bandwidth annotation configuration error, format error or bandwidth range error | Valid bandwidth values: 1-2048 | New resources have no traffic access. |
E4047 | In the Ingress, the Service specified by forwarding rules is of the ClusterIP type and has no forwarding port access. | Modify the Service with an error to the NodePort type. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4048 | The Ingress contains a domain name with multiple default certificates declared. | Multiple Secrets with no Host configuration are declared in the TLS field. Delete them until only one remains. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4049 | The Ingress contains a fixed domain name with multiple certificates declared. | Multiple Secrets are declared for a domain in the TLS field. Delete them until only one remains. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4051 | The configuration generated automatically by the system is specified for the user's manual external configuration. | For details, see the use of TKEServiceConfig to configure CLBs in an Ingress. Use a resource with a different name instead. | N/A |
E4052 | The domain name specified by forwarding rules in the Ingress does not meet the regular expression requirements. | Check and correct the erroneous domain name. Common errors include domain names without a ''.'', such as Host: test, and domain names with any uppercase letter, such as Host: Test.com. Regular expression: (\\*|[a-z0-9]([-a-z0-9]*[a-z0-9])?)(\\.[a-z0-9]([-a-z0-9]*[a-z0-9])?)+ | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4053 | Unable to create a CLB due to the exhaustion of subnet IPs | Three solutions: 1. Replace the subnet with another subnet with enough IPs and create a subnet. 2. Update the Service annotation and use a new subnet ID. 3. Use the public network type CLB instead. | New resources have no traffic access. |
E4054 | The number of backends has reached the upper limit. | Submit a ticket to apply for a CLB backend quota. | Backend updates may fail, causing possible interruption during the user's rolling updates. |
E4055 | Unable to create a CLB due to the absence of the subnet or a format error | Three solutions: 1. Replace the subnet with another subnet with enough IPs and create a subnet. 2. Update the Service annotation and use a new subnet ID. 3. Use the public network type CLB instead. | New resources have no traffic access. |
E4060 | Unable to enable the SNAT Pro feature for the user due to no granting of allowlist authorization to the account | Submit a ticket to apply for the granting of allowlist authorization to enable the SNAT Pro capability for the CLB. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4066 | The cluster initialization failed, and CRD cannot be created. | In the cluster dimension, components cannot operate properly. | |
E4068 | The automatic redirection rules conflict with other user-declared rules. | When the automatic redirection feature is used, it is recommended not to declare other forwarding rules. For details, see the Ingress redirection. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4071 | Cross-regional configuration error: the CLB's VPC and the current cluster's VPC are not in the same CCN. | Use the CCN to associate two VPCs and replace VPCs in other CCNs. For details, see the cross-regional binding for an Ingress. | New resources have no traffic access. |
E4074 | Overdue payment for a node may cause backend binding failure. | The CLB's backend binding problem may be due to node blockage. | Backend updates may fail, causing possible interruption during the user's rolling updates. |
E4081 | The annotation format of kubernetes.io/ingress.https-rules is incorrect (configuration conflict). | It is recommended to modify the configuration through the console. For details, see the description of Ingress annotations. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4082 | The NoSelector Service does not support binding. In direct connection scenarios, the Ingress declares the use of similar resources. | The backend of the NoSelector Service does not support direct access, so NodePort needs to be used instead. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4084 | Under cross-regional binding solution 1.0, the SNAT Pro feature cannot be used. | The technical solution needs to be adjusted due to system limitations. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
E4098 | The CLB ID format of the specified existing CLB is incorrect. | Log in to the CLB console, find the CLB instance under the same VPC as the current cluster, confirm the CLB ID, and use a real and valid CLB ID. For details, see the use of an existing CLB in an Ingress. | New resources have no traffic access. |
E4101 | The listener of the specified existing CLB has a conflict. | Check if port 80/443 is already occupied by other resources. | Resource synchronization is blocked. The user's update may cause the CLB backend to fail to be updated properly. |
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

