Tencent Cloud EdgeOne
- Release Notes and Announcements
- Security Announcement
- Announcements
- Product Introduction
- Purchase Guide
- Billing Items
- Basic Service Fees
- Value-added Service Fees
- Instructions for overdue and refunds
- Getting Started
- Domain Service&Origin Configuration
- Domain Service
- Hosting DNS Records
- Domain Connection
- Traffic Scheduling
- HTTPS Certificate
- HTTPS Configuration
- SSL/TLS Security Configuration
- Origin Configuration
- Load Balancing
- Related References
- Origin-pull configuration
- Related References
- Site Acceleration
- Access Control
- Cache Configuration
- EdgeOne Cache Rules
- Cache Configuration
- Clear and Preheat Cach
- File Optimization
- Network Optimization
- HTTP/3(QUIC)
- QUIC SDK
- Modifying Header
- Modify the response content
- Rule Engine
- Related References
- Request and Response Actions
- DDoS & Web Protection
- DDoS Protection
- Configuration of Exclusive DDoS protection Rules
- Related References
- Web Protection
- Rate Limiting
- Bot Management
- Related References
- Related References
- Image&Video Processing
- Edge Functions
- Runtime APIs
- Streams
- Images
- Sample Functions
- Best Practices
- L4 Proxy
- Obtaining Real Client IPs
- Obtaining Real Client IPs Through Protocol V1/V2
- Data Analysis&Log Service
- Log Service
- Real-time Logs
- Data Analysis
- Alarm Service
- Version Management
- Site and Billing Management
- Site Management
- General Policy
- Terraform
- Practical Tutorial
- Automatic Warm-up/Cache Purge
- Resource Abuse/hotlinking Protection Practical
- HTTPS Related Practices
- Acceleration Optimization
- Scheduling Traffic
- Origin-pull Based On User IP/geolocation
- APK Dynamic Packaging
- Data Analysis and Alerting
- API Documentation
- Making API Requests
- Site APIs
- Acceleration Domain Management APIs
- Site Acceleration Configuration APIs
- Edge Function APIs
- Alias Domain APIs
- Security Configuration APIs
- Layer 4 Application Proxy APIs
- Content Management APIs
- Data Analysis APIs
- Log Service APIs
- Billing APIs
- Certificate APIs
- Load Balancing APIs
- Diagnostic Tool APIs
- Custom Response Page APIs
- DNS Record APIs
- Content Identifier APIs
- Old Version APIs
- Version Management APIs
- Common Guidelines
- FAQs
- Troubleshooting
- Tool Guide
- Speed Test Tools
- Diagnostic Tool
- Agreements
DocumentationTencent Cloud EdgeOneDDoS & Web ProtectionWeb ProtectionBot ManagementClient Reputation
Client Reputation
Last updated: 2024-08-26 09:38:50
Overview
Malicious bots usually initiate requests through proxy pools, botnets, or specific devices. EdgeOne's client reputation analysis uses Tencent's nearly 20 years of network security experience and big data intelligence accumulation to determine the real-time state of IP, adopt scoring mechanisms, quantify risk values, and precisely identify access from malicious dynamic IPs. It accurately identifies high-risk clients, updates the latest threat intelligence every 24 hours, and provides threat confidence reports for different IP addresses. According to the different types of attack clients, it provides 5 risk classifications and confidence levels. You can help control multiple categories (network attack sources, exploited network proxy devices, vulnerability scanning tools, brute force cracking behaviors, etc.) of high-risk client access by customizing the protection strategy for each threat confidence level, reducing business risks and effectively intercepting such malicious behaviors.
Example Scenario
In the Web security analysis module, you observe that under the site
api.example.com, the login interface /api/login has high-frequency access, and there are a large number of failed access requests in a short period of time. However, due to the large number of access IPs, mainly from broadband operator networks, a single IP request is only 1-2 times. Judging from the access features, it is suspected that dial-up IPs are used for brute force cracking login attempts. To strengthen the security policy, we suggest intercepting higher confidence network proxy clients and setting medium confidence clients to observe.Directions
1. Log in to the EdgeOne console and click Site List in the left sidebar. In the site list, click the target site to enter the site details page.
2. Click Security > Web Security . By default, it is a site-level security policy. Click the Domain-level security policy tab and then click the target domain name such as
shop.example.com , to enter the configuration page for the security policy of the target domain name.3. Locate the Bot Management tab and click Edit under Client reputation to enter the configuration page.
4. Client reputation is classified into network attack, network proxy, scanner, account takeover attack, and malicious bot. For different client types, you can select the corresponding action based on the client credibility level. In this example scenario, dial-up IPs belong to a typical network proxy client. When high-frequency access from dispersed IPs is monitored at the site, you can block high-credibility network proxy clients, and set the action to Monitor for moderate-credibility clients.
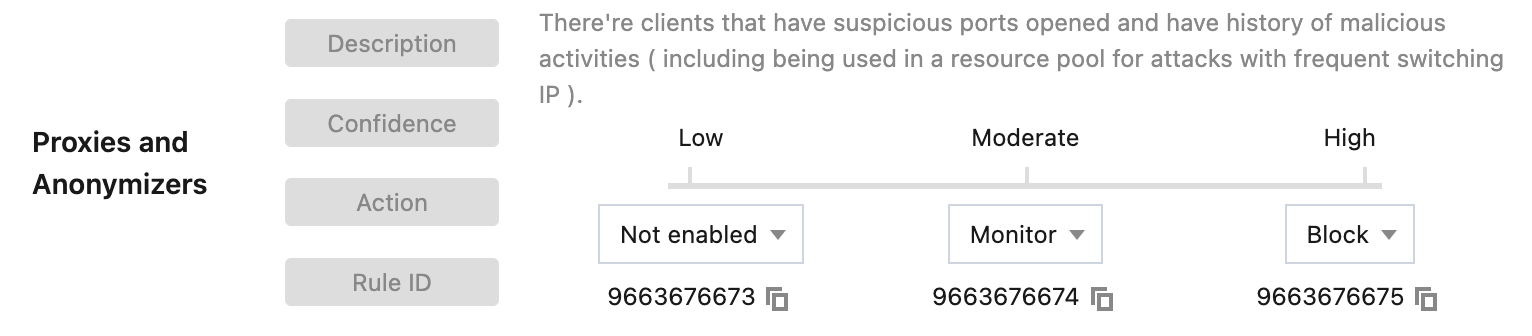
5. Click OK to complete the configuration.
Related References
Risk Classification
Client reputation analysis is based on real-time threat intelligence libraries and can effectively identify clients with the following 5 types of malicious behavior history:
Network attack: Clients with recent attack behavior (such as DDoS, high-frequency malicious requests, site attacks, etc.). For example, attacks initiated by the Mirai botnet can be classified into this category.
Network proxy: Clients that have recently opened suspicious proxy ports and have been used as network proxies, including dial-up IP proxy pools and IoT proxy networks used to initiate malicious requests.
Scanner: Clients with recent scanner behavior targeting known vulnerabilities. For example, vulnerability scanning tools for Web applications.
Account takeover attack: Clients with recent malicious login cracking and account takeover attack behavior. For example, attackers who use brute force to crack user login credentials.
Malicious bot: Clients with recent malicious bot, hotlinking, and brute force cracking behaviors. For example, illegal bots that collect website content.
Credibility Level
For each category of client reputation rules, each credibility level corresponds to a client address list. The credibility level reflects the frequency and consistency of the client address's recent malicious behavior in that category:
Higher credibility: The client address has recently engaged in stable, high-frequency malicious behavior in that category. It is recommended to intercept such clients.
Moderate credibility: The client address has recently engaged in significant frequency malicious behavior in that category. It is recommended to configure such clients for JavaScript challenge or observation.
General credibility: The client address has recently engaged in stable malicious behavior in that category. It is recommended to configure this type of client as an observation, and then adjust it to a JavaScript challenge or a hosting challenge based on the analysis results.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

