Tencent Cloud EdgeOne
- Release Notes and Announcements
- Security Announcement
- Announcements
- Product Introduction
- Purchase Guide
- Billing Items
- Basic Service Fees
- Value-added Service Fees
- Instructions for overdue and refunds
- Getting Started
- Domain Service&Origin Configuration
- Domain Service
- Hosting DNS Records
- Domain Connection
- Traffic Scheduling
- HTTPS Certificate
- HTTPS Configuration
- SSL/TLS Security Configuration
- Origin Configuration
- Load Balancing
- Related References
- Origin-pull configuration
- Related References
- Site Acceleration
- Access Control
- Cache Configuration
- EdgeOne Cache Rules
- Cache Configuration
- Clear and Preheat Cach
- File Optimization
- Network Optimization
- HTTP/3(QUIC)
- QUIC SDK
- Modifying Header
- Modify the response content
- Rule Engine
- Related References
- Request and Response Actions
- DDoS & Web Protection
- DDoS Protection
- Configuration of Exclusive DDoS protection Rules
- Related References
- Web Protection
- Rate Limiting
- Bot Management
- Related References
- Related References
- Image&Video Processing
- Edge Functions
- Runtime APIs
- Streams
- Images
- Sample Functions
- Best Practices
- L4 Proxy
- Obtaining Real Client IPs
- Obtaining Real Client IPs Through Protocol V1/V2
- Data Analysis&Log Service
- Log Service
- Real-time Logs
- Data Analysis
- Related References
- Legacy Console Relevant Documentation
- Security Analysis
- Alarm Service
- Version Management
- Site and Billing Management
- Site Management
- General Policy
- Terraform
- Practical Tutorial
- Automatic Warm-up/Cache Purge
- Resource Abuse/hotlinking Protection Practical
- HTTPS Related Practices
- Acceleration Optimization
- Scheduling Traffic
- Origin-pull Based On User IP/geolocation
- APK Dynamic Packaging
- Data Analysis and Alerting
- API Documentation
- Making API Requests
- Site APIs
- Acceleration Domain Management APIs
- Site Acceleration Configuration APIs
- Edge Function APIs
- Alias Domain APIs
- Security Configuration APIs
- Layer 4 Application Proxy APIs
- Content Management APIs
- Data Analysis APIs
- Log Service APIs
- Billing APIs
- Certificate APIs
- Load Balancing APIs
- Diagnostic Tool APIs
- Custom Response Page APIs
- DNS Record APIs
- Content Identifier APIs
- Old Version APIs
- Version Management APIs
- Common Guidelines
- FAQs
- Troubleshooting
- Tool Guide
- Speed Test Tools
- Diagnostic Tool
- Agreements
DocumentationTencent Cloud EdgeOnePractical TutorialResource Abuse/hotlinking Protection PracticalEdgeOne Hotlink Protection Practical Tutorial
EdgeOne Hotlink Protection Practical Tutorial
Last updated: 2025-03-21 11:51:28
This document describes how to use the hotlink protection capabilities provided by EdgeOne to protect your content against unauthorized hotlinking and improve the security of acceleration services.
Background
Hotlinking refers to other websites or applications directly linking to your resources without your authorization. This behavior can seriously impact your website. First, hotlinking consumes your bandwidth and server resources, causing your website to slow down and even potentially crash the server. Second, hotlinking may lead to your content being misused or spread without authorization, which can seriously damage your brand image and reputation.
To address these issues, EdgeOne provides a range of powerful Hotlink protection capabilities. By using EdgeOne's Hotlink protection feature, you can ensure that only authorized users can access and use your content. You can set an allowlist to permit only specific domain names or IP addresses to access your resources, thereby preventing unauthorized hotlinking. Additionally, you can flexibly configure custom Hotlink protection rules as needed.
With EdgeOne's Hotlink protection capabilities, you can effectively safeguard your content. You can confidently provide high-quality content without worrying about hotlinking and misuse issues. This helps maintain your brand image and reputation while saving bandwidth and server resources, enhancing your website's performance and reliability.
Implementation Method
HTTP response: Implements basic access control such as IP blocklist/allowlist, Referer blocklist/allowlist, UserAgent blocklist/allowlist, and regional access control. For details, see HTTP Response.The issues with this method are:
IP addresses can be forged or hidden, allowing attackers to bypass IP allowlist and blocklist restrictions. They can use proxy servers, Virtual Private Networks (VPN), or other technologies to hide the actual IP address, thereby bypassing access restrictions. This makes IP allowlist and blocklist less reliable in preventing unauthorized access;
The Referer header can also be easily forged. Attackers can bypass Referer allowlist and blocklist restrictions by modifying the Referer field in the HTTP request header. They can use browser plugins, proxy tools, or other technologies to alter the Referer field, making it appear as if it comes from a trusted source, thereby bypassing access restrictions;
The issue with the User-Agent header is similar to the Referer header, as it is also easily forged.
Token authentication: Timestamp hotlink protection, which is more secure and reliable. For details, see Token Authentication.Compared to the basic access control mentioned above, its advantages and issues are as follows:
Prevent link reuse: Each link contains a timestamp parameter. Even if the link is forwarded or shared, once the timestamp expires, others cannot use the link to access the resource.
Difficult to forge: Timestamp Hotlink protection increases the difficulty of hotlinking because attackers need to know the authentication algorithm, authentication key, timestamp format, etc., to construct a URL that can pass verification. These details are hard for attackers to guess or forge.
Client modification required: The use of this feature requires cooperation between the client and EdgeOne. After the client initiates an encrypted URL request, EdgeOne is responsible for Legitimacy Verification of the URL based on predefined rules. Therefore, some additional overhead and complexity need to be considered during implementation.
Edge functions: Customizable hotlink protection capabilities such as remote authentication can be supported through Edge Functions.The advantages and issues of this method are as follows:
High security: Remote authentication can provide higher security. The authentication process is completed by a remote server provided by the customer, rather than the EdgeOne node server, reducing the risk of being compromised by attackers.
Flexibility and scalability: Remote authentication provides greater flexibility and scalability. Customers can flexibly control the authentication logic to adapt to changing business requirements and user access patterns.
Customer modification: Customers need to deploy a remote authentication service and ensure the reliability, security, and performance of the remote server to avoid increased authentication delays, which could affect service quality. Additionally, to handle possible exceptions, an appropriate authentication timeout should be set. Generally, if authentication times out, the request is directly allowed. However, if the authentication service encounters an exception, it may result in illegal requests being allowed, thereby increasing security risk.
Directions
Referer Hotlink Protection
Setting access control rules based on the Referer field in the HTTP request header helps identify and filter visitors, preventing illegal use of website resources. After the Referer blocklist/allowlist is configured, EdgeOne will authenticate requests based on the list, allowing or denying access requests. If the request is allowed, EdgeOne will return the resource link; if denied, EdgeOne will return a 403 response code.
Configuration Samples
For your site
example.com, if you only allow access to the domain business www.example.com with the Referer set to https://www.example.com, and deny other requests directly with a 403 response, you can follow these steps:1. Log in to the EdgeOne console and click Site List in the left sidebar. Subsequently, in the Site List, click the Site you want to configure.
2. On the site details page, click Site Acceleration to enter the global configuration page for the site. Then, click the Rule Engine tab.
3. On the Rule Engine page, click Create rule, and then select Add blank rule.
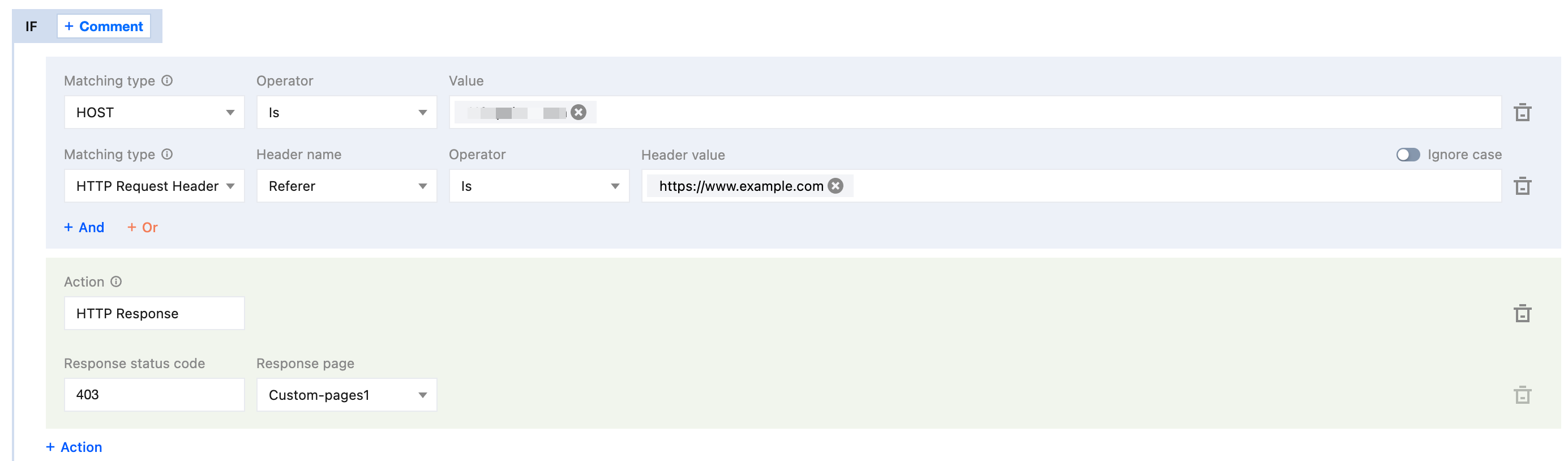
3.1 On the rule editing page, set the matching type to HOST equal to
www.example.com, and set the matching type HTTP Request Header Referer's header value not equal to https://www.example.com.3.2 Click Action, and in the pop-up operation list, select the operation as HTTP Response.
3.3 Configure the response status code as 403. Select the response page from the drop-down list. If no page is available, you need to click Create Page to create one first and then reference it.
4. The complete rule configuration is as demonstrated below. By clicking Save and publish, the rule configuration will be completed.
IP Blocklist/Allowlist
By configuring the IP blocklist/allowlist to filter user requests, you can intercept or allow access from specific IP addresses, effectively limiting access sources and addressing issues such as hotlinking by malicious IP addresses and attacks.
Configuration Samples
For your site
example.com, if you only allow access from client IP addresses within the range of 1.1.2.1 to 1.1.2.254 (including 1.1.2.1 and 1.1.2.254) to the domain business www.example.com, and deny other access directly with a 403 response, you can follow these steps:1. Log in to the EdgeOne console and click Site List in the left sidebar. Subsequently, in the Site List, click the Site you want to configure.
2. On the site details page, click Site Acceleration to enter the global configuration page for the site. Then, click the Rule Engine tab.
3. On the Rule Engine page, click Create rule, and then select Add blank rule.
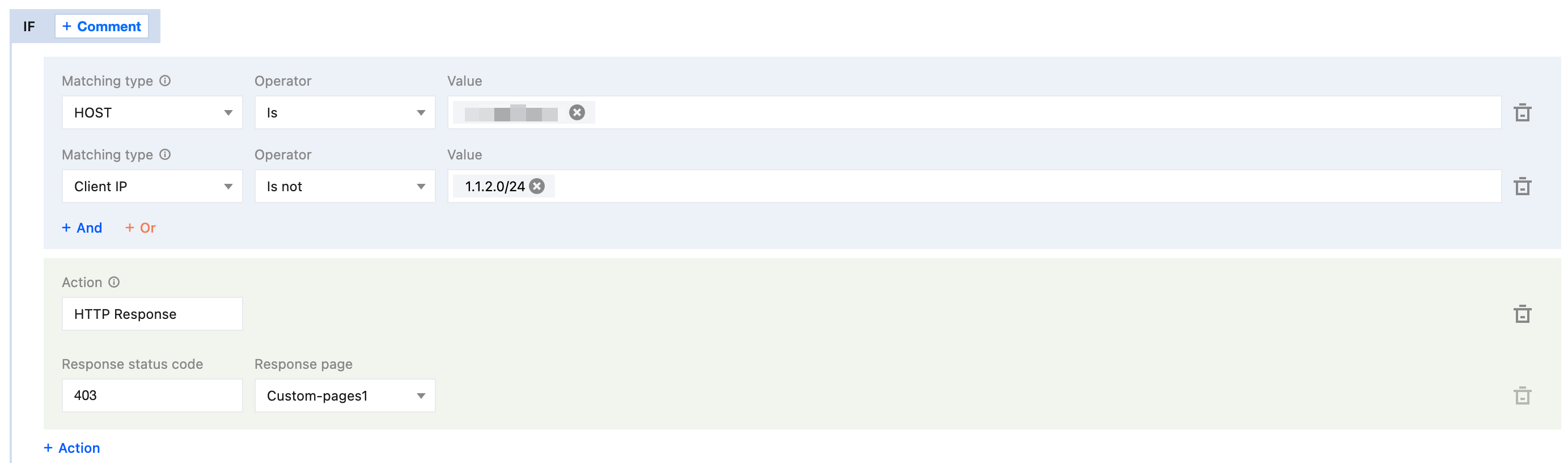
3.1 On the rule editing page, set the matching type to HOST equal to
www.example.com, and set the matching type client IP equal to 1.1.2.0/24.3.2 Click Action, and in the pop-up operation list, select the operation as HTTP Response.
3.3 Configure the response status code as 403. Select the response page from the drop-down list. If no page is available, you need to click Create Page to create one first and then reference it.
4. The complete rule configuration is as demonstrated below. By clicking Save and publish, the rule configuration will be completed.
UserAgent Blocklist/Allowlist
User-Agent is part of the HTTP request header, which identifies the operating system and version and the browser type and version used by the user for accessing. You can configure the User-Agent blocklist/allowlist to restrict the sources of users accessing business resources and enhance the security of acceleration.
Configuration Samples
The domain business
www.example.com under your example.com site is maliciously crawled by Google crawlers, causing a sudden bandwidth increase and severely impacting fees. Through analysis, it was found that the crawler request's User-Agent contains spider. If you want to block such requests, you can follow these steps:1. Log in to the EdgeOne console and click Site List in the left sidebar. Subsequently, in the Site List, click the Site you want to configure.
2. On the site details page, click Site Acceleration to enter the global configuration page for the site. Then, click the Rule Engine tab.
3. On the Rule Engine page, click Create rule, and then select Add blank rule.
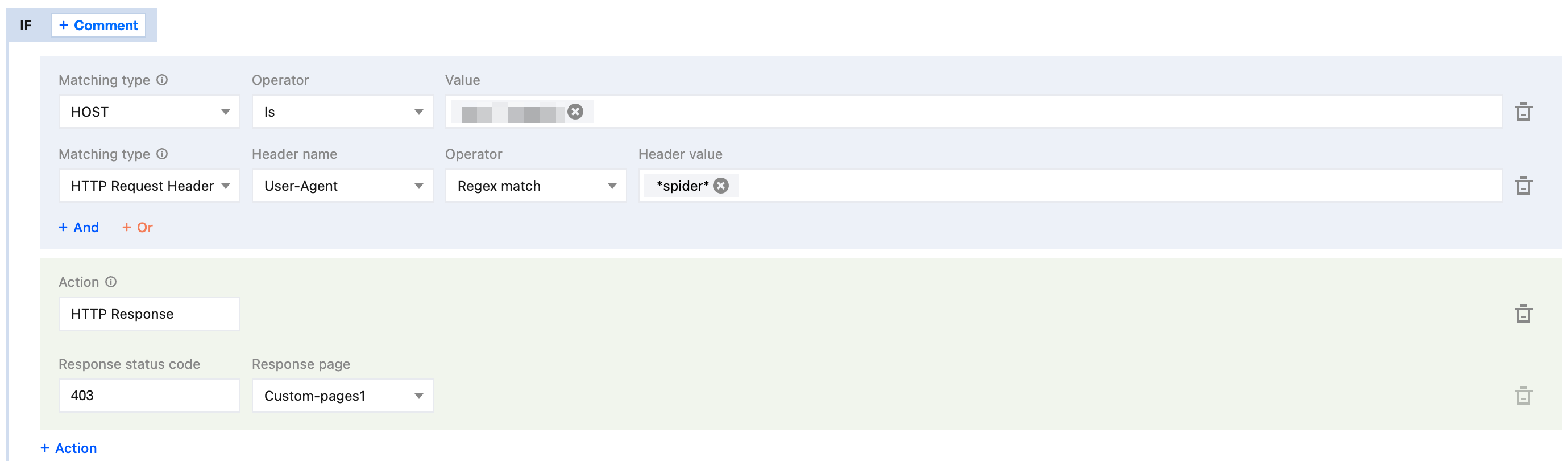
3.1 On the rule editing page, set the matching type to HOST equal to
www.example.com.3.2 Click Action, and in the pop-up operation list, select the operation as HTTP Response, and set the matching type to HTTP Request Header User-Agent with a regular expression match for the header value
*spider*.3.3 Configure the response status code as 403. Select the response page from the drop-down list. If no page is available, you need to click Create Page to create one first and then reference it.
4. The complete rule configuration is as demonstrated below. By clicking Save and publish, the rule configuration will be completed.
Token Authentication
Token authentication is a simple and highly reliable access control policy. By configuring authentication rules for URL access validation, it can effectively prevent malicious hotlinking of site resources. The use of this feature requires cooperation between the client and EdgeOne. The client is responsible for initiating encrypted URL requests, and EdgeOne is responsible for legitimacy verification of the URL based on predefined rules. For detailed configuration and usage, refer to Token Authentication.
Remote Authentication
If you have your own authentication server, you can configure remote authentication to forward user requests to the authentication server you specify. The server then validates the requests. This method is suitable for scenarios requiring precise access control and real-time authentication. EdgeOne can achieve remote authentication capability through edge functions. For sample functions, refer to Remote Authentication.
Was this page helpful?
You can also Contact Sales or Submit a Ticket for help.
Yes
No

